A method, device, computer equipment and storage medium for authorization authentication
An authentication method and permission technology, applied in the security field, can solve problems such as one-sided permission authentication, high business system coupling, and repeated development, so as to avoid repeated development work, ensure comprehensiveness, and reduce coupling.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
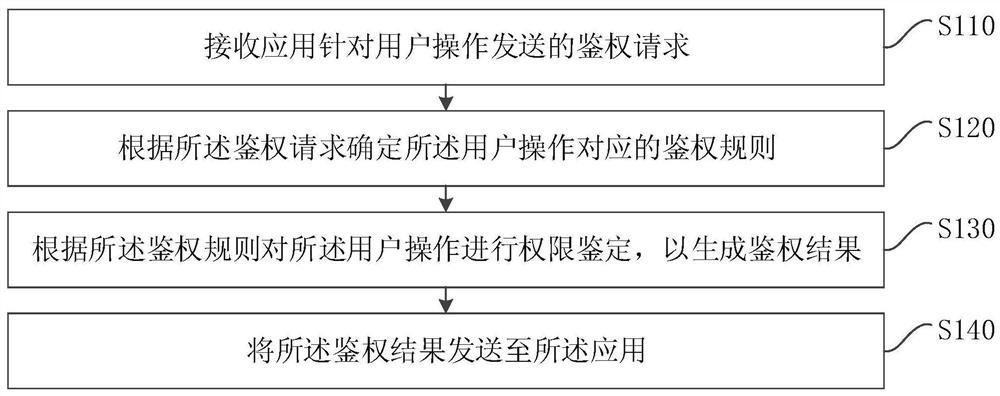
[0039] figure 1 It is a flow chart of an authority authentication method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where authority authentication is uniformly provided for system clusters. The method can be executed by an authority authentication device, which can be implemented by a software And / or hardware implementation, can be configured in computer equipment, such as server etc., this method specifically comprises the following steps:
[0040] S110. Receive an authentication request sent by an application for a user operation.
[0041] In this embodiment, a unified authentication system is set up in the system cluster to provide unified authorization authentication for each application in the system cluster.
[0042] Since most of the user operations in the business system are real-time operations, in order to ensure the real-time performance of user operations, the authentication system can be set as a real-time op...
Embodiment 2
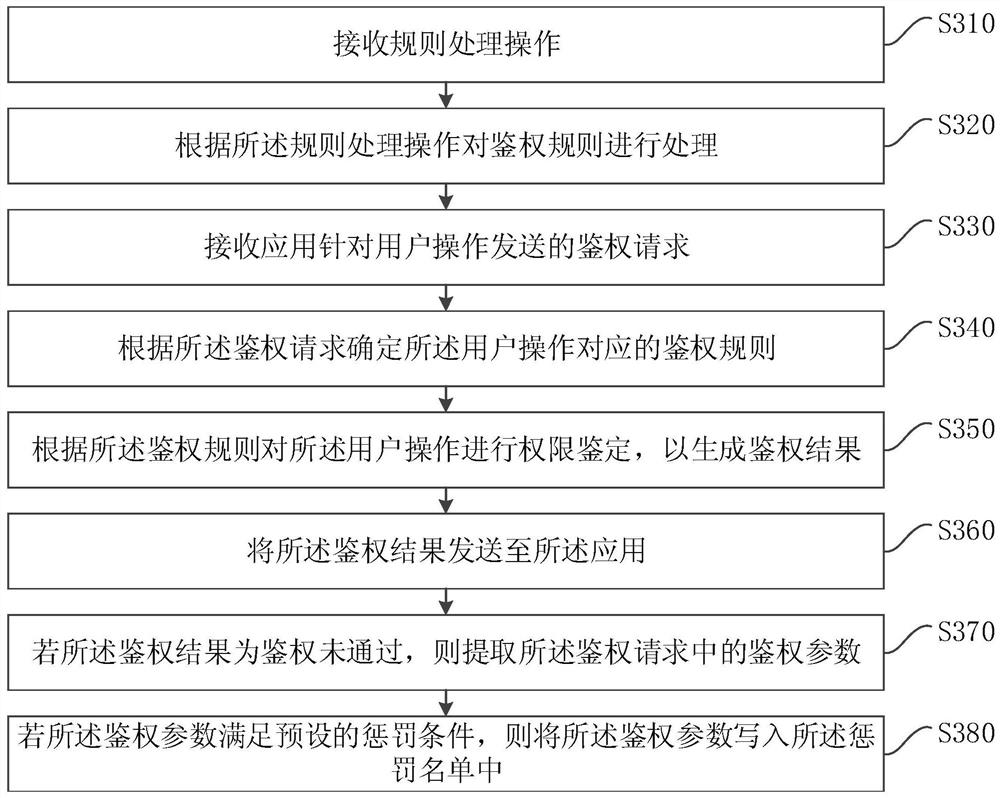
[0094] image 3 It is a flowchart of an authority authentication method provided by Embodiment 2 of the present invention. This embodiment is based on the foregoing embodiments, and further adds processing operations of editing authentication rules and penalty lists. The method specifically includes the following steps:
[0095] S310. A rule processing operation is received.
[0096] S320. Process the authentication rule according to the rule processing operation.
[0097] In this embodiment, a unified authentication system is set in the system cluster to provide unified authentication rules for each application in the system cluster.
[0098] The management user can send a rule processing operation to the authentication system for the authentication rule, and request the authentication system to process the authentication rule accordingly.
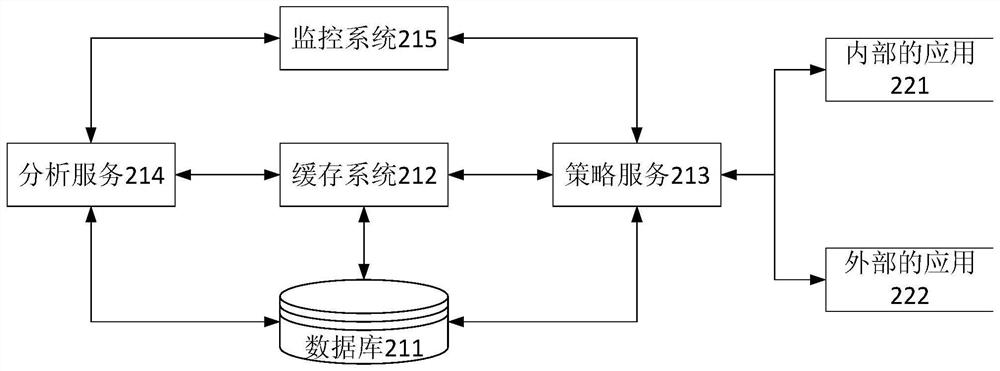
[0099] In one embodiment, as figure 2 As shown, the policy service 213 can provide a unified processing interface, and the internal...
Embodiment 3
[0127] Figure 4 It is a flow chart of an authority authentication method provided by Embodiment 3 of the present invention. This embodiment is applicable to the situation where authority authentication is uniformly provided for system clusters. The method can be executed by an authority authentication device, which can be implemented by a software And / or hardware implementation, can be configured in computer equipment, such as server etc., this method specifically comprises the following steps:
[0128] S410. Receive a user operation.
[0129] In this embodiment, there are multiple business-related applications in the system cluster, and each application may be relatively independent, that is, provide specific services for users independently.
[0130] For example, the live broadcast platform includes business-related applications such as broadcasting applications, barrage applications, and user information applications.
[0131] For the broadcasting application, the user's...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com