A Malicious Encrypted Traffic Identification Method Based on Machine Learning
A traffic identification and machine learning technology, applied in character and pattern recognition, instruments, computer components, etc., can solve the problems of unable to identify encrypted traffic, unable to match, unable to extract features, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
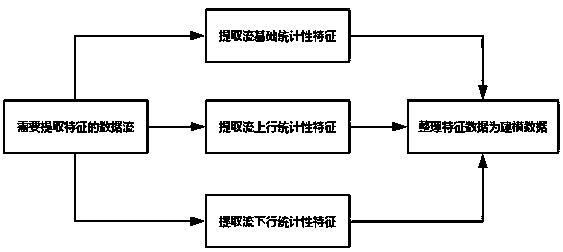
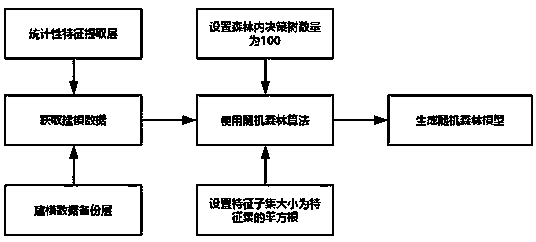
[0018] The present invention is mainly used for identification of malicious encrypted traffic. The sources of malicious traffic identified include malicious attack software, scanning software, phishing websites, Trojan viruses, malicious mining machines, etc. Since the data used in modeling is the statistical characteristics of traffic, the model According to the data samples, the statistical laws of malicious encrypted traffic can be mastered, not only known malicious encrypted traffic can be identified, but also unknown new malicious traffic can be identified.
[0019] The technical framework of the invention will be described below in conjunction with the accompanying drawings.
[0020] figure 1 Invented technical process framework
[0021] Figure 1 It is a technical framework diagram of the present invention, which adopts a layered model framework. Each layer has a different function, and the input of each layer is derived from the output of the previous layer. The in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com