Protection system for safety communication of KNX (Konnex) bus equipment
A bus device and protection system technology, applied in the field of communication security, can solve the problems of losing control of KNX bus devices and user data loss, etc., to achieve the effect of ensuring data transmission security and user privacy, and improving data security levels
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
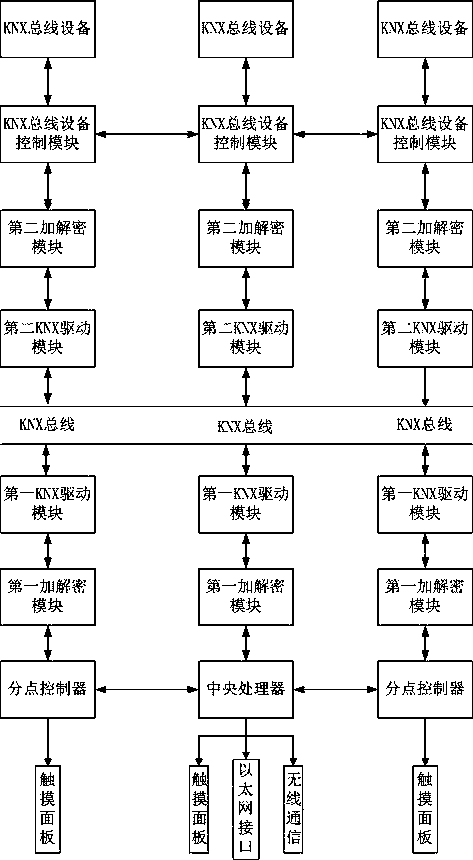
[0042] figure 1 A kind of protection system for KNX bus device safety communication, it is characterized in that, described protection system comprises some KNX bus devices, some KNX bus device control modules, some first encryption and decryption modules, some second encryption and decryption modules, some first A KNX drive module, several second KNX drive modules, a central controller, several point controllers and a KNX bus, wherein:
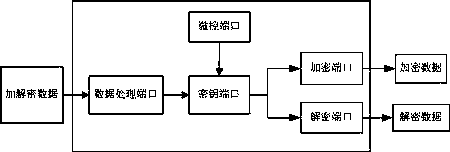
[0043] The encryption and decryption module includes: a data processing port, a key port, an encryption port and a decryption port, wherein:
[0044] The output end of the data processing port is connected to the input end of the key port;
[0045] The output end of the micro-control port is connected to the input end of the key port;
[0046] The output end of the key port is connected to the encryption port and the decryption port respectively.
[0047] It is used to encrypt the communication data between the controller and the KNX bus d...
Embodiment 2
[0064] figure 2 It is an encryption and decryption module used for the protection system of KNX bus device security communication, including data processing port, key port, micro control port, encryption port and decryption port, among which:
[0065] The data processing output end is connected with the key port input end;
[0066] The output end of the micro-control port is connected with the input end of the key port;
[0067] The output end of the key port is respectively connected with the input end of the encryption port and the input end of the decryption port.
[0068] Embodiment 2 specific implementation process:
[0069] The encryption and decryption module obtains the encryption and decryption data from the system, and processes the data before encryption according to the given data to ensure that each encrypted data bit is 256 bits. The key is then generated by the random number generator of the microcontroller or a custom key is generated by other key algorithm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com