A method for detecting VPN based on open stack network system
A detection method and network system technology, applied in the detection field based on the OpenStack network system VPN, can solve the problems of long verification time, low test efficiency, and the inability of test developers of non-network modules to check by themselves, so as to achieve wide application and reduce The cost of testing and R&D, and the authenticity and reliability of test conclusions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
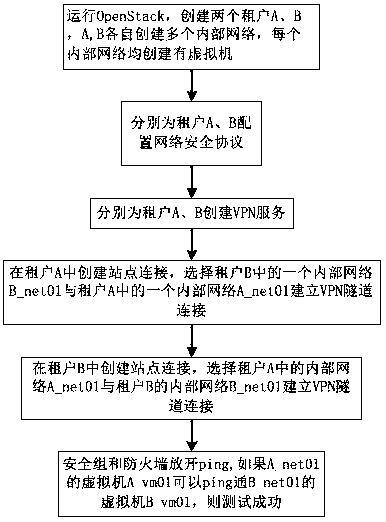
[0030] Such as figure 1 Shown a kind of detection method based on Open Stack network system VPN, it is characterized in that, comprises the steps:
[0031] Step 1: Run Open Stack, create two tenants A and B, A and B each create multiple internal networks, each internal network is created with a virtual machine.
[0032] Step 2: Configure network security protocols for tenants A and B respectively.
[0033] Step 3: Create VPN services for tenants A and B respectively.
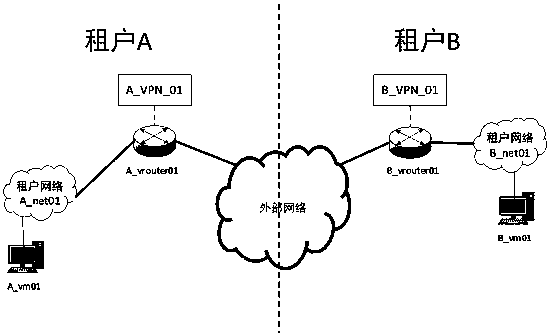
[0034] Step 4: Create a site connection in tenant A, select an internal network B_net01 in tenant B to establish a VPN tunnel connection with an internal network A_net01 in tenant A.
[0035] Step 5: Create a site connection in tenant B, select tenant A's internal network A_net01 to establish a VPN tunnel connection with tenant B's internal network B_net01.
[0036] Step 6: Release ping from the security group and firewall. If the virtual machine A_vm01 of A_net01 can ping the virtual machine B_vm01 of B_net0...
Embodiment 2
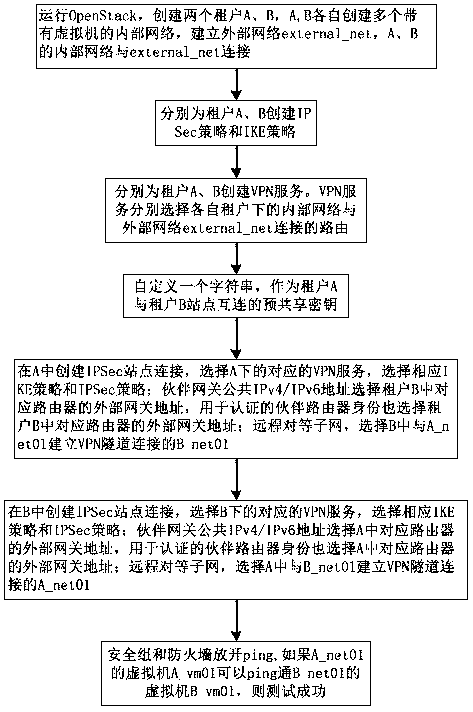
[0039] Such as figure 2 and image 3 Shown a kind of detection method based on Open Stack network system VPN, it is characterized in that, comprises the steps:
[0040] Step 1: Run Open Stack, create two tenants A and B, A and B each create multiple internal networks, each internal network is created with a virtual machine. Create an external network external_net, and the internal networks of tenants A and B are connected to the external network external_net through their respective routes.
[0041] Step 2: Create IPSec policies and IKE policies for tenants A and B respectively.
[0042] Step 3: Create VPN services for tenants A and B respectively. The VPN service respectively selects the route connecting the internal network and the external network external_net under the respective tenants.
[0043] Step 4: Customize a string as the pre-shared key for tenant A and tenant B site interconnection.
[0044]Step 5: Create an IPSec site connection in tenant A, select the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com