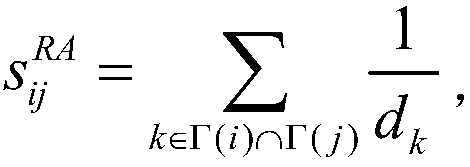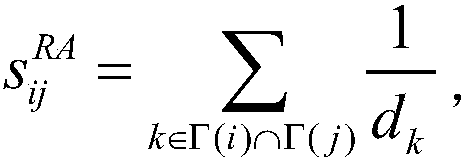Social relationship hiding method based on attack node similarity
A technology of social relations and attacking nodes, which is applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as hidden failures, lower key link recognition rates, and lower accuracy of link prediction algorithms to achieve good concealment effects Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described below in conjunction with the accompanying drawings.
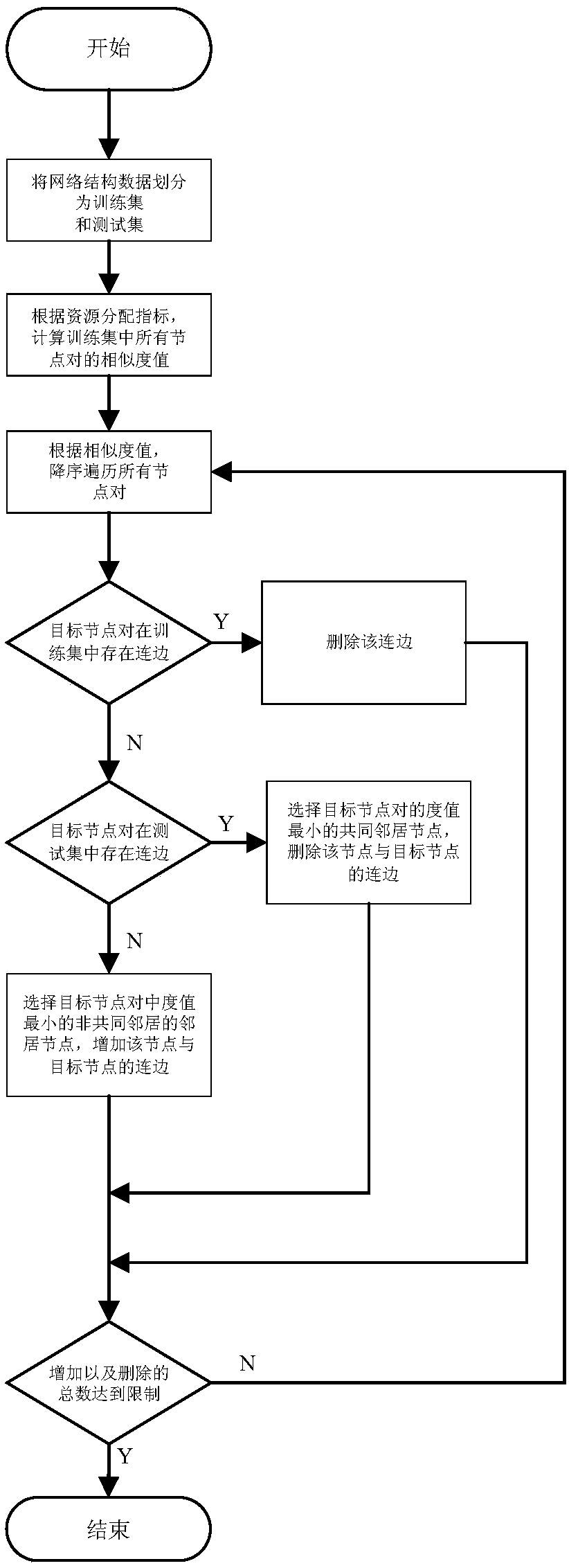
[0020] refer to figure 1 , a social relationship concealment method based on the similarity of attacking nodes, including the following steps:
[0021] S1: Assuming an unweighted and undirected network G(V,E), divide the network structure data into a training set G T and the test set G V , where the training set is the disturbance object, and the test set is used to evaluate the effectiveness of the algorithm, that is, the link prediction accuracy and AUC are used to measure the effect of specific disturbances and random disturbances;
[0022] S2: According to the resource allocation index RA, calculate the similarity value of all node pairs (i, j) in the training set The resource allocation metrics are defined as follows:
[0023]
[0024] where Γ(i) represents the neighbor set of node i, d k Indicates the degree value of node k;
[0025] S3: In order to ens...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com