Document manipulation method, device and computer storage medium
A technology of file operation and operation method, which is applied in computer security devices, computing, file systems, etc., can solve problems such as system paralysis, fatal blows, and hacker attacks on servers, so as to avoid random tampering and ensure security and fairness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
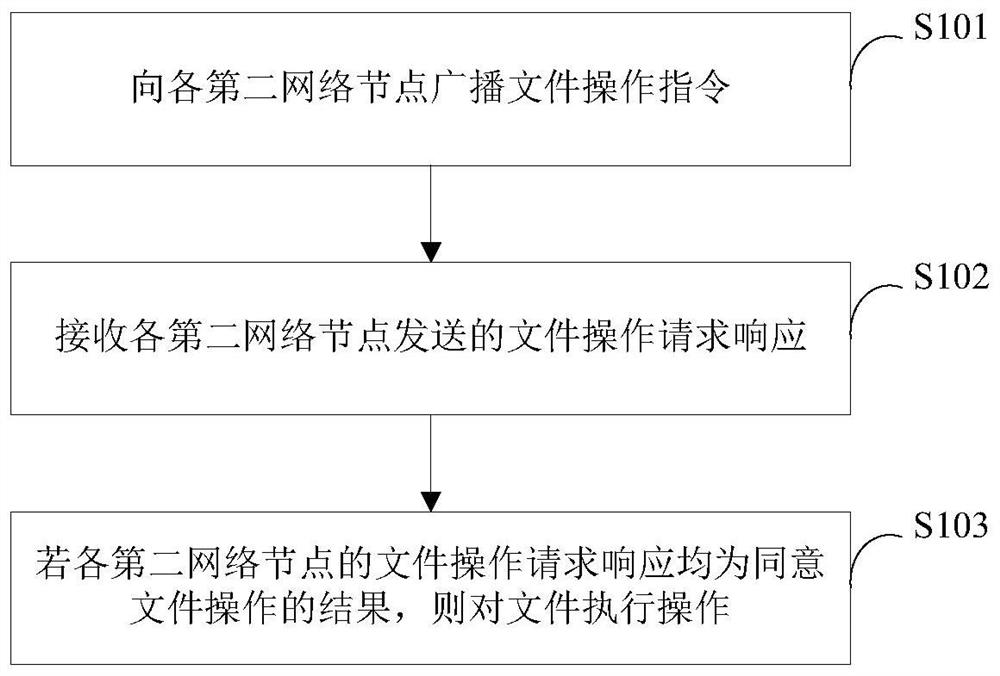
[0059] figure 1 A schematic flow chart of the operation method of the file provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method includes the following steps:
[0060] S101. Broadcast a file operation instruction to each second network node, where the file operation instruction includes: a file identifier, a first network node identifier, and an operation identifier, so that each second network node judges according to the file identifier, the first network node identifier, and the operation identifier Whether the first network node has the authority to operate the file corresponding to the file identifier.
[0061] Specifically, the blockchain network of this embodiment includes at least two network nodes, and each network node corresponds to a unique identifier. The network node that broadcasts file operation instructions is called the first network node, and the network node in the blockchain network is called The network nodes other tha...
Embodiment 2
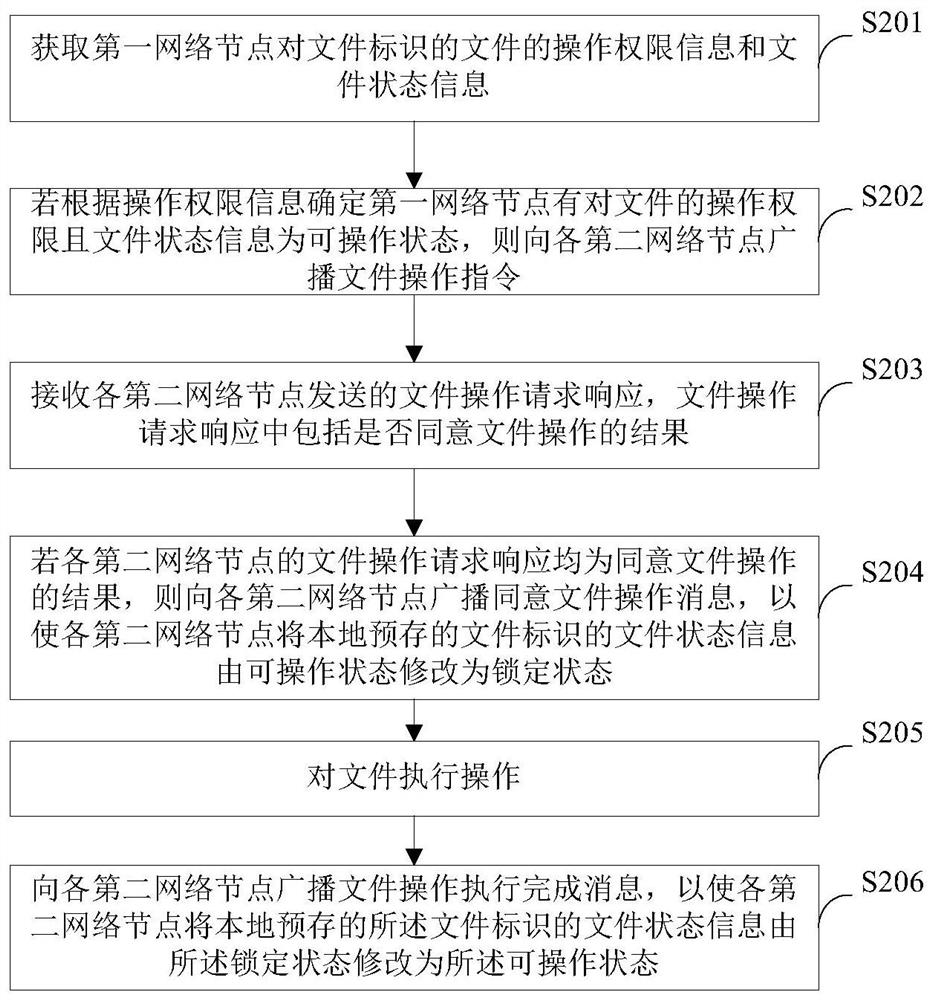
[0070] figure 2 A schematic flow chart of the operation method of the file provided in Embodiment 2 of the present invention, such as figure 2 As shown, the method may include the following steps:
[0071] S201. Obtain operation authority information and file status information of the file identified by the file by the first network node.
