Connection method and system based on workload proof, client and server
A connection method and workload technology, applied in the Internet field, can solve problems such as economic losses, server crashes, and website crashes, and achieve the effects of controlling the number of connections, increasing costs, and reducing the number of connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
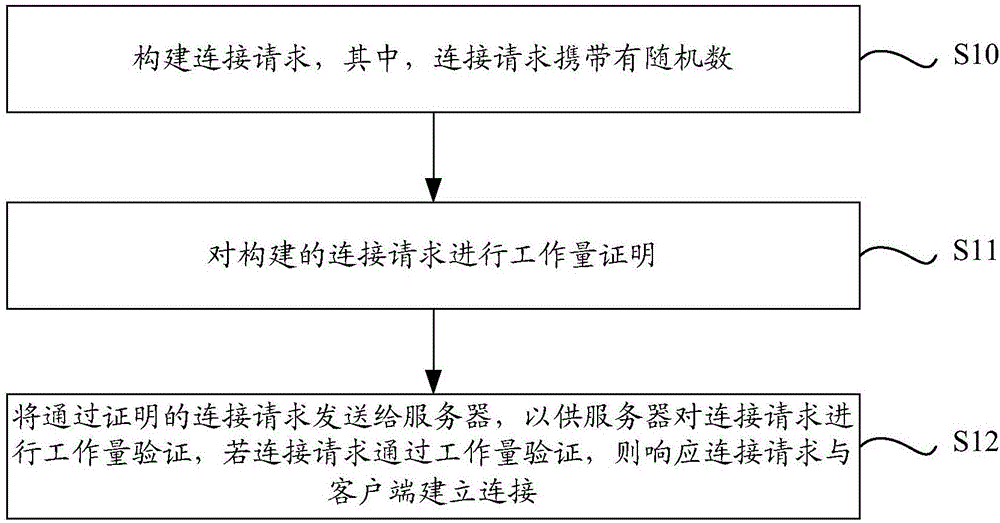
[0065] figure 1 A schematic flowchart of a proof-of-work-based connection method according to Embodiment 1 of the present invention is shown. Such as figure 1 As shown, the method includes the following steps:
[0066] Step S10, constructing a connection request, wherein the connection request carries a random number.
[0067] Specifically, the client may include a random number generator, use the random number generator to randomly generate a random number, and then use the generated random number to construct a connection request, that is, the connection request carries a random number, wherein the connection request Can be http request.
[0068] Of course, the client can store a random number set locally, and the client can select a random number from the random number set each time, and then use the selected random number to construct a connection request. This is just an example and does not have any limiting effect. .
[0069] In step S11, proof of workload is perfo...
Embodiment 2
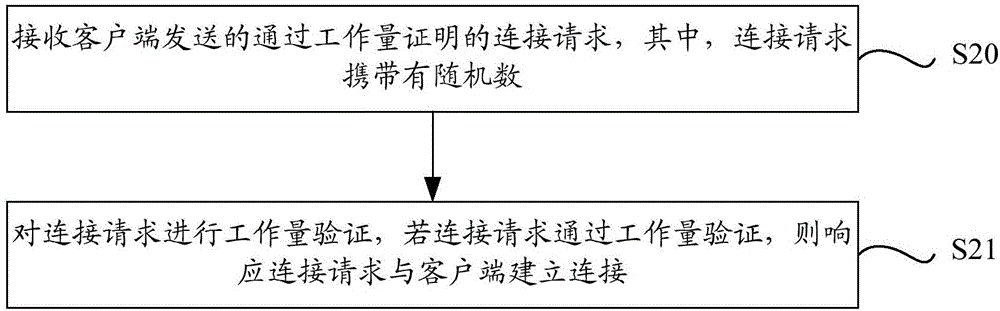
[0078] figure 2 A schematic flowchart of a proof-of-work-based connection method according to Embodiment 2 of the present invention is shown. The execution subject of this method is the server, such as figure 2 As shown, the method includes the following steps:
[0079] Step S20, receiving a connection request through the proof-of-work sent by the client, wherein the connection request carries a random number.
