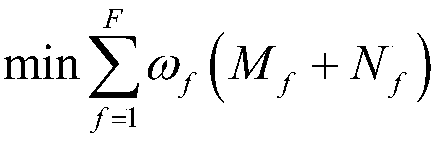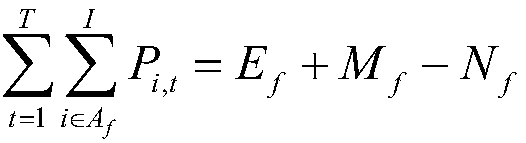Centralized safety analysis method, device and system for multi-component electric quantity decentralized transaction of multiple power plants
A security analysis and multi-component technology, applied in the direction of data processing applications, forecasting, instruments, etc., can solve the problems of market fairness, lack of supporting technology, and difficulty in satisfying the operation mode of the power grid
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
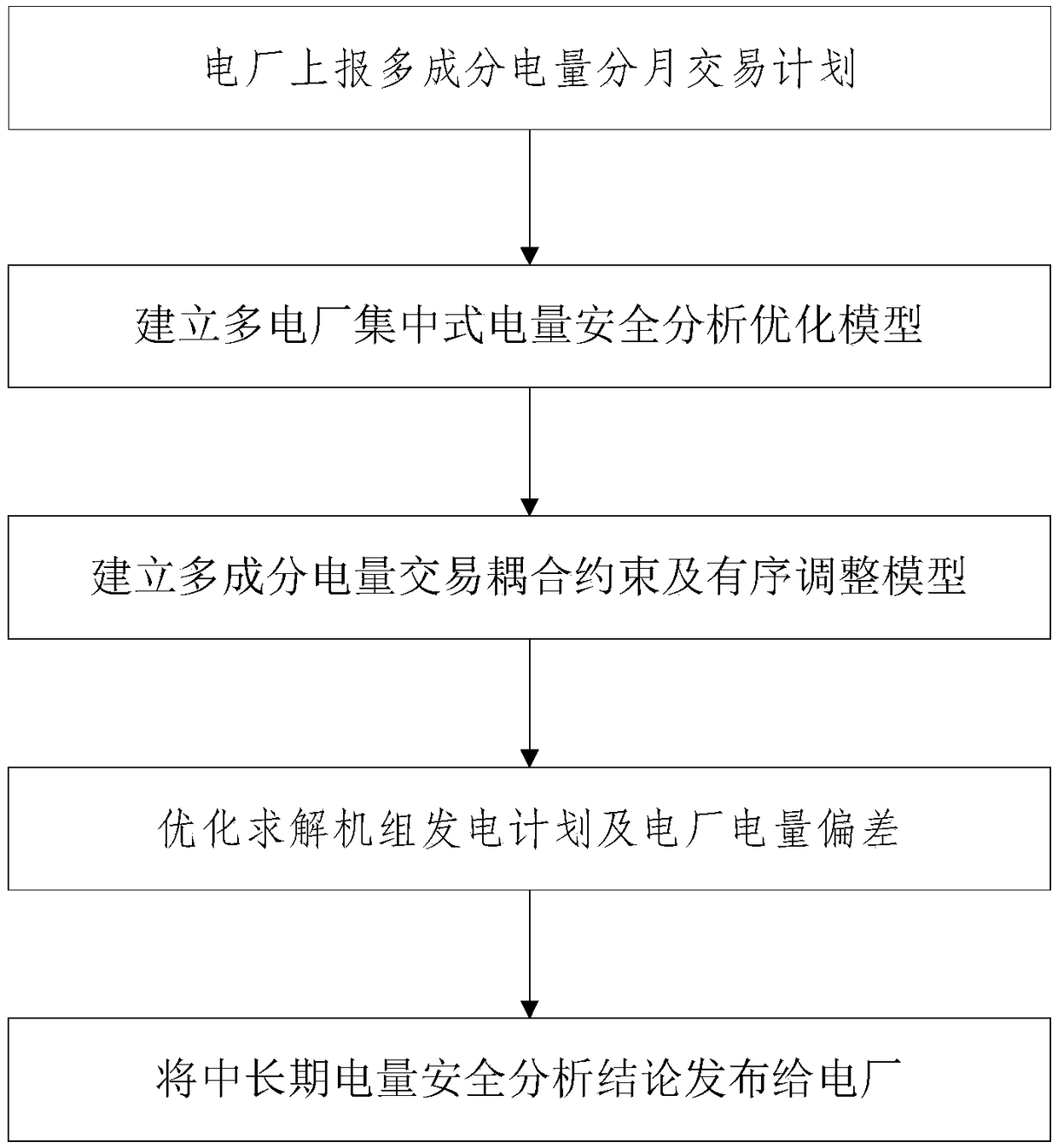
[0078] In the embodiment of the present invention, a centralized security analysis method for the decentralized transaction of multi-power plants and multi-component electricity is provided, which is aimed at the provincial power grid; Medium and long-term electricity trading, providing security analysis services before the transaction, judging whether the transaction electricity can be executed, locating the cause after the electricity exceeds the limit, and how to reasonably adjust the electricity transaction after the limit is exceeded.
[0079] In the embodiment of the present invention, the centralized security analysis method for multi-power plants and multi-component electricity decentralized transactions is mainly based on the annual electricity monthly arrangement plan data and monthly electricity market transaction plan data and monthly electricity market transaction plan data reported by power plants in rolling reports, and based on system load forecasting , maintena...
Embodiment 2
[0120] Based on the same inventive concept as in Embodiment 1, the embodiment of the present invention provides a centralized security analysis device for multi-power plant multi-component electricity decentralized transactions, including:
[0121] The first acquisition module is used to obtain the annual power monthly arrangement plan data reported by the power plant, the monthly power market transaction plan data and the multi-component power contracts;
[0122] The second acquisition module is used to obtain a multi-power plant centralized power security analysis and optimization model. The constraints of the multi-power plant centralized power security analysis and optimization model include: system operation constraints, power grid security constraints, and unit operation constraints; the optimization objective is: Minimize the sum of positive power deviation and negative power deviation between the total power generation of the power plant and the total planned power;
...
Embodiment 3
[0129]Based on the same inventive concept as that of Embodiment 1, the embodiment of the present invention provides a centralized security analysis system for multi-power plants and multi-component electricity decentralized transactions, including:
[0130] a processor adapted to implement the instructions; and
[0131] The storage device is suitable for storing a plurality of instructions, and the instructions are suitable for being loaded by the processor and executing the steps described in any one of Embodiment 1.
[0132] The system of the present invention includes annual, monthly, day-ahead, intra-day, real-time, and multiple cycle power grid security analysis functions. The long-term power trading is carried out, and the calculation boundary of the system is provided for the security analysis of the day. Mid-to-long-term security analysis is that the power dispatching agency conducts security analysis and calculations in subsequent months based on grid operation infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com