[0072] S202. If it is determined according to the operation authority information that the first network node has the operation authority to the file and the file state information is operable, broadcast the file operation instruction to each second network node.
[0073] S203. Receive a file operation request response sent by each second network node, where the file operation request response includes a result of whether the file operation is approved.
[0074] Specifically, all network nodes in the blockchain network pre-store the file identifiers of all files, the corresponding file status information and the operation authority info...
Embodiment 3
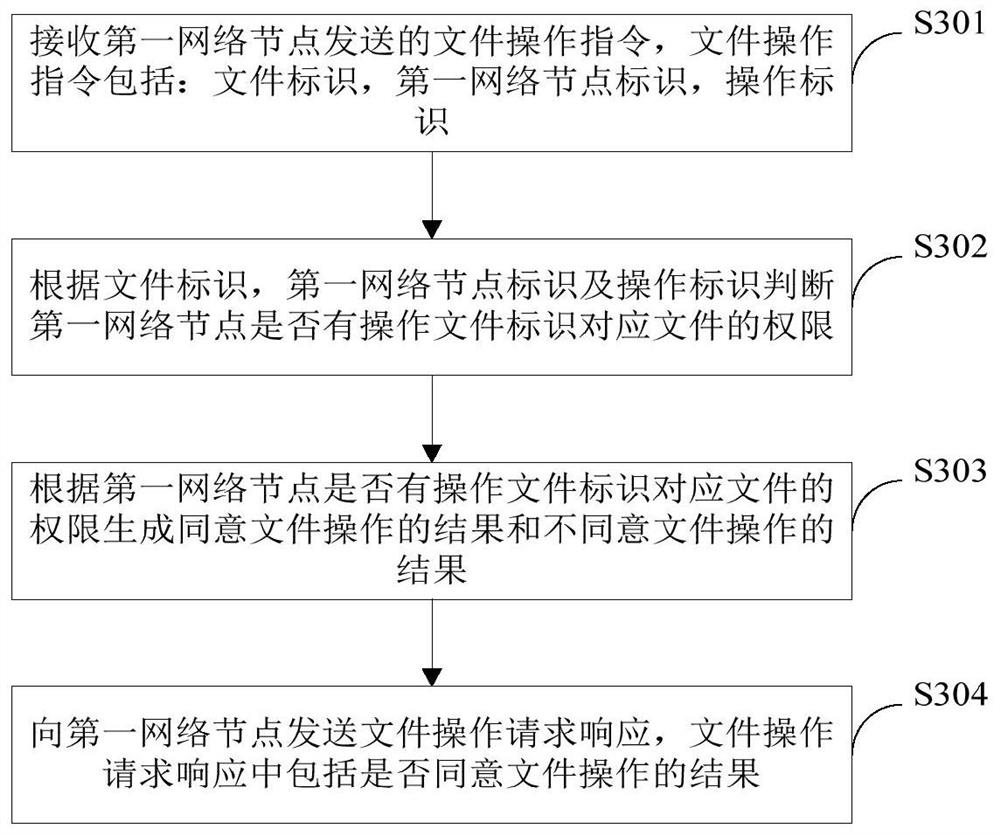
[0085] image 3 A schematic flow chart of the operation method of the file provided in Embodiment 3 of the present invention, such as image 3 As shown, the method includes:
[0086] S301. Receive a file operation instruction sent by a first network node, where the file operation instruction includes: a file identifier, a first network node identifier, and an operation identifier.
[0087] S302. Determine whether the first network node has permission to operate the file corresponding to the file identifier according to the file identifier, the first network node identifier, and the operation identifier.
[0088] S303. Generate a result of agreeing to the file operation and a result of not agreeing to the file operation according to whether the first network node has the authority to operate the file corresponding to the file identifier.
[0089] S304. Send a file operation request response to the first network node, where the file operation request response includes a result...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com