Link establishing method of hidden service
A link establishment and link technology, which is applied in the field of link establishment of hidden services, can solve the problems of complex link structure and no obvious improvement in communication efficiency, and achieve the effects of reducing transmission delay, reducing the number of times, and reducing the burden.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with specific embodiment:
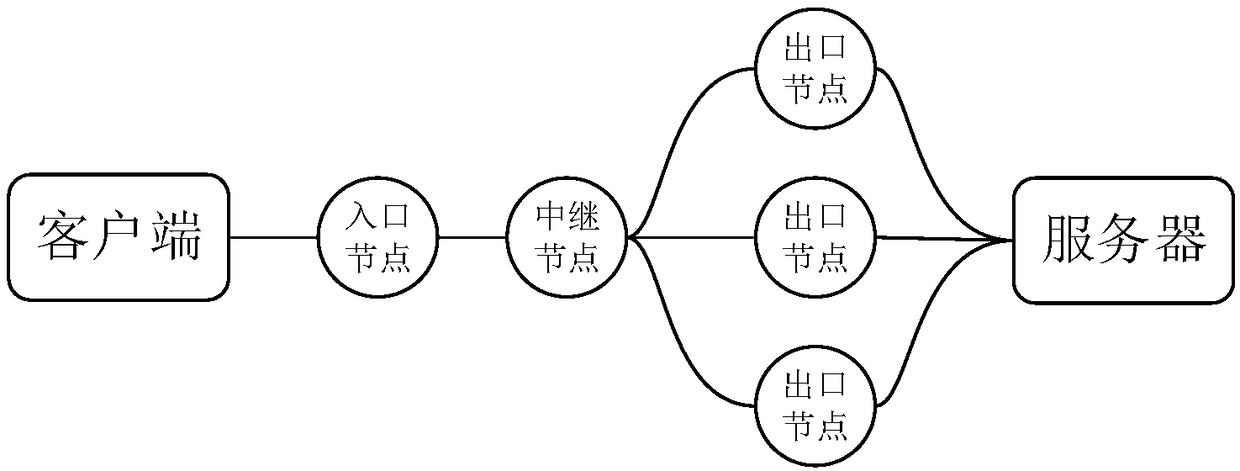
[0031] A hidden service link establishment method described in this embodiment: including hidden service deployment and link establishment, so as to connect the client and the server;
[0032] Among them, the specific steps of hidden service deployment are as follows:
[0033] SA-1. The server generates a pair of keys for the hidden service;
[0034] SA-2. Select 3 nodes as introduction nodes;
[0035] SA-3. The server establishes a connection with the introducing node, and sends a relay establishment instruction to each node;
[0036] SA-4. After the introduction node verification is successful, send the corresponding command to the server;
[0037] SA-5. The server generates a hidden service descriptor for the hidden service, including the public key corresponding to the hidden service, the secret id part, the release time, the protocol version, the list of introducing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com