Management method and device for terminal permission
A management method and authority technology, applied in the direction of unauthorized/fraudulent phone call prevention, electronic digital data processing, instruments, etc., can solve the problems of privacy leakage, low mobile phone security, and affecting the personal and property safety of users, and achieve improvement Technical effect, the effect of solving low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
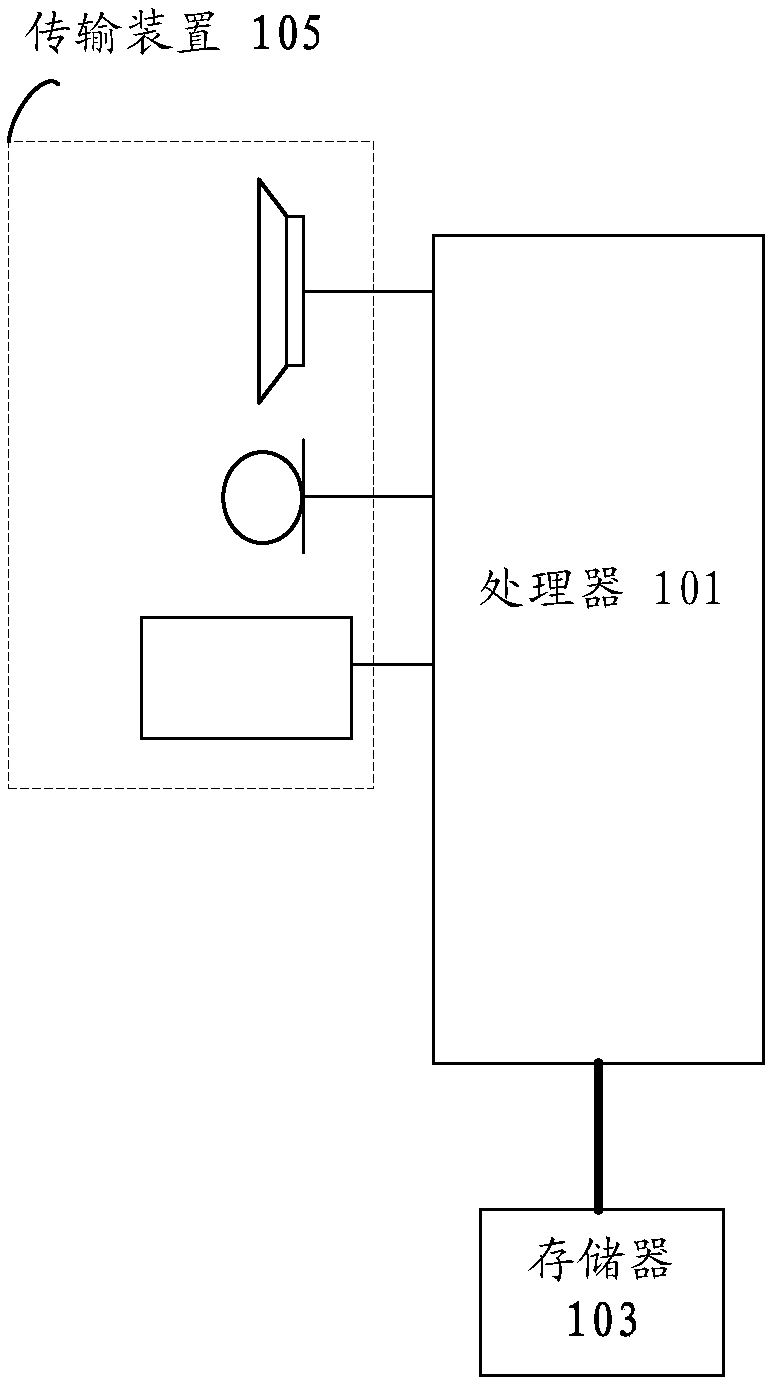
[0029] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal (such as a wearable device, a mobile phone, a tablet computer, etc.), a computer terminal, or a similar computing device. Take running on a mobile terminal as an example, such as figure 1 As shown, the mobile terminal may include one or more (only one is shown in the figure) processors 101 (the processors 101 may include but not limited to processing devices such as microprocessors MCUs or programmable logic devices FPGAs) for storing Data storage 103, and transmission means 105 for communication functions. Those of ordinary skill in the art can understand that, figure 1 The shown structure is only for illustration, and it does not limit the structure of the above-mentioned electronic device.
[0030] The memory 103 can be used to store software programs and modules of application software, such as program instructions / modules corresponding to the control met...
Embodiment 2
[0072] The embodiment of the present invention also provides a device for managing terminal rights. The device is used to implement the above-mentioned embodiments and preferred implementation modes, and what has been described will not be repeated. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
[0073] Figure 4 is a schematic diagram of an apparatus for managing terminal rights according to an embodiment of the present invention. Such as Figure 4As shown, the device may include: a collection unit 41 , a determination unit 42 and an execution unit 43 .
[0074] The collection unit 41 is used to collect the biological characteristics of the terminal user when the mobile terminal is unlocked;
...
Embodiment 3
[0088] The embodiment of the invention also provides a storage medium. Optionally, in this embodiment, the above-mentioned storage medium may be configured to store program codes for performing the following steps:
[0089] S1, when the mobile terminal is unlocked, collect the biological characteristics of the terminal user;
[0090] S2. Determine the user authority of the terminal user on the mobile terminal according to the biometric feature;
[0091] S3. After the mobile terminal is successfully unlocked, perform operations permitted by the user authority.
[0092] Optionally, in this embodiment, the above-mentioned storage medium may include but not limited to: U disk, read-only memory (ROM, Read-Only Memory), random access memory (RAM, Random Access Memory), mobile hard disk, magnetic disk Various media that can store program codes such as discs or optical discs.
[0093] Optionally, in this embodiment, the processor executes according to the program code stored in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com