Network security incident correlation method
A security event and event correlation technology, applied to electrical components, transmission systems, etc., can solve problems such as unexplainable classification results, system performance degradation, and impact on system execution efficiency, and achieve the effect of easy deployment and maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
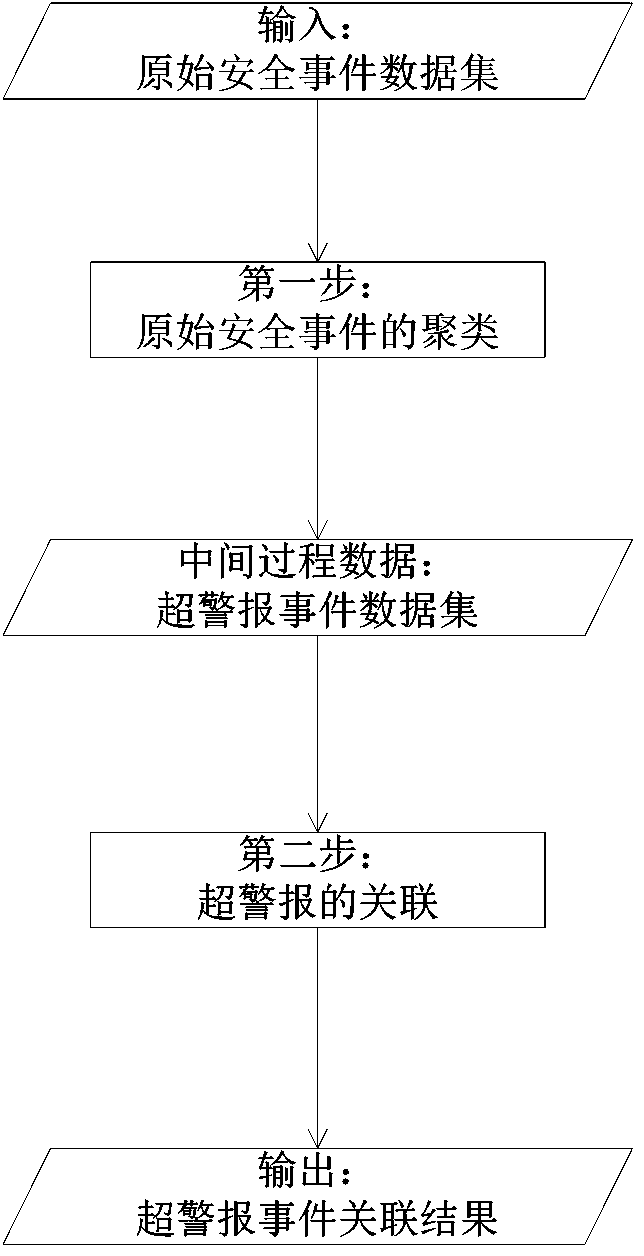
[0061] The invention discloses a method for correlating network security events, which is a similarity calculation method based on an attribute classification tree, and mainly realizes correlation in two steps.
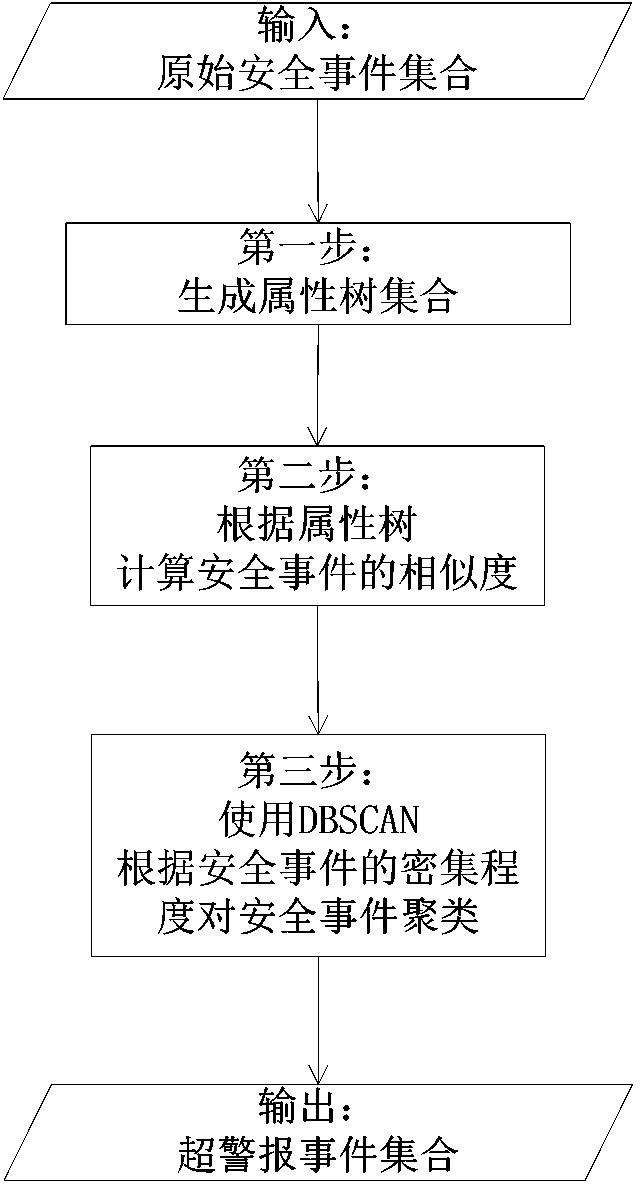
[0062] In the first step, the original security event is classified by one-step alarm to obtain super-alert information.
