Authentication method for network slice and corresponding device, system and medium
A network slicing and network authentication technology, applied in the field of systems and media, network slicing authentication methods and corresponding devices, can solve problems such as the inability to meet UE access network slicing authentication requirements, and achieve the effect of satisfying dynamic deployment characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
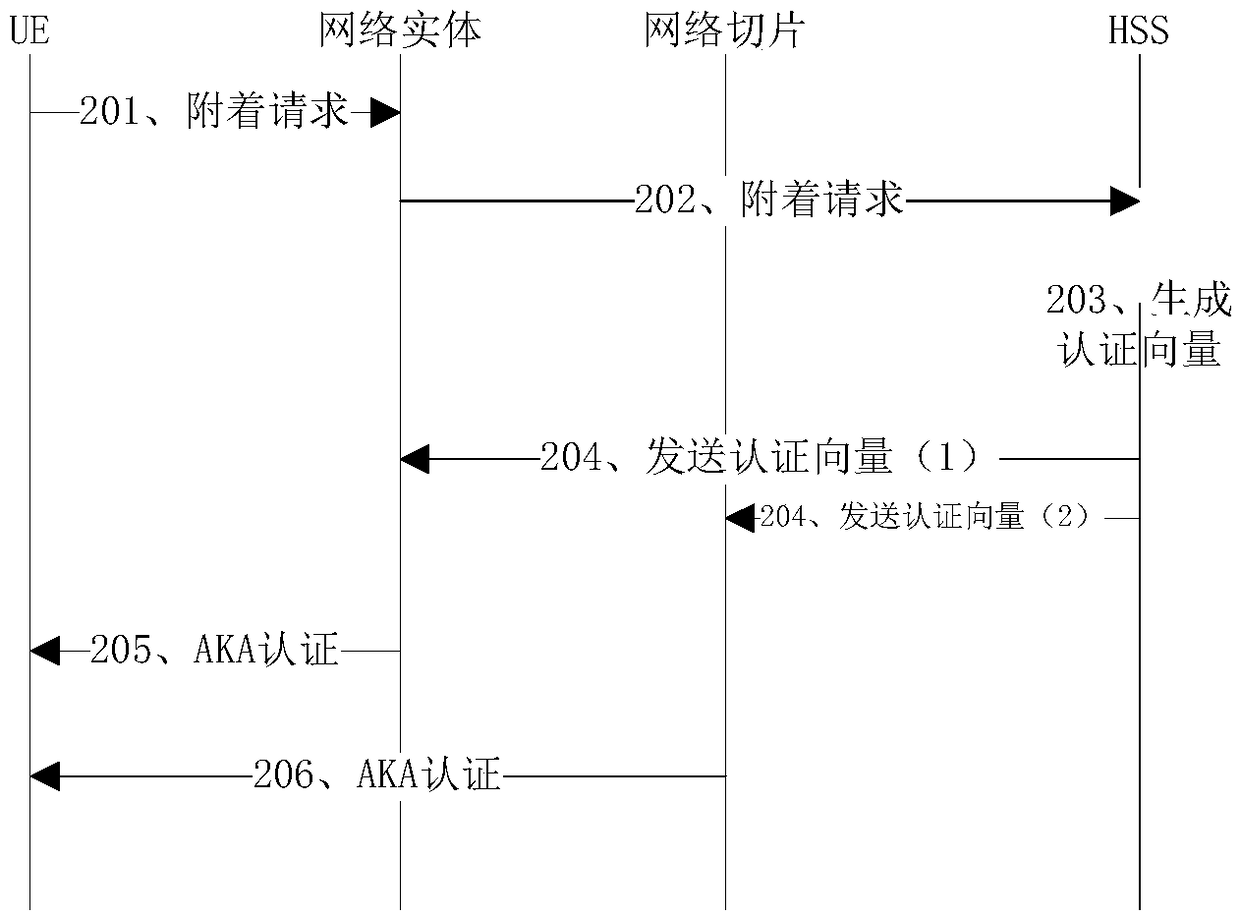
[0037] Such as figure 1 As shown, an embodiment of the present invention provides an authentication method for network slicing, the method comprising:
[0038] S101, acquiring a network slice authentication vector corresponding to user network slice identity information SID (Slice Identification) of the user terminal UE from a network authentication entity;
[0039] S102. Perform authentication with the user terminal according to the network slice authentication vector.
[0040] The network authentication entity may be a home subscriber server (Home Subscriber Server, HSS).
[0041] The method in the embodiment of the present invention is used for a network slicing functional entity.
[0042] In the embodiment of the present invention, the network slice authentication vector corresponding to the user network slice identity information of the user terminal UE is obtained from the network authentication entity; For example, in 5G), based on the introduction of network slicing...
