A mobile application program identification method based on K-means clustering and a random forest algorithm
A technology of k-means clustering and random forest algorithm, which is applied in the field of information security to reduce misjudgments, avoid misjudgments that interfere with samples, and improve accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
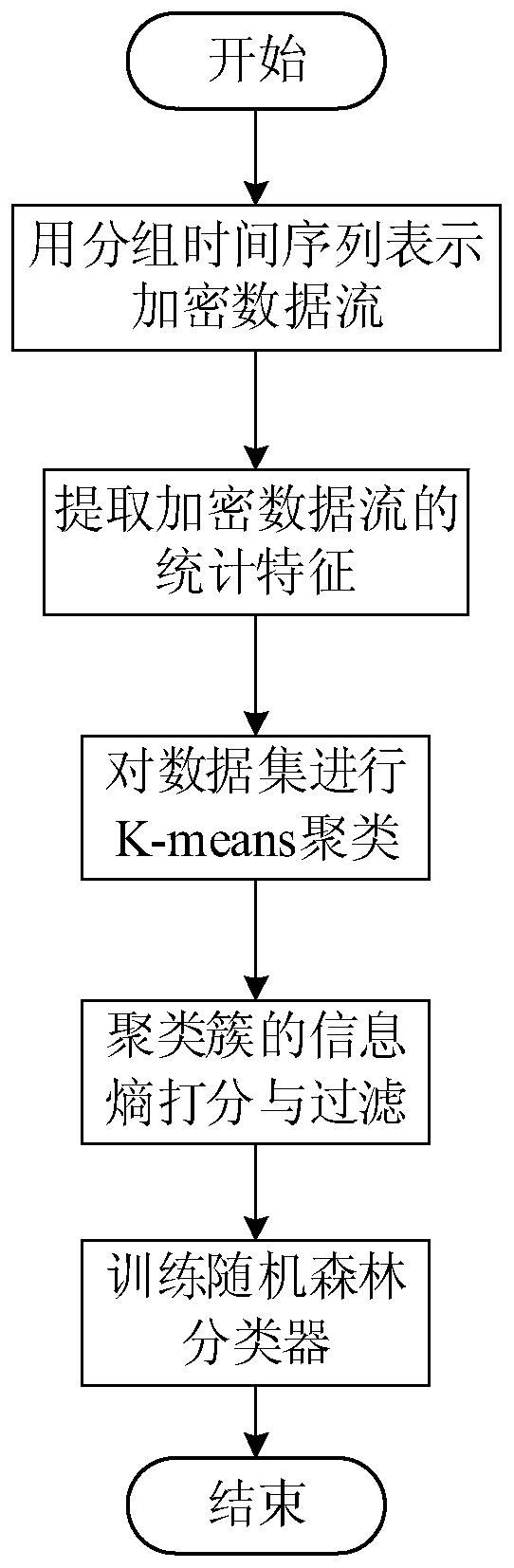
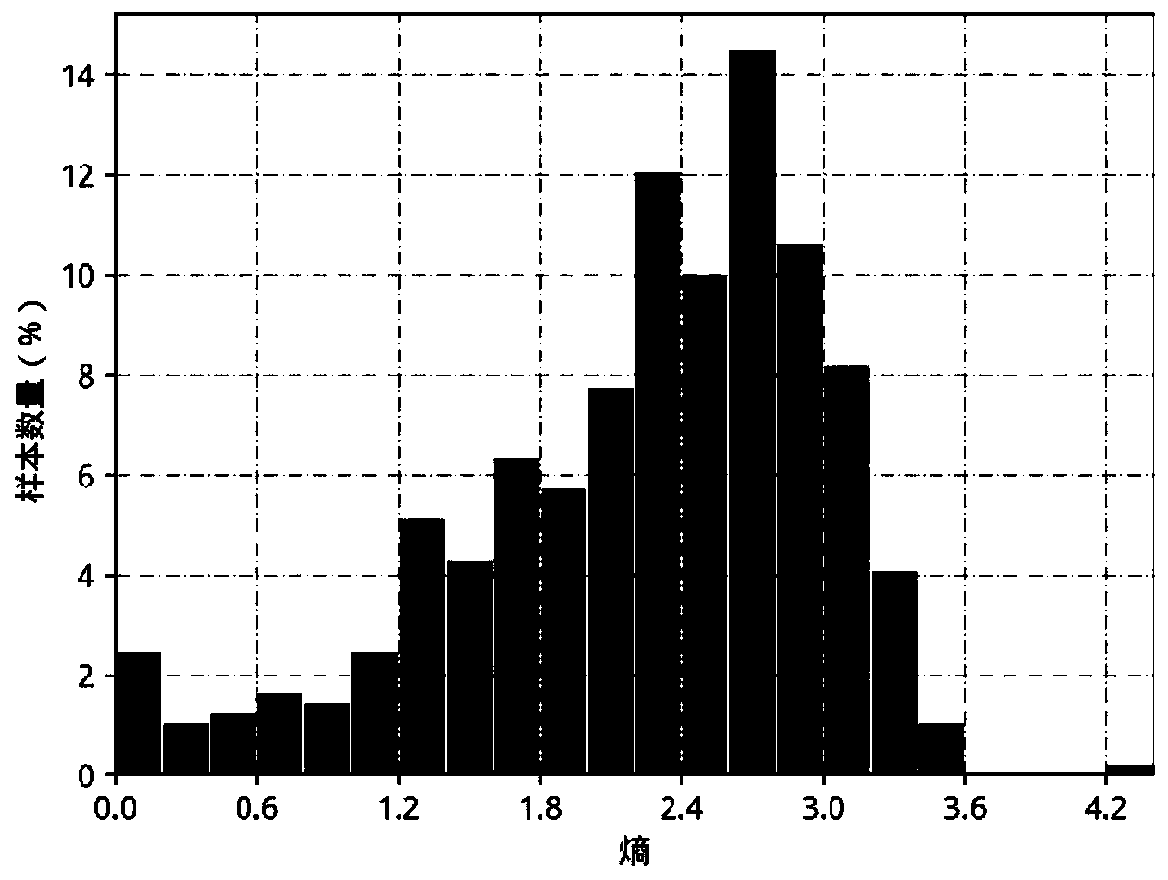
[0040] see figure 1 , this embodiment provides a mobile application identification method based on K-means clustering and random forest algorithm, such as figure 1 As shown, the method includes the following steps:
[0041] Step 1: Represent the encrypted data stream as a grouped time series
