A blockchain malicious node discovery and isolation method and device
A malicious node and blockchain technology, applied in the blockchain field, can solve problems such as exhaustion of resources, occupation, failure to provide services normally, and achieve the effect of improving reliability and fault tolerance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The concept, specific structure and technical effects of the present disclosure will be clearly and completely described below in conjunction with the embodiments and drawings, so as to fully understand the purpose, scheme and effect of the present disclosure. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
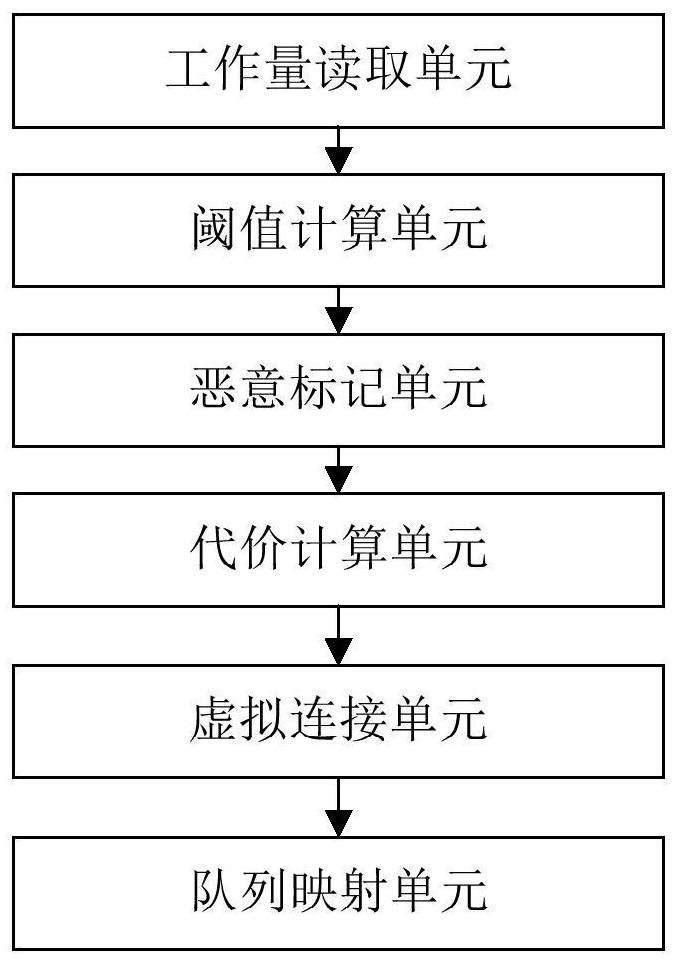
[0036] Such as figure 1 Shown is a flow chart of a blockchain malicious node discovery and isolation method according to the present disclosure, combined below figure 1 A method for discovering and isolating malicious blockchain nodes according to an embodiment of the present disclosure will be described.
[0037] This disclosure proposes a method for discovering and isolating malicious nodes in blockchain, which specifically includes the following steps:
[0038] Step 1, read the proof-of-work data of each blockchain node in the blockchain network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com