Embodiment 2
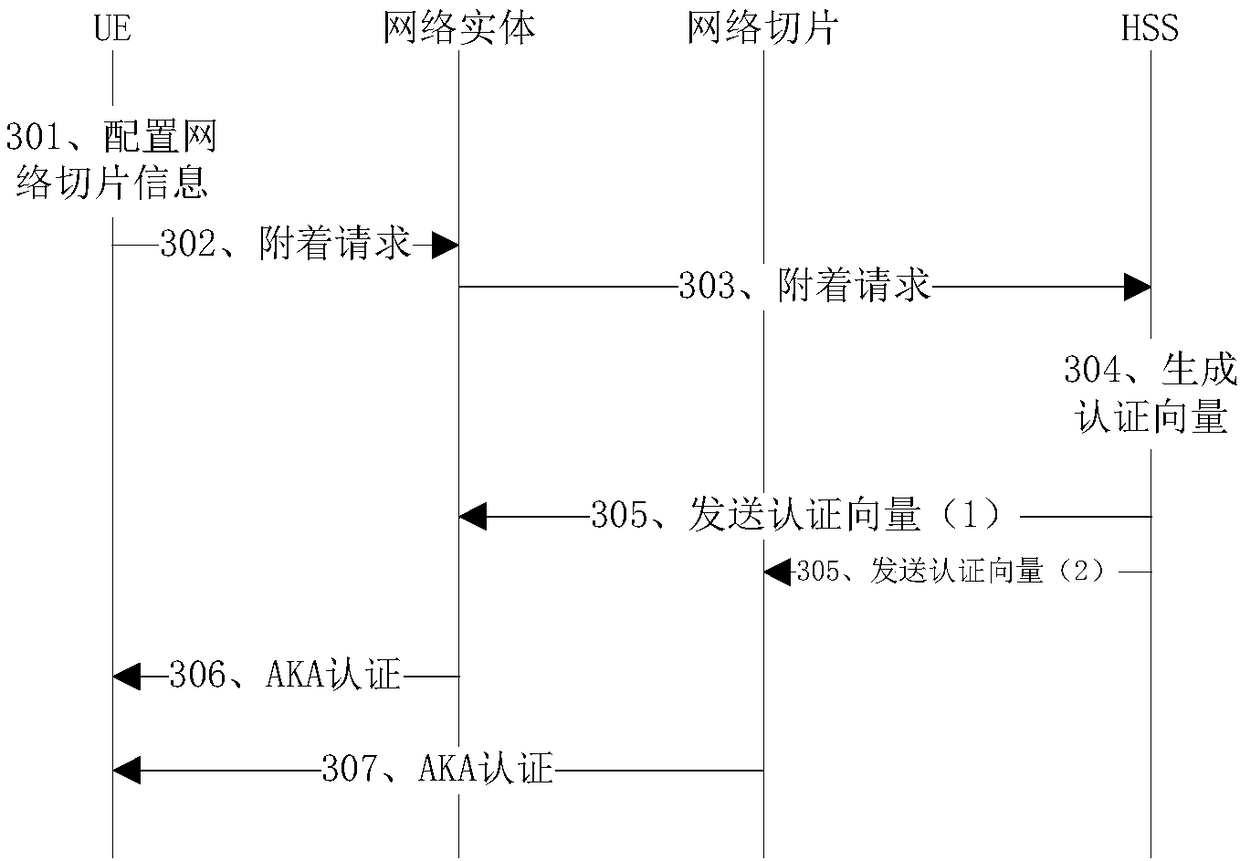
[0094] Such as Figure 6 As shown, an embodiment of the present invention provides an authentication method for network slicing, wherein the method includes:
[0095] S601. Obtain attachment request information of the user terminal;
[0096] S602. Generate a network slice authentication vector corresponding to the user network slice identity information of the user terminal according to the attachment request information;
[0097] S603. Send the network slicing authentication vector to a network slicing functional entity, so that the network slicing functional entity authenticates with the user terminal according to the network slicing authentication vector.
[0098] The method in the embodiment of the present invention is used for network authentication entities, such as HSS.
[0099]The embodiment of the present invention obtains the attachment request information of the user terminal; generates a network slice authentication vector corresponding to the user network slice ...
Embodiment 3
[0134] Such as Figure 7 As shown, the embodiment of the present invention provides a network slicing function entity device, the device includes a first memory 70 and a first processor 72; the first memory 70 stores an authentication computer program for network slicing of the device The computer program is executed by the first processor 72 to realize the following steps:
[0135] Obtaining a network slice authentication vector corresponding to the user network slice identity information of the user terminal from the network authentication entity;
[0136] performing authentication with the user terminal according to the network slice authentication vector.
[0137] Optionally, the network slice authentication vector includes at least the following parameters: random number, expected response, network slice key and authentication token;
[0138] The authentication is the Authentication and Key Agreement Protocol (AKA) authentication of the mobile communication network;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com