[0080] The client performs proof of work on the connection request constructed. In order to pass the proof of work, the client may need to perform multiple calculations. That is to say, the process of proof of work is a complicated process. Proof, then send the connection request through the workload proof to the server, the connection request carries the random number that meets the workload proof, and the server receives the connection request through the workload proof sent by the client.
[0081] In step S21, workload verification is performed on the connectio...
Embodiment 3
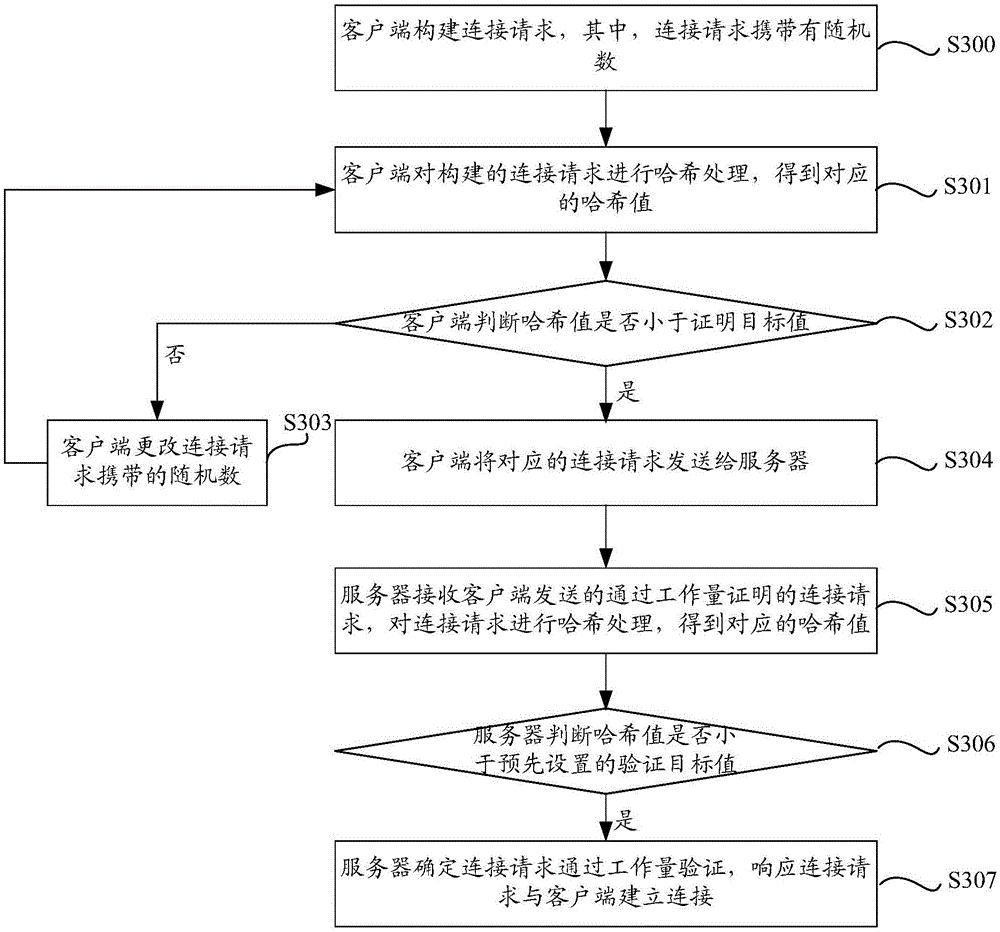
[0085] image 3 A schematic flowchart of a proof-of-work-based connection method according to Embodiment 3 of the present invention is shown. Such as image 3 As shown, the method includes the following steps:
[0086] Step S300, the client constructs a connection request, wherein the connection request carries a random number.
[0087] Specifically, the client may include a random number generator, use the random number generator to randomly generate a random number, and then use the generated random number to construct a connection request, that is, the connection request carries a random number, wherein the connection request Can be http request.
[0088] Of course, the client can store a random number set locally, and the client can select a random number from the random number set each time, and then use the selected random number to construct a connection request. This is just an example and does not have any limiting effect. .
[0089] In step S301, the client perf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com