Automatic malicious code behavior analysis system
An automatic analysis system and malicious code technology, which is applied in the field of automatic malicious code behavior analysis system, can solve problems such as low efficiency, high cost of testing programs, inability to analyze binary malicious code, etc., and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
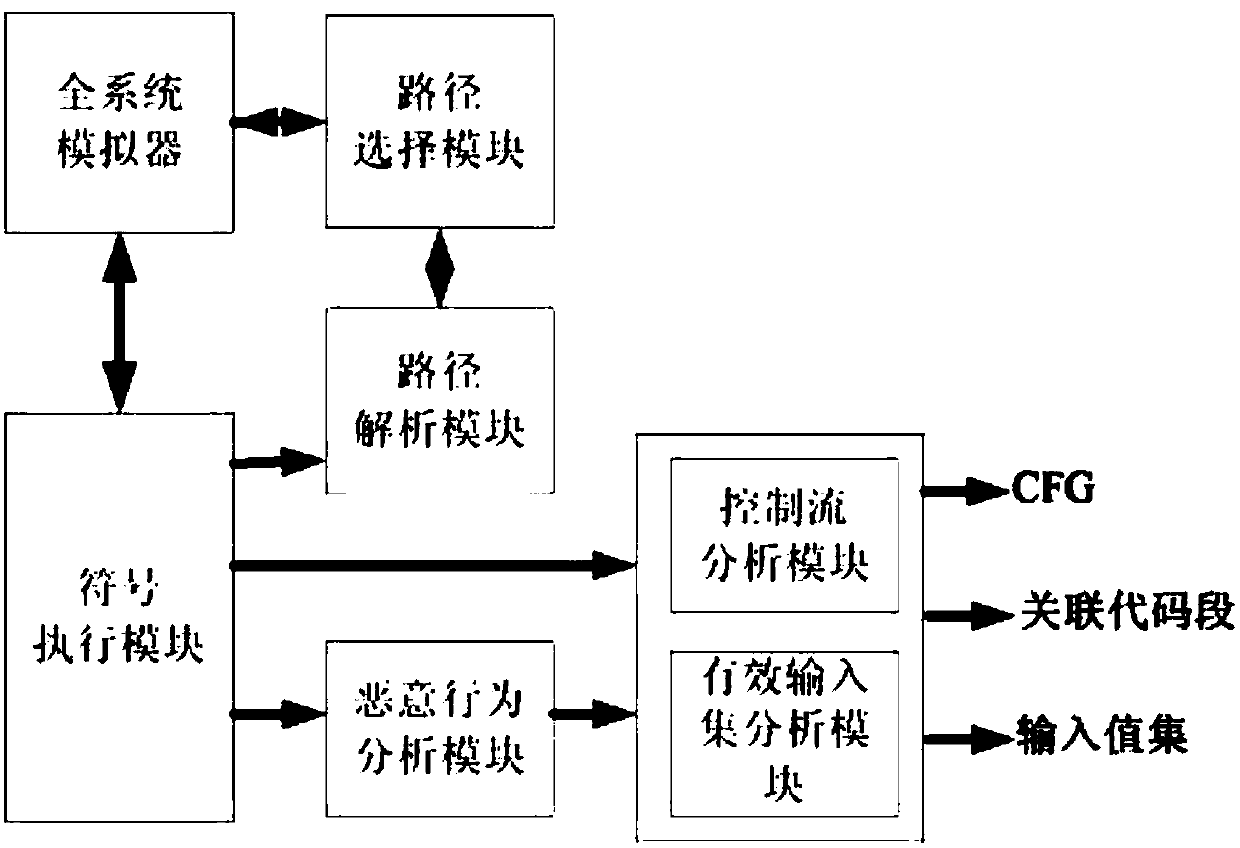
[0033] Embodiment one: see figure 1 , in the figure, the malicious code behavior automatic analysis system includes the whole system
[0034] system simulator, symbolic execution module, path analysis module, path selection module, malicious behavior analysis module, control flow analysis module and effective input set analysis module. The input of symbolic variables, after the symbolic execution module discovers the branch that depends on the symbolic variable in the binary malicious code, builds a path judgment predicate logic for each branch; the path analysis module analyzes the path judgment predicate logic generated by the symbolic execution module, and Branches are sorted. If the path judgment predicate logic is satisfyable, the path resolution module returns the input instance set that makes the path judgment predicate logic satisfied, and the path resolution module generates a new execution path and adds it to the path storage pool; path selection The module sets the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com