A Virtual Network Mapping Method Oriented to Network Security Experiment
A technology of virtual network mapping and virtual network, applied in data exchange network, software simulation/interpretation/simulation, instruments, etc., can solve the problem of low revenue-to-cost ratio
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0024] Specific implementation mode one: a kind of virtual network mapping method for network security experiment comprises the following steps:
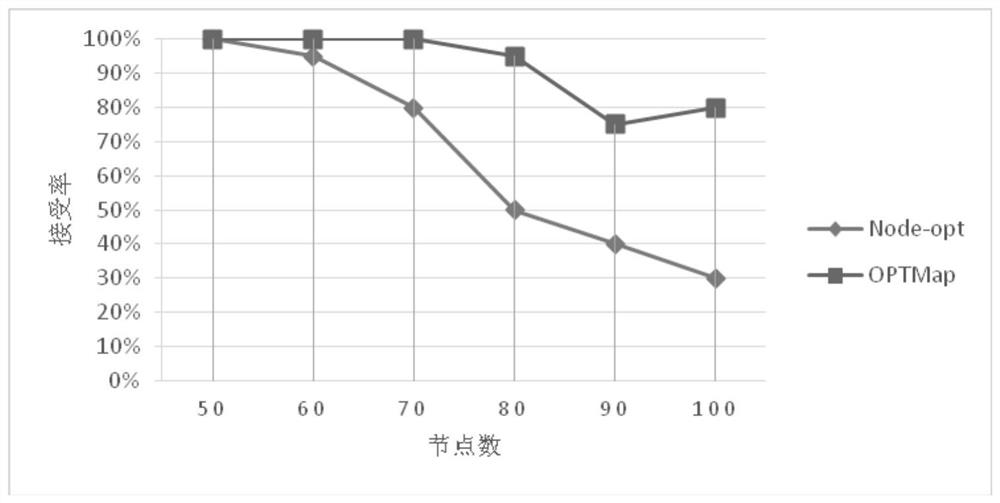
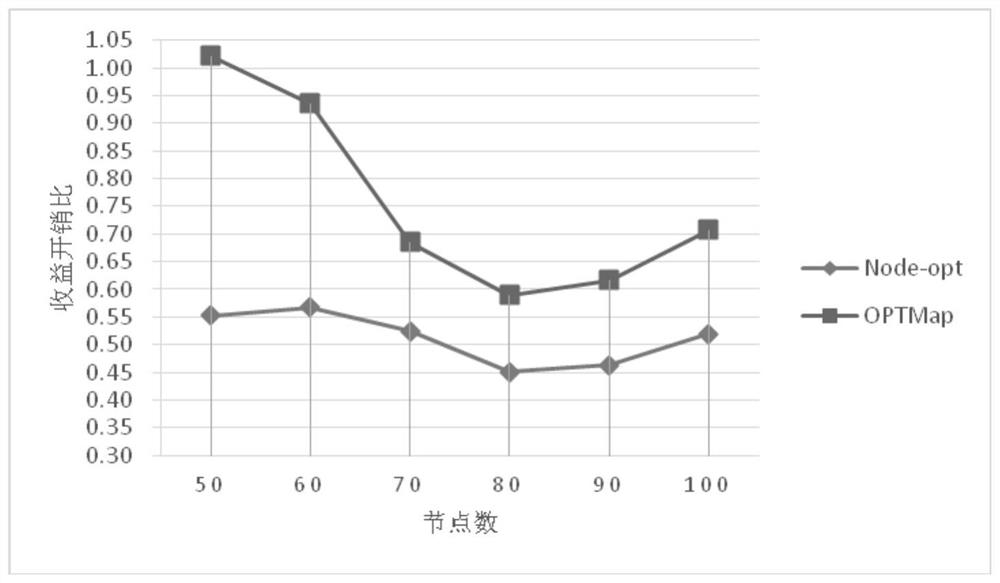
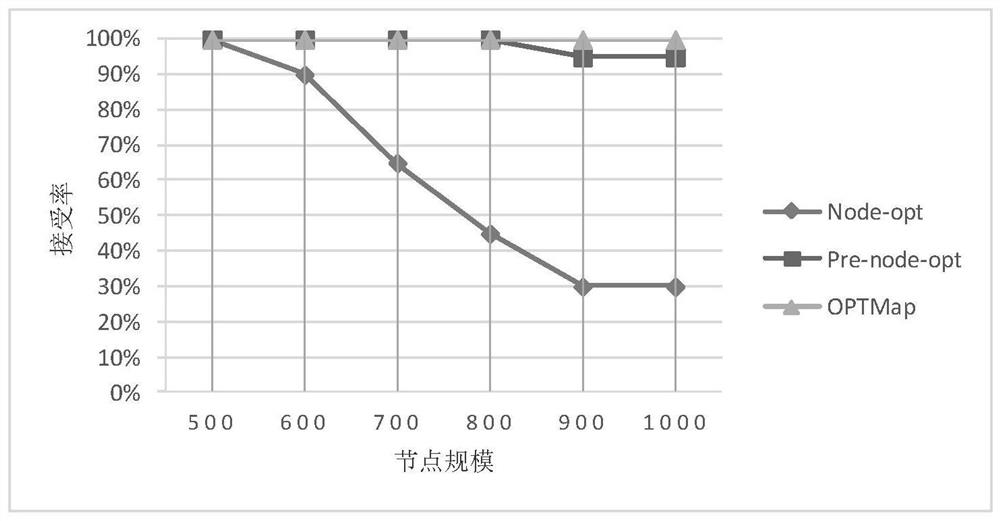
[0025] The present invention mainly proposes a new algorithm OPTMap under the background of the problem of new large-scale virtual network mapping, combining the two ideas of the graph division scheme and the mapping scheme, which first divides the graph and then maps it. Firstly, a simple segmentation is given by using the graph partition method. While ensuring the mapping effect, it is to reduce the number of links, improve the success rate and quality of the mapping process, and avoid complex constraint control. Then, for simple segmentation, a new mapping process is proposed to reflect constraints and pursue a more optimal ratio of revenue to cost.
[0026] Step 1: coarsening the virtual network topology map to obtain the roughened virtual network topology map;
[0027] Step 2: Carry out K-path division to the virtual network t...
specific Embodiment approach 2
[0032] Embodiment 2: The difference between this embodiment and Embodiment 1 is that in the first step, the virtual network topology map is coarsened, and the specific process of obtaining the roughened virtual network topology map is as follows:
[0033] The virtual network topology map is coarsened by using an improved double-edge matching strategy, and the compressed virtual network topology map is obtained.
[0034] Other steps and parameters are the same as those in Embodiment 1.
specific Embodiment approach 3
[0035] Specific embodiment 3: The difference between this embodiment and specific embodiments 1 or 2 is that in the step 2, the virtual network topology graph roughened in step 1 is divided into K paths to obtain a virtual network divided into K parts The specific process of the topology map is:
[0036] The first is the process of graph partitioning, which is called the preprocessing process based on multi-layer K-path partitioning. Divided into three stages. The first is the coarsening stage. The goal of the coarsening stage is to compress the size of the virtual network topology graph. By continuously merging the vertices and edges in the virtual network topology graph, the large graph is transformed into a sufficiently small graph. Based on the improved multiple edge matching Strategy.
[0037] Then there is K-way division. The goal of this step is to divide the virtual network topology map obtained in the coarsening stage into K parts. The sum of the link weights is th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com