Flow-based abnormal communication behavior detection method and system
An abnormal detection and detection system technology, applied in transmission systems, electrical components, etc., can solve problems such as poor generality, hazards, and insufficient real-time performance, and achieve the effects of strong real-time performance, comprehensive discovery range, and high data processing efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solutions of the present invention will be described below in conjunction with the drawings and embodiments.
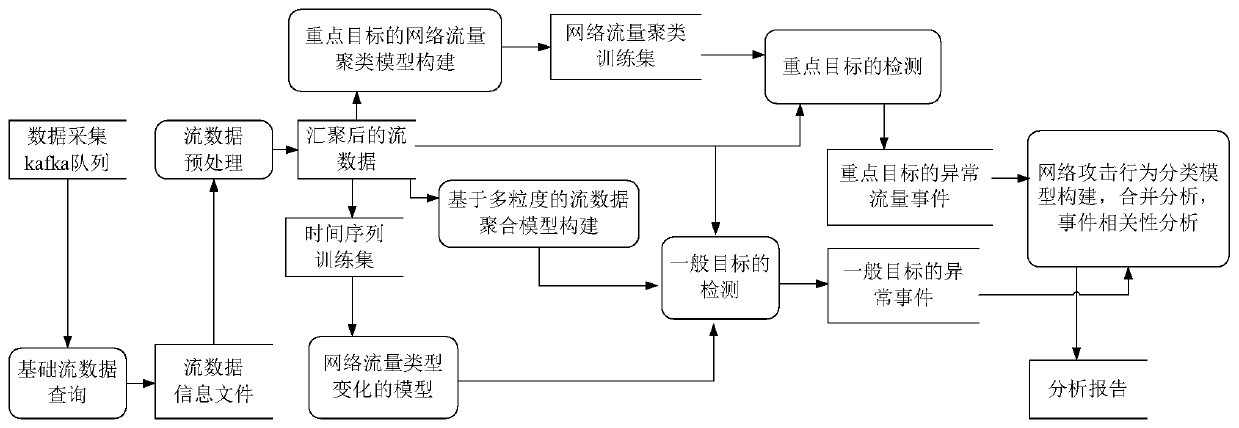
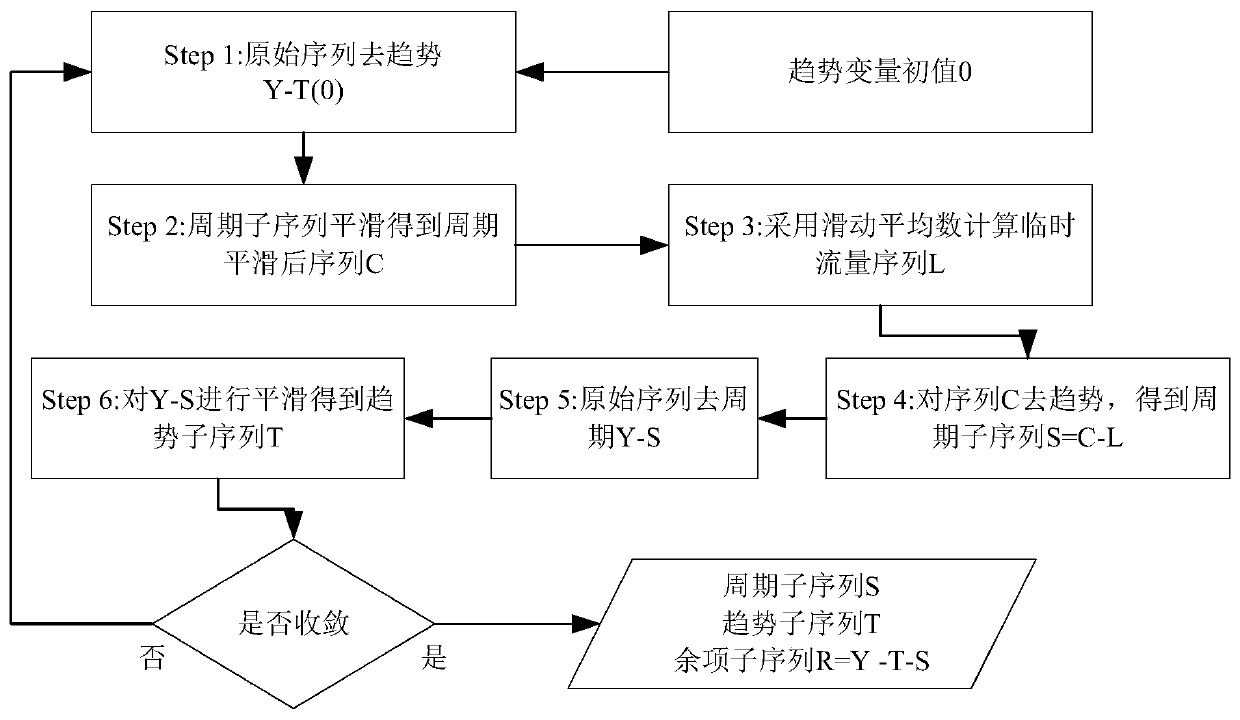
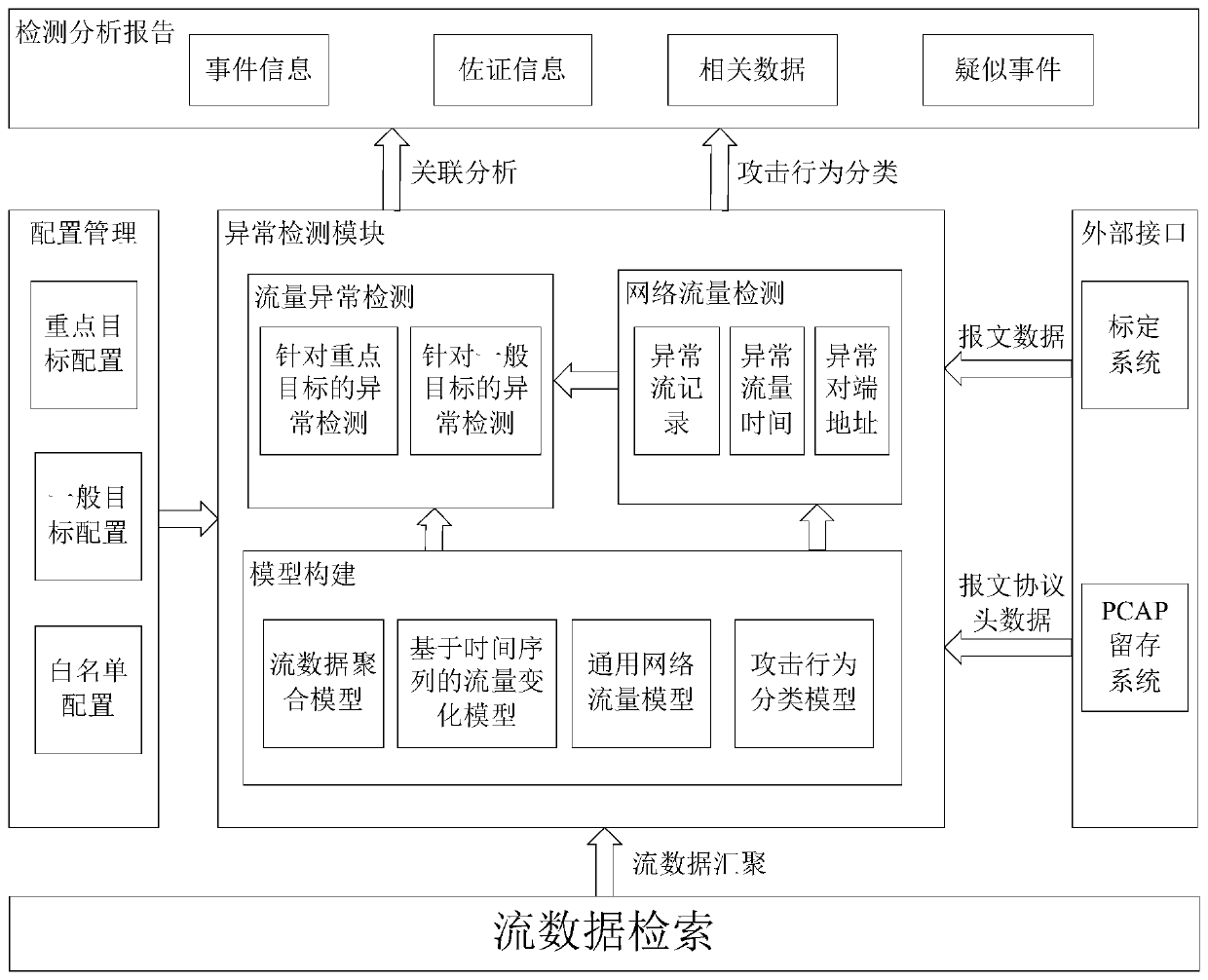
[0042] The purpose of the present invention is to realize the real-time and universal detection of abnormal communication behaviors in the enterprise internal network, so as to quickly discover various abnormalities and maintain the security of the internal network. First of all, the flow-based abnormal communication behavior detection method of the present invention is described, and an implemented business process is as follows figure 1 As shown, the specific implementation steps are described below.
[0043] Step 1: Configure key target IP. The source of key targets consists of two parts: external submission and monitoring and analysis acquisition.
[0044] 1) Based on the key objectives submitted externally. As a fixed part of the key target set, the externally submitted key targets are the main service targets of this system; for the extern...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com