[0042] The encrypted data stream is discretized and expressed in the form of three grouped time series, the specific steps are as follows:
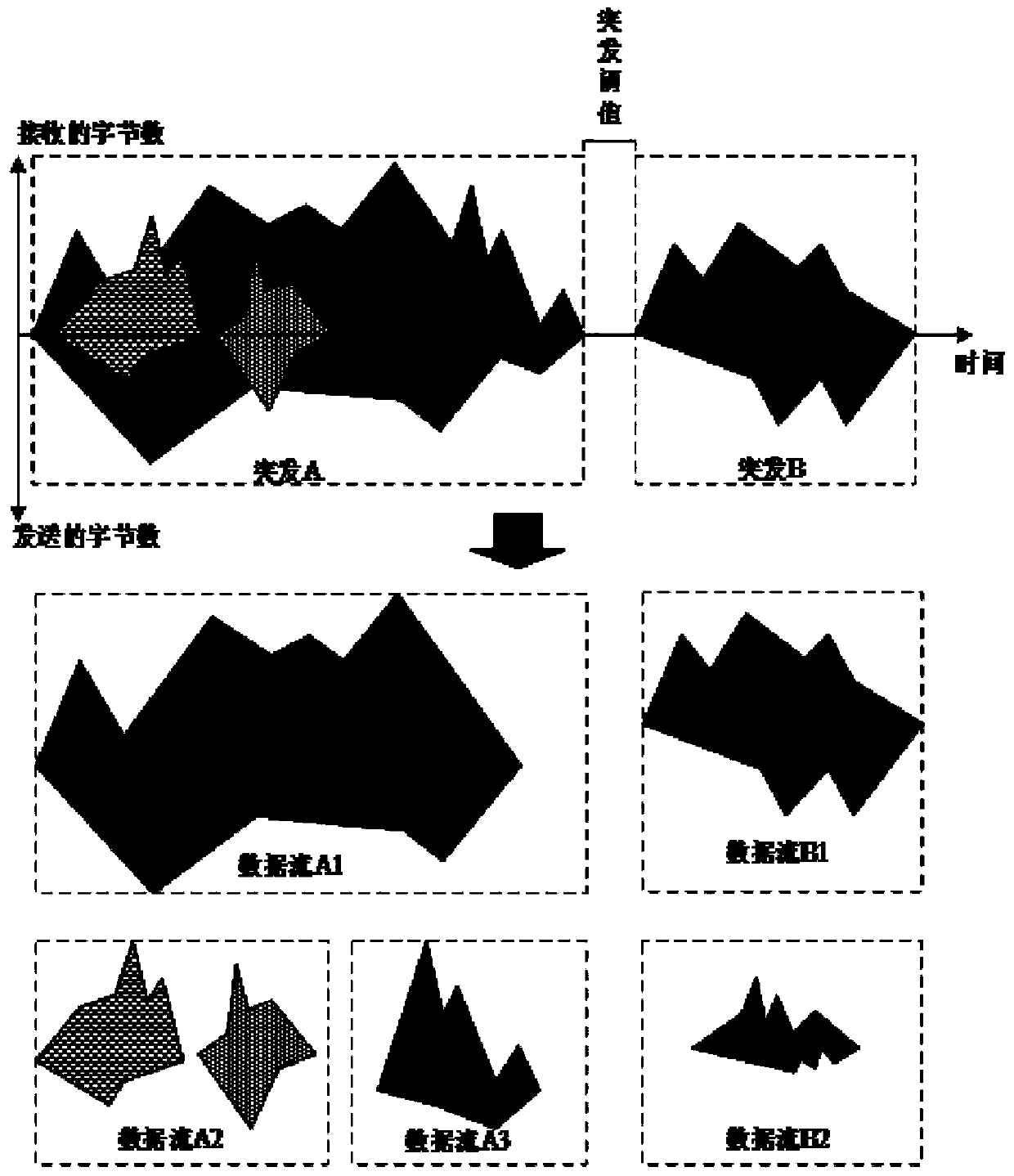
[0043] 1.1. Discretize continuous encrypted network traffic in units of bursts. A burst is a series of packets whose adjacent time interval is less than a certain threshold;
[0044] 1.2. Separate multiple encrypted data streams from each burst. In a burst, packets related to the same pair of quadruples form a data stream;
[0045] 1.3. Each data stream is represented by three grouped time series. The three time series are: (1) the sequence arranged in chronological order by the packet length of each packet flowing in the data stream; (2) the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com