Container configuration method and computing node
A technology for computing nodes and containers, applied in the network field, can solve the problems of IP address persistence and migration that cannot support containers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manner of the present application will be further described in detail below in conjunction with the accompanying drawings.
[0062] Before explaining and describing the embodiments of the present invention in detail, the application scenarios and implementation environments involved in the embodiments of the present invention will be described.
[0063] First, the application scenarios involved in the embodiments of the present invention are described.
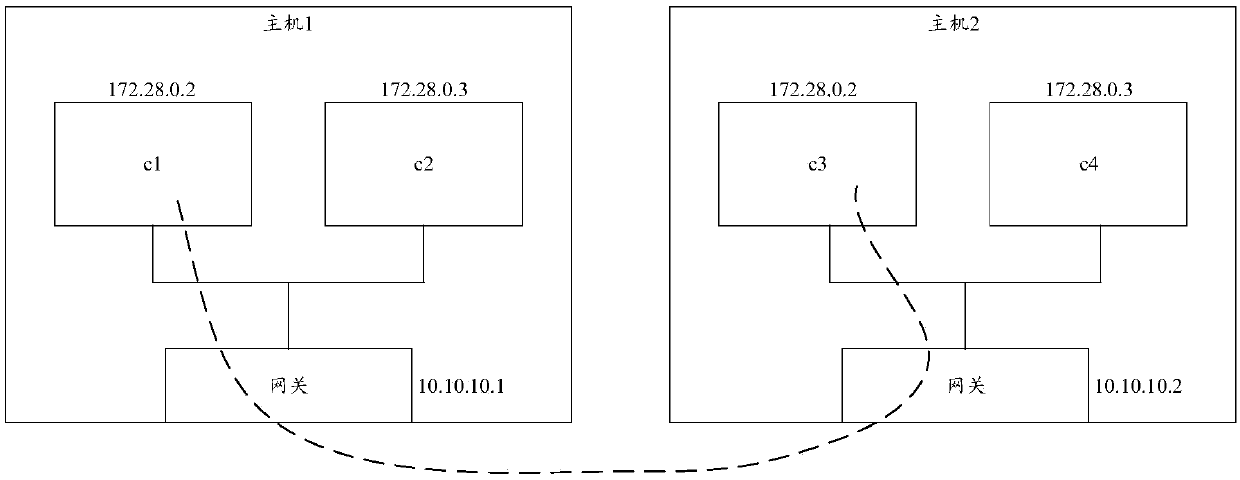
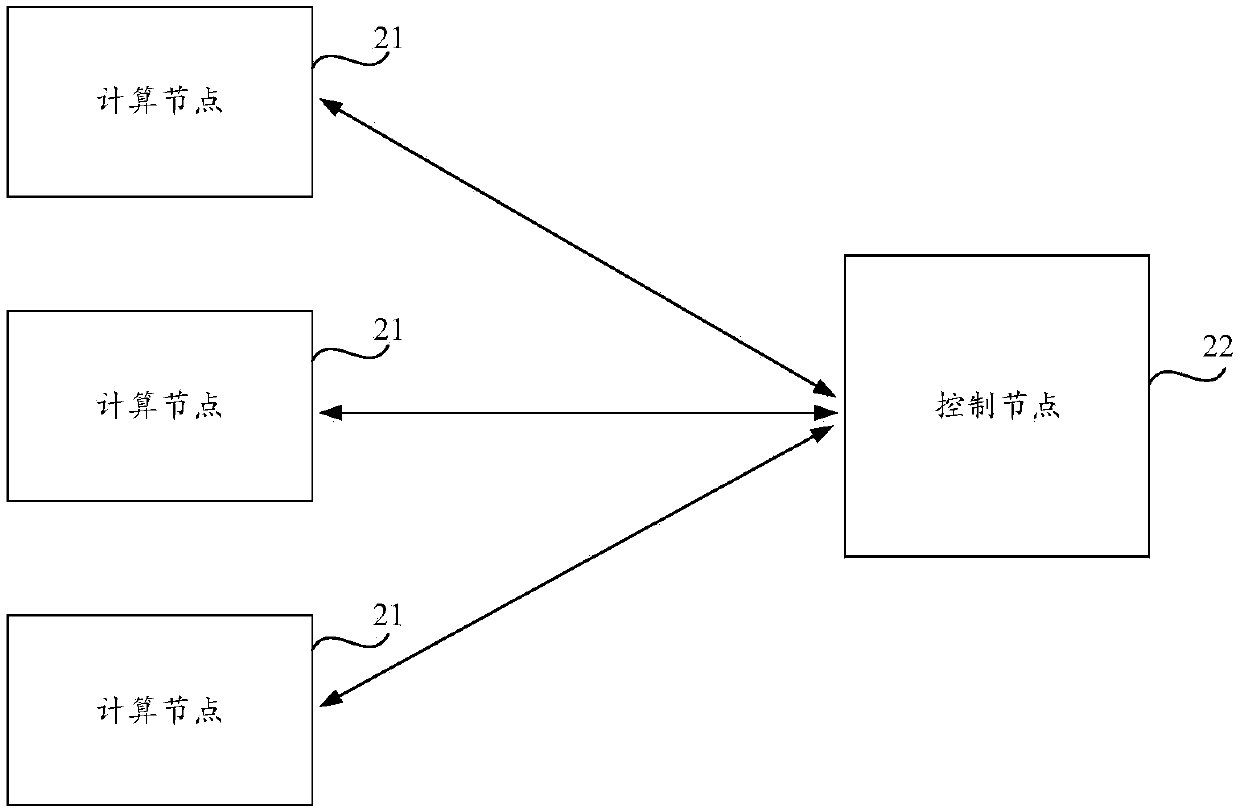
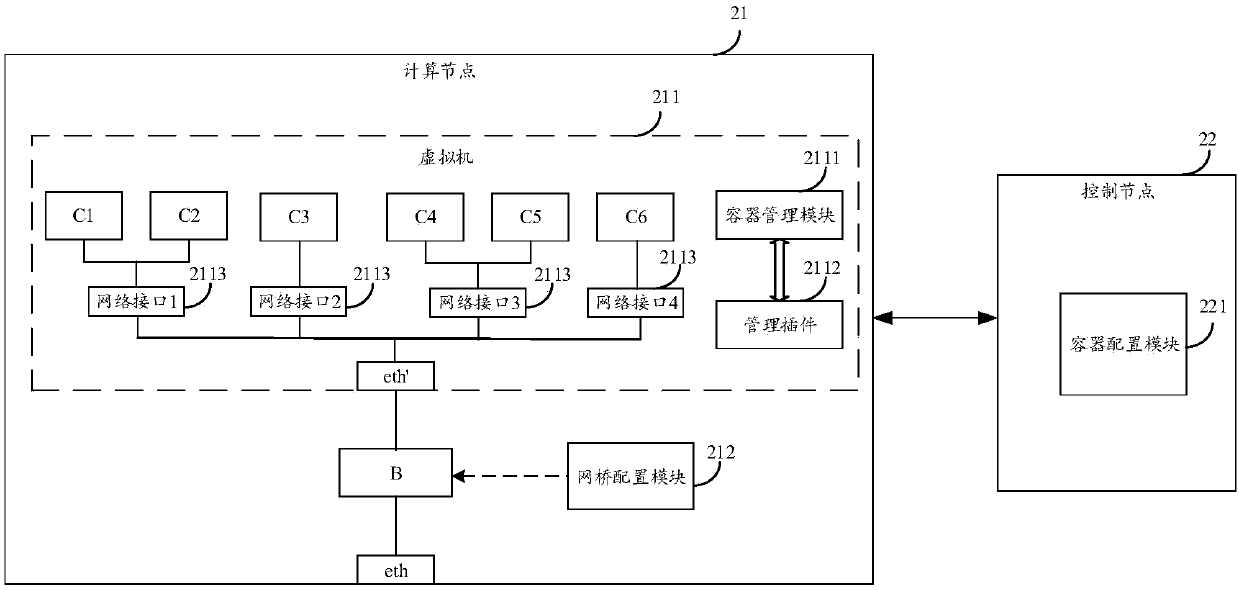
[0064] The embodiments of the present invention can be applied to container configuration scenarios, and specifically can be applied to the scenario of configuring network attributes (such as IP address, MAC address, etc.) and transmission attributes (such as data transmission mode, etc.) of the container after the container is created. For example, after receiving a configuration instruction triggered ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com