Method and system for updating network threat information
A technology of intelligence information and update method, which is applied in the update field of cyber threat intelligence information, and can solve problems such as the inability to update high-frequency intelligence information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
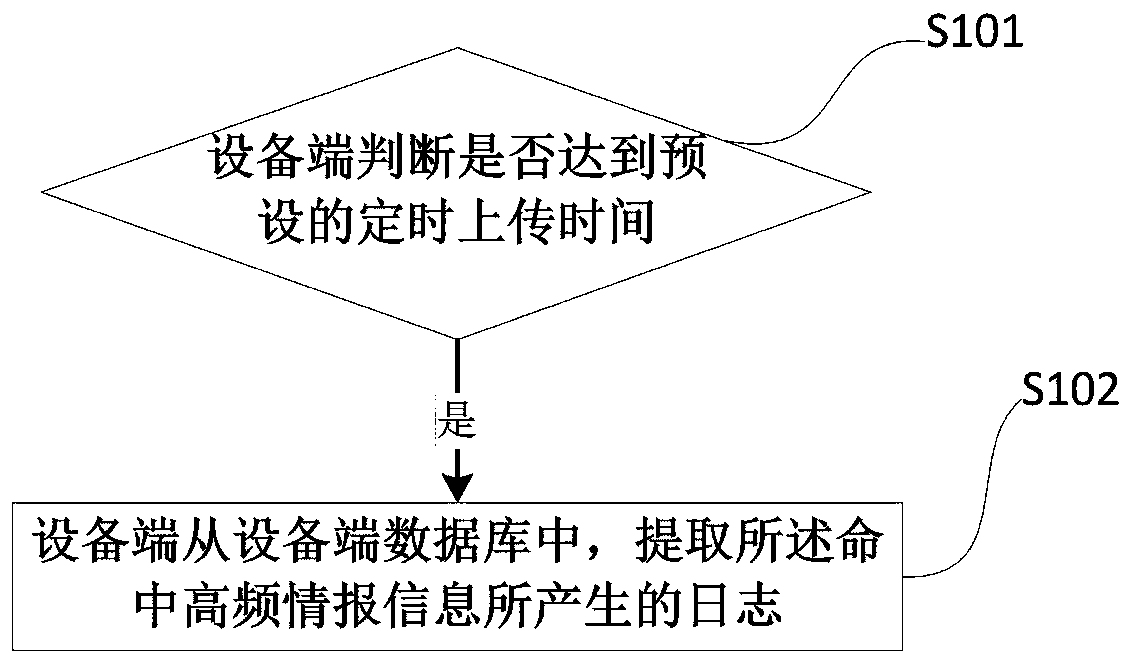
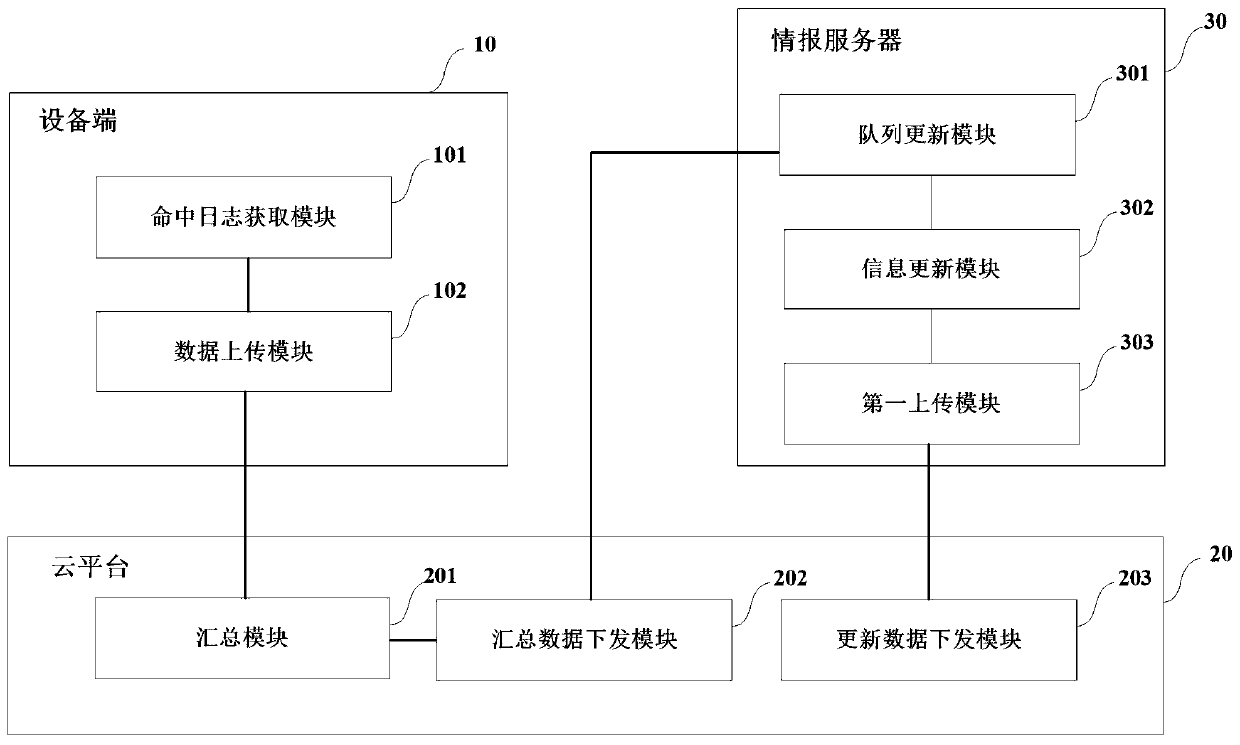
[0044]In order to solve the problem that high-frequency intelligence information cannot be updated in a targeted and timely manner when the number of servers is large, this application discloses a method and system for updating network threat intelligence information through the following embodiments.
[0045] In each embodiment of this application, network threat intelligence information refers to an information set that can help discover threats and deal with threats based on data. Through network threat intelligence information, vulnerabilities can be repaired before attacks occur. Purpose. Open source intelligence services refer to websites or companies that can provide users with data services related to cyber threat intelligence information. Open source intelligence services usually store the latest intelligence information. The hit log refers to the record generated by the hit intelligence information when the device is running. Each hit log records the time, user and a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com