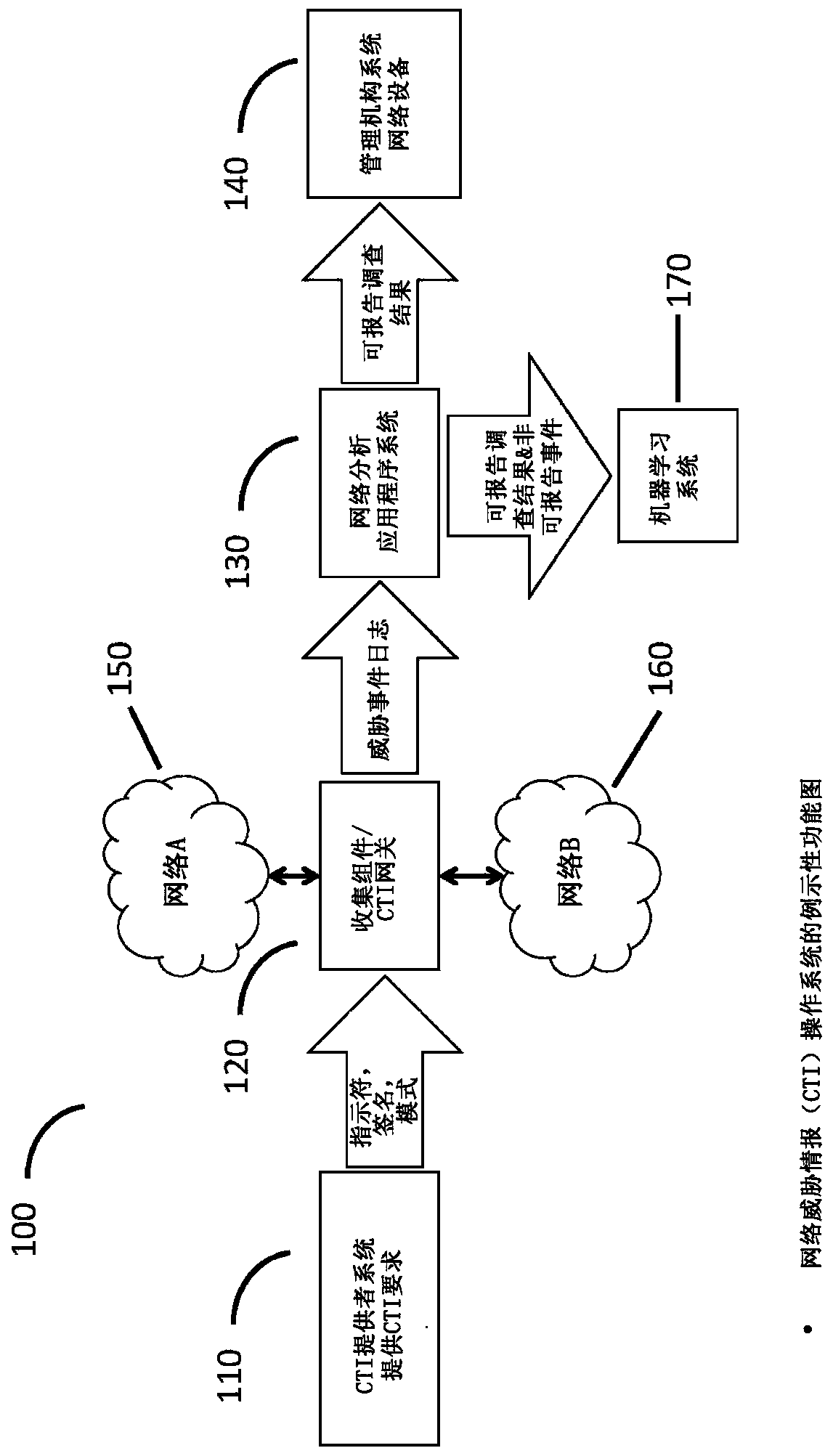
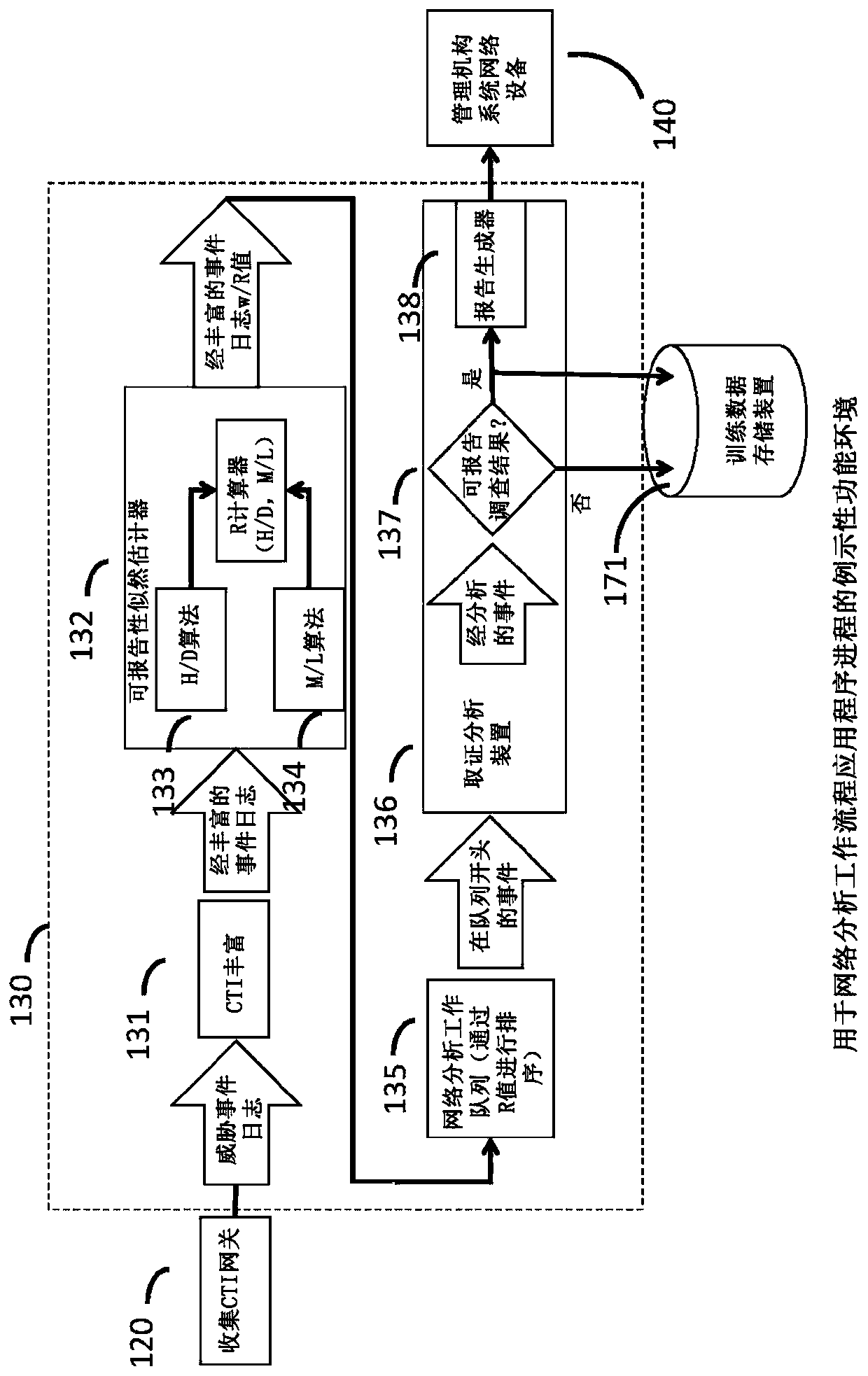
Cyberanalysis workflow acceleration
A technology for analyzing systems and events, applied in machine learning, instrumentation, computing, etc., to solve problems such as overwhelm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In the following description of various exemplary embodiments, reference is made to the accompanying drawings which form a part hereof, and in which is shown by way of illustration various embodiments in which aspects of the disclosure may be practiced. It is to be understood that other embodiments may be utilized and structural and functional modifications may be made without departing from the scope of the present disclosure. In addition, reference is made to specific applications, protocols, and embodiments in which aspects of the present disclosure may be practiced. It is to be understood that other applications, protocols, and embodiments may be utilized and structural and functional modifications may be made without departing from the scope of the present disclosure.
[0032] Various connections between elements are discussed in the following description. These connections are general and unless otherwise indicated they may be direct or indirect, wired or wireles...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com