Malware detection method based on HTTP behavior graph
A malware and detection method technology, applied in the field of network security, can solve the problems of poor classification effect and difficulty in distinguishing normal software and malware, and achieve the effect of good classification effect and high classification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
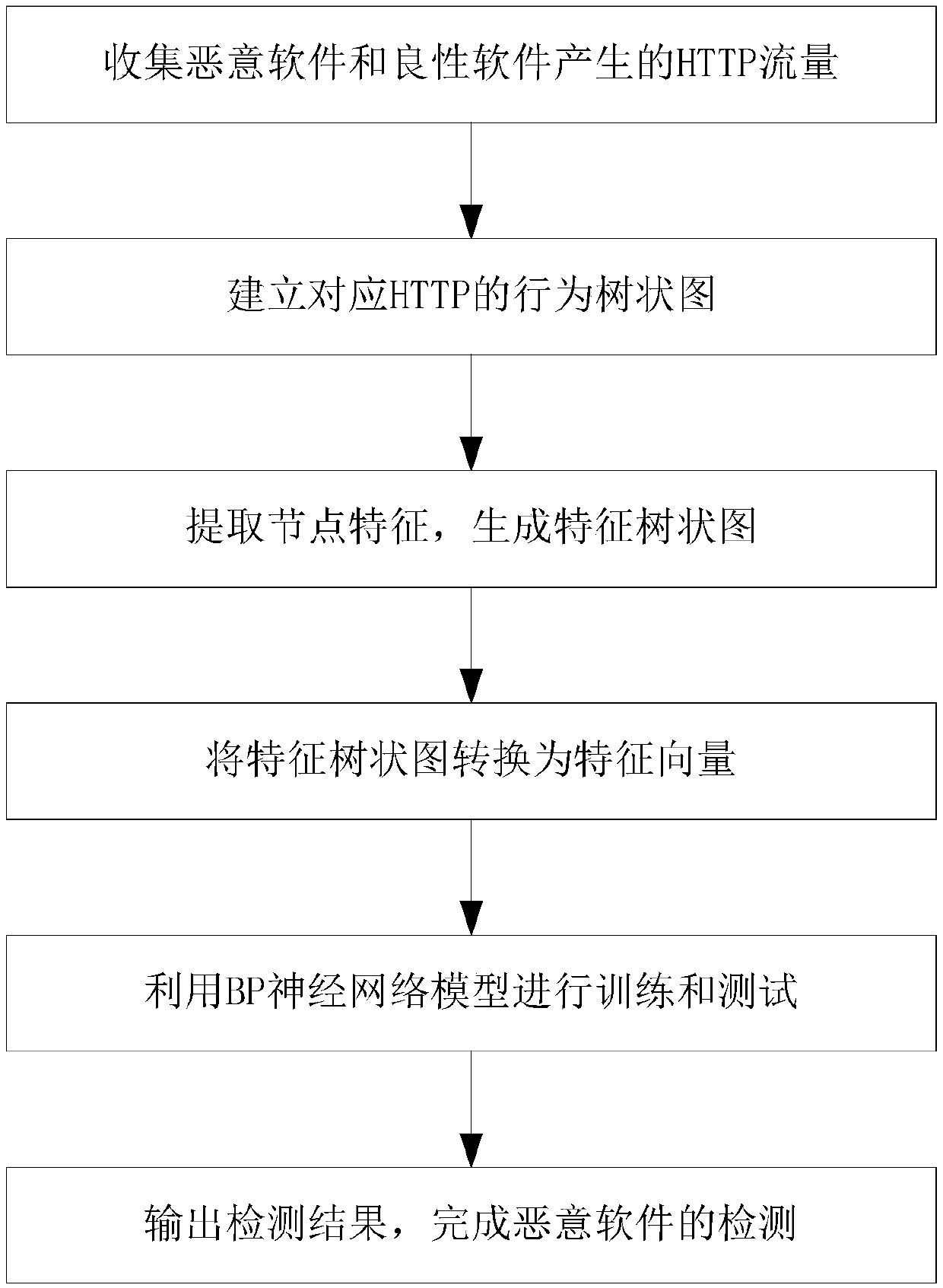
[0056] A kind of malicious software detection method based on HTTP behavior graph that the preferred embodiment of the present invention provides, comprises the following steps:
[0057] Step 1: Collect HTTP traffic generated by malware and benign software;
[0058] Step 1.1: Use cuckoo to build a sandbox to simulate the real use environment of the software;
[0059] Step 1.2: put the collected malware and benign software into the sandbox in turn, and collect the traffic generated by the malware and benign software;
[0060] Step 1.3: Input the collected website of Alexatop10000 into the sandbox, and collect the website traffic of Alexatop10000 in turn as a supplement of benign data;
[0061] Step 2: Use the collected traffic to build a behavior dendrogram corresponding to HTTP, such as figure 2 As shown, each tree of the behavior dendrogram represents the HTTP behavior activities of the client in the sandbox, and the behavior dendrogram includes a root node, a child node a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com