Vulnerability situation data fusion method
A data fusion and vulnerability technology, applied in the field of network security, can solve the problems of false negatives and false positives, and different detection capabilities of security equipment, and achieve the effect of eliminating inconsistencies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
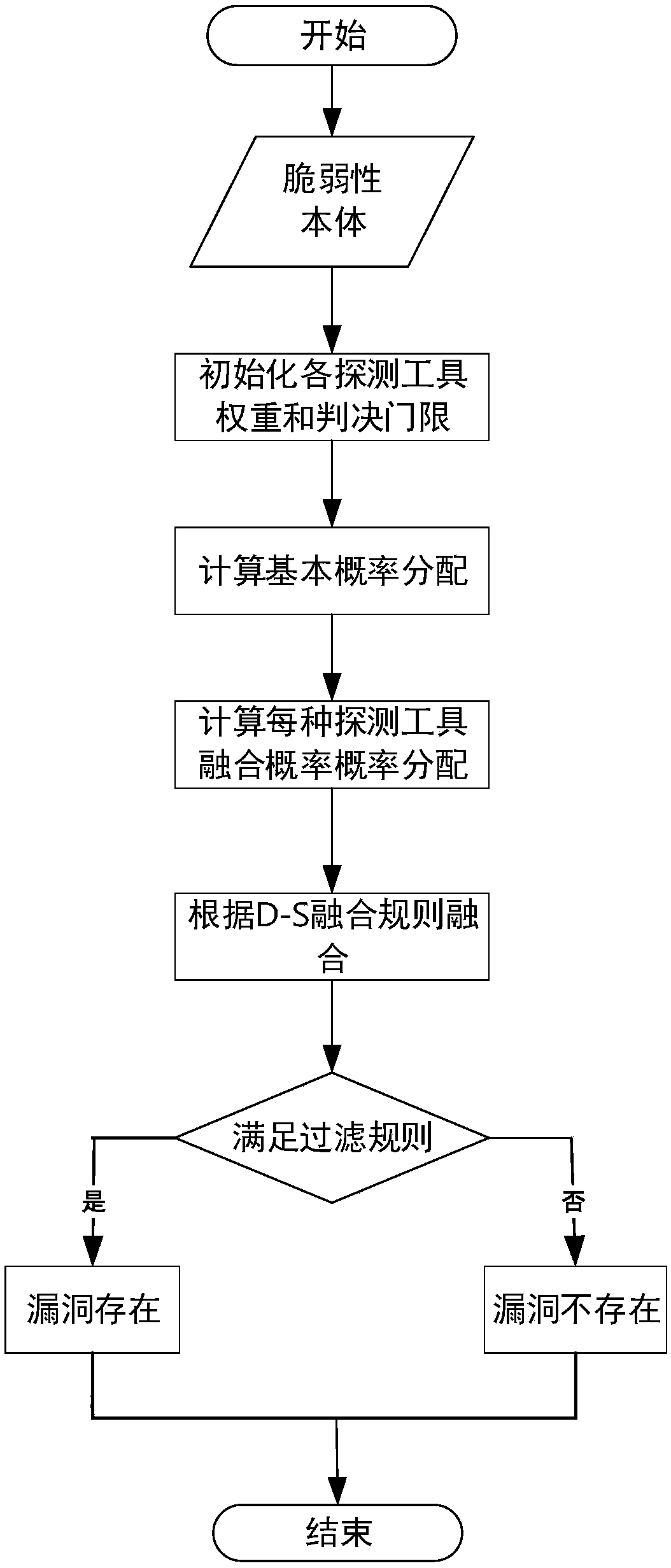
[0055] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in combination with specific examples and with reference to the accompanying drawings.
