Event-driving-based fault-tolerant control method under network attack of unmanned surface vehicle
An event-driven, fault-tolerant control technology, applied in the direction of adaptive control, general control system, control/regulation system, etc., can solve the problems of high energy consumption in data transmission and large network bandwidth occupancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0029] Specific implementation mode 1: This implementation mode is based on the event-driven fault-tolerant control method under the network attack of the surface unmanned boat. The specific process is as follows:
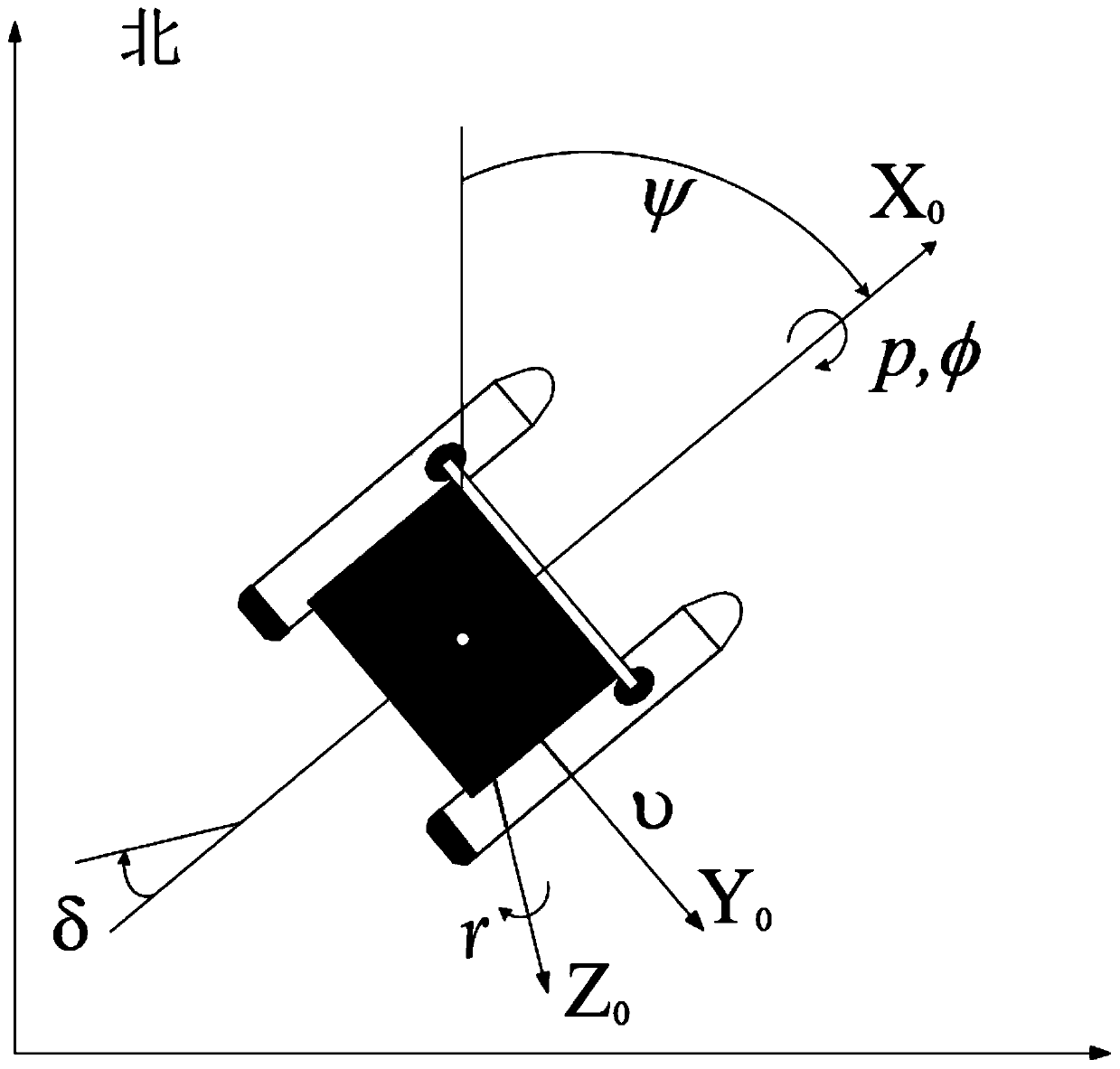
[0030] Step 1. The motion coordinate system of the surface unmanned vehicle is as follows: figure 1 As shown, here we only consider the traversing, swinging and rolling motions of the surface unmanned vehicle.
