TLS protocol session key restoration method based on random number implicit negotiation
A session key and random number technology, which is applied to the public key and key distribution of secure communication, can solve the problems that cannot meet the usage scenarios of TLS middleware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, and the steps include:
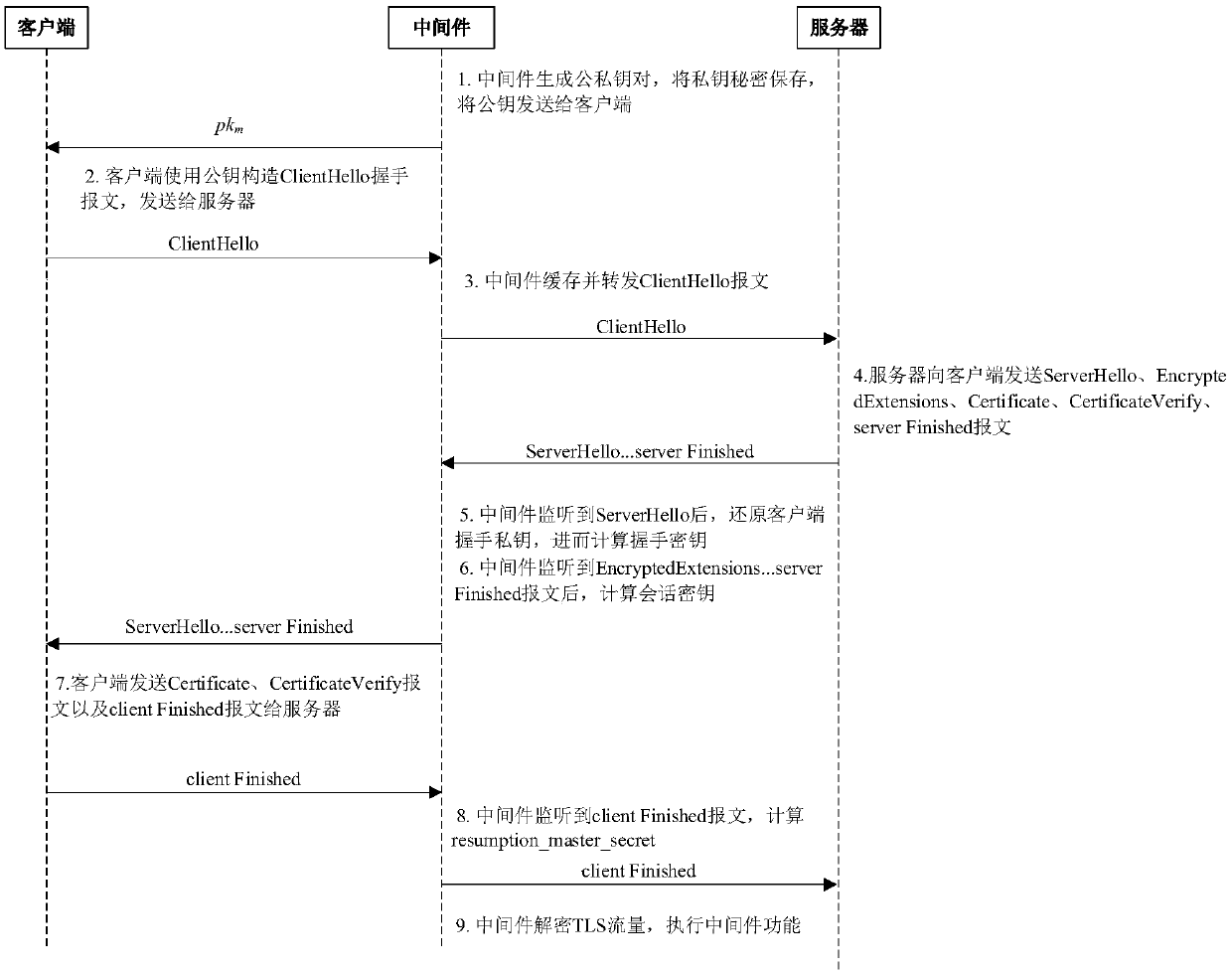
[0066] In the first step, the middleware randomly generates a public-private key pair (sk m , pk m ), Where g is the generator of the elliptic curve x25519. The middleware sends the private key sk m Keep it secret, put the public key pk m sent to the client.
[0067] In the second step, the client receives the public key pk m After that, save it locally and use it to generate a handshake temporary private key when establishing a TLS connection later. The client and the server perform a handshake. When constructing the handshake message, the client selects a random number r, and sets g r Fill in the random number field of the handshake message. For the elliptic curve chosen by the client for ECDHE key exchange, the client computes the handshake ephemeral key client will esk c The corresponding public ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com