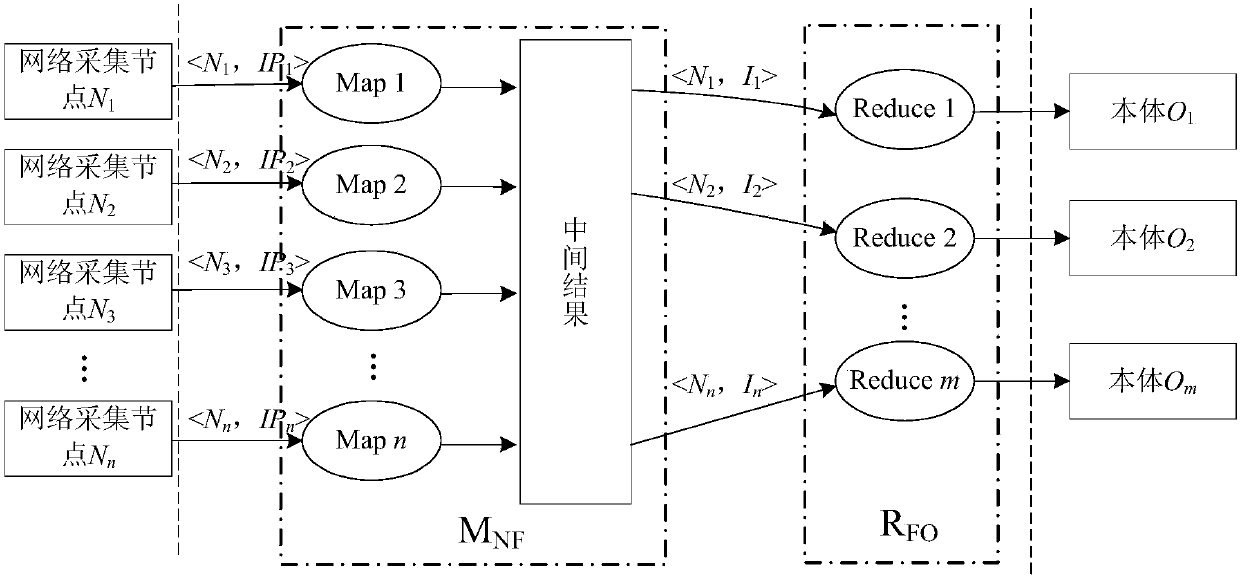
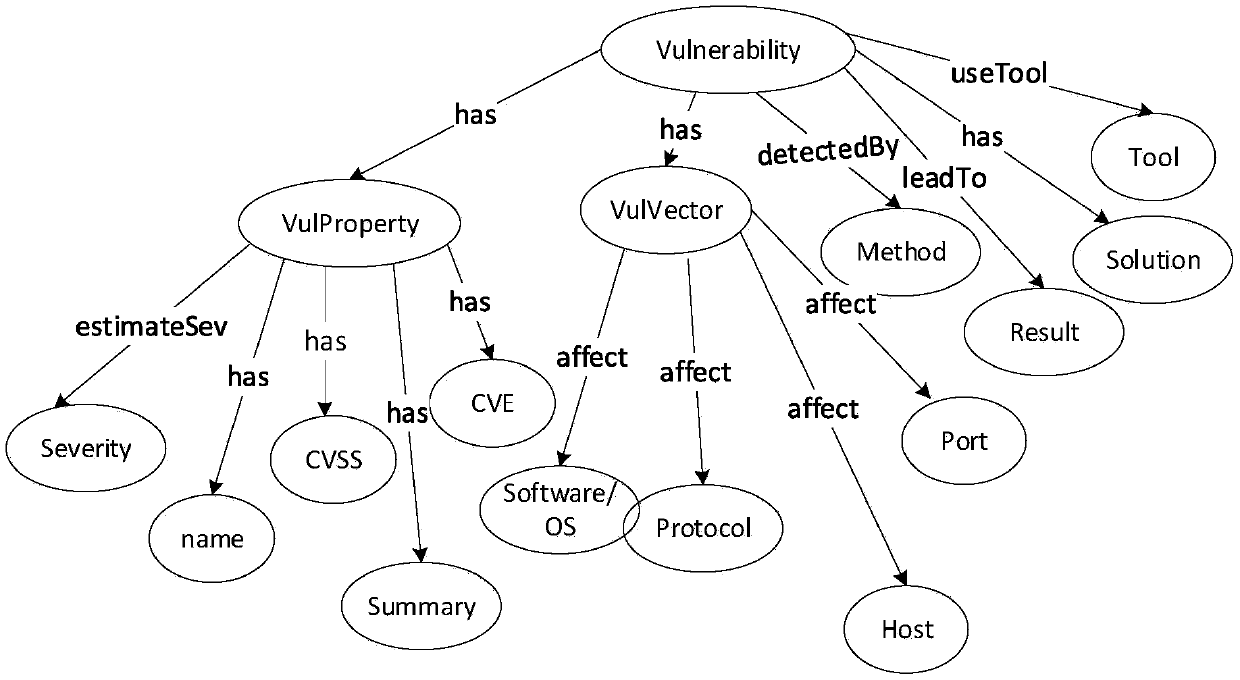
[0056] The experimental data used in this embodiment of a vulnerability situation data fusion method is mainly obtained by scanning network devices, operating systems, databases and application services in the attack environment built by the laboratory through the detection tools OpenVAS and Nessus. This example selects an open source operating system dedicated to testing system vulnerabilities, so there will be more vulnerabilities. The data scanned by the detection tool includes Scan Information (scanning information), HostInformation (host information), Result Summary (total number of results), and Result Details (detailed information of scanning results).
[0057] In order to verify the effectiveness of this method, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com