[0031] According to the kinematic equation of the surface unmanned vehicle, the state space equation (formula 1) of the surface unmanned vehicle system is established;
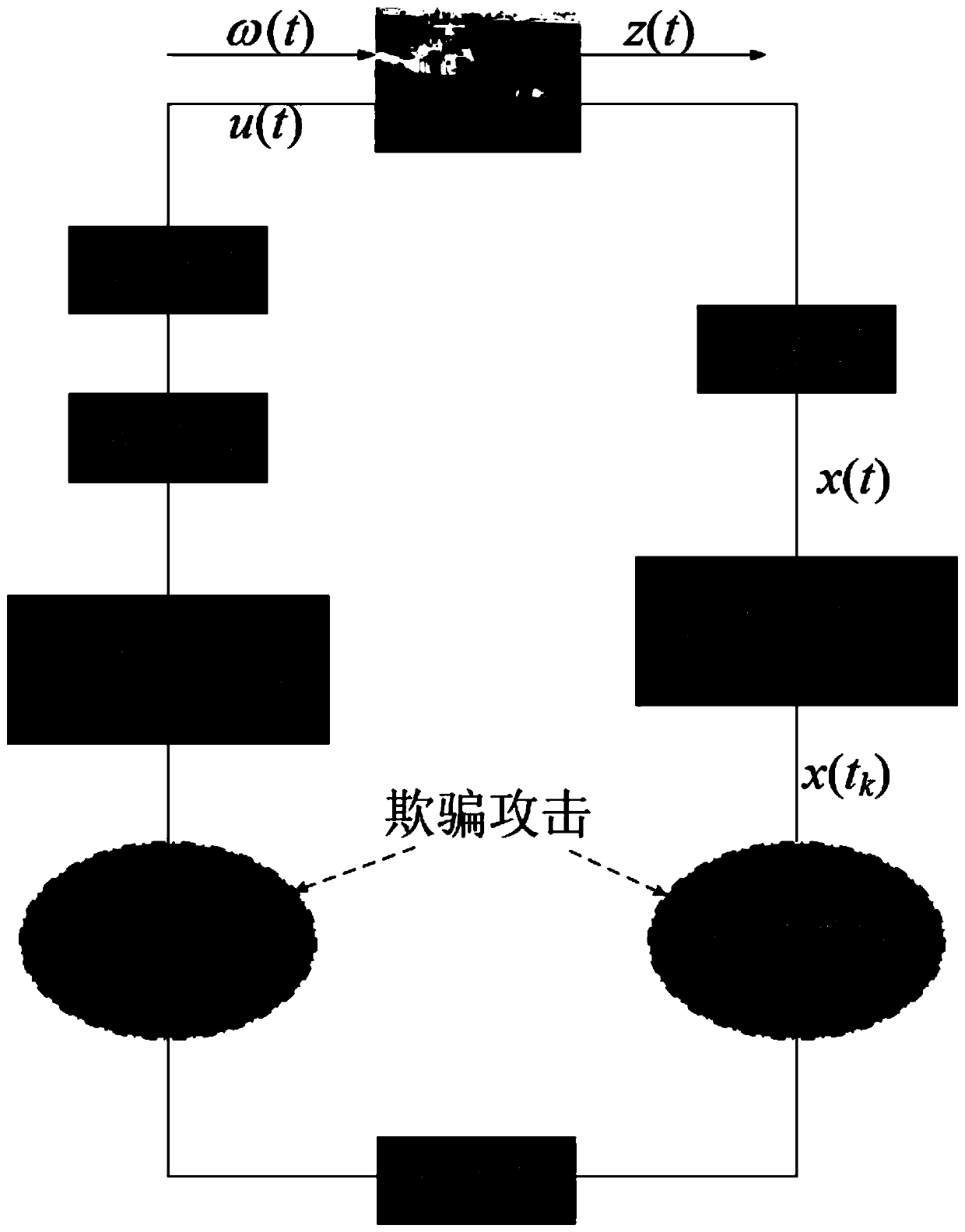
[0032] Step 2. Based on the state space equation of the surface unmanned vehicle system established in step 1, random deception attacks are introduced, and a mathematical model (formula 3) of random deception attacks is established;
[0033] Step 3, based on the mathematical model of random spoofing attack established in step 2, establish the state space equation (formula 5) of the surfac...
specific Embodiment approach 2
[0038] Specific embodiment two: the difference between this embodiment and specific embodiment one is that in the step one, according to the kinematic equation of the surface unmanned vessel, the state space equation of the surface unmanned vessel system is established; the specific process is:
[0039] The motion coordinate system of the surface unmanned vehicle is as follows: figure 1 As shown, the kinematics equation of the surface unmanned vehicle is established, and only the lateral movement, swing and roll motion of the surface unmanned vehicle are considered here;
[0040]
[0041] According to the kinematic equation of the surface unmanned vehicle, the state space equation of the surface unmanned vehicle system is established, and the expression is:
[0042]
[0043] In the formula, x(t)=[υ(t) r(t )ψ(t) p(t) φ(t)] T is the current state of the USV system;
[0044] Among them, υ(t) is the traverse velocity generated by the rudder of the surface unmanned boat, r...
specific Embodiment approach 3
[0060] Specific embodiment three: the difference between this embodiment and specific embodiment one or two is that the system matrix A, B, and E of the surface unmanned vehicle are expressed as follows:
[0061]
[0062] Other steps and parameters are the same as those in Embodiment 1 or 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com