A memory detection device and method based on android virtual container
A virtual container and memory detection technology, which is applied in computer security devices, instruments, calculations, etc., can solve the problems of false positives, failure to detect malicious code, and high detection rate of common applications, achieving a high detection rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
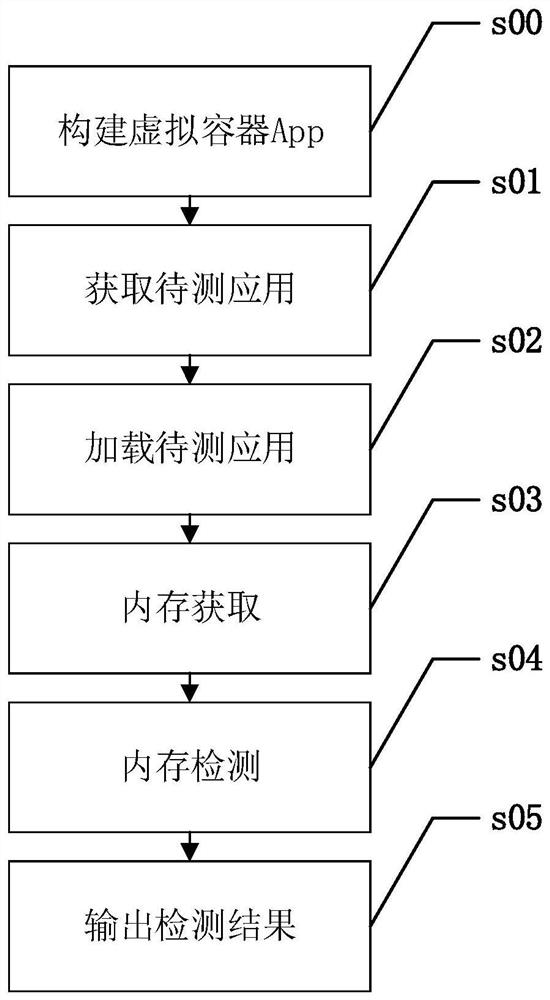
[0041] The present invention will be further described below in conjunction with specific examples and accompanying drawings.
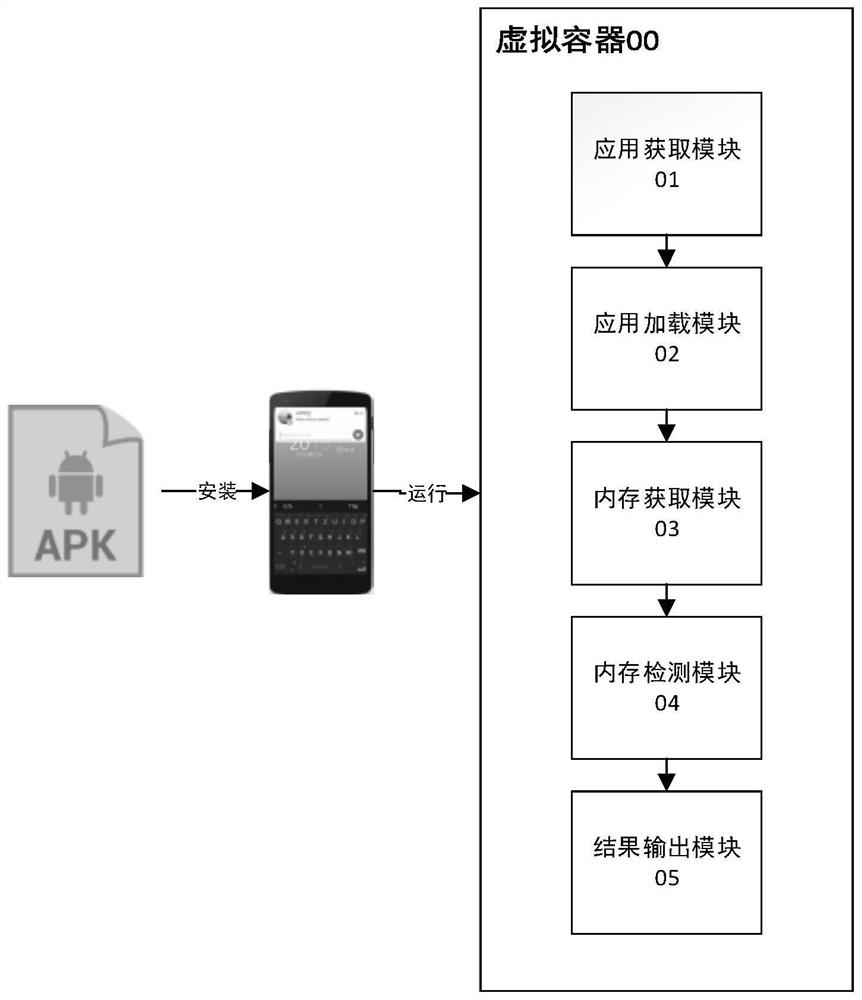
[0042] The present invention provides a memory detection device based on an Android virtual container, such as figure 1 As shown, it is located in a virtual container 00, and the virtual container 00 is located at the Android application layer and is isolated from the real system environment. This device includes:
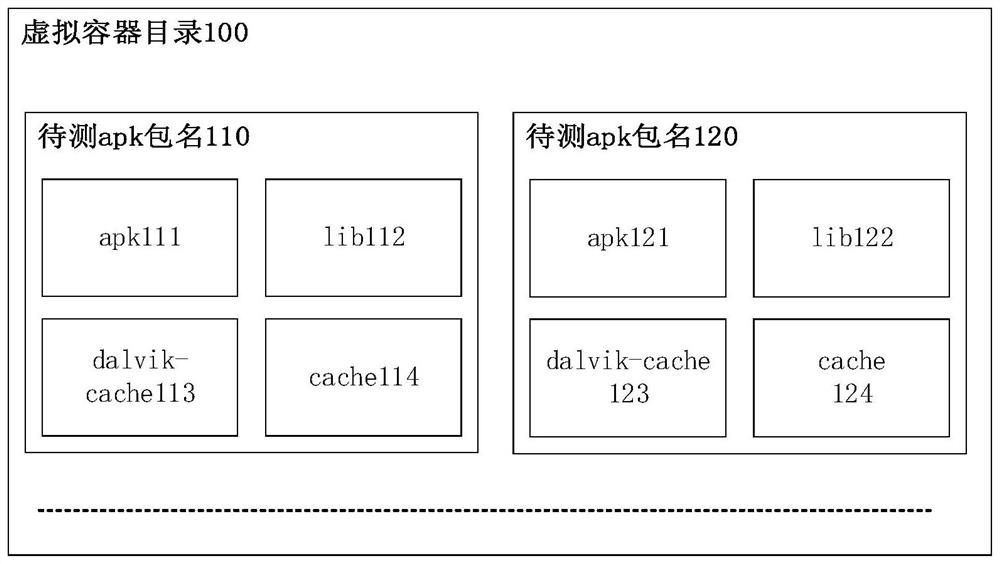
[0043] The application acquisition module 01 is used to acquire and parse the apk file in the external memory.
[0044] The application loading module 02 is used to load and run the apk file. The application loading module 02 mainly includes a code loading module and a resource loading module; the code loading module is used to create Application and Activity to be tested; the resource loading module is used to load the application resources to be tested, wherein the resources include bitmap files , page layout file, or color file.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com