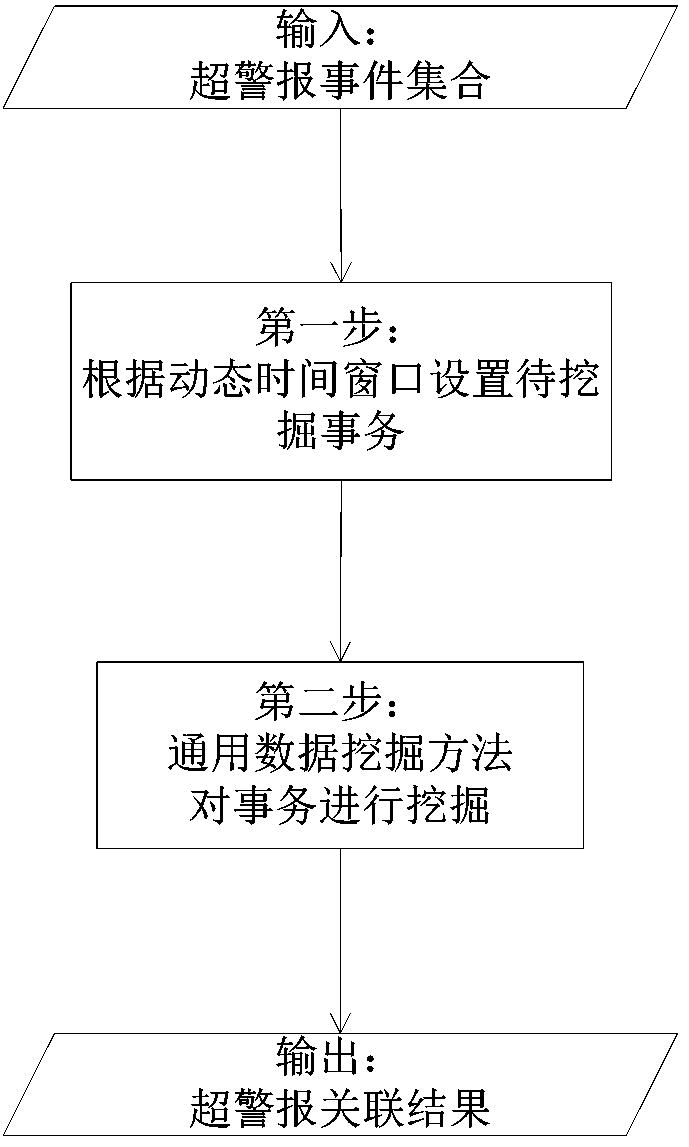
[0063] The second step is to merge the super-alarm information obtained through the classification of the first step, and obtain a set of super-alarm events with strong correlation for each combination.
[0064] The method of the present invention is realized based on the following principles: a network attack can be decomposed into several attack steps, and each network attack constitutes a step in the attacker's larger attack plan, and a specific attack step can be recorded by numerous intrusion detection alarms constitute.
[0065] The event correlation method based on similarity mainly considers to correlate the original security events throu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com