Security isolation method for modules in ARM platform
A security isolation and platform technology, applied in the direction of platform integrity maintenance, internal/peripheral computer component protection, etc., can solve the problems of Linux system implementation differences and inapplicability, and achieve the effect of improving safety reliability and ensuring reliability and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
[0027] The present invention is a solution based on the Linux system. The names of the existing system calls, structures and functions involved are all customarily used in English in this field. Confused; and these names have specific meanings in the Linux system, and technicians can clarify the content represented by each name without misunderstanding. Therefore existing in the Linux system involved in the present invention, the name that does not have recognized Chinese translation all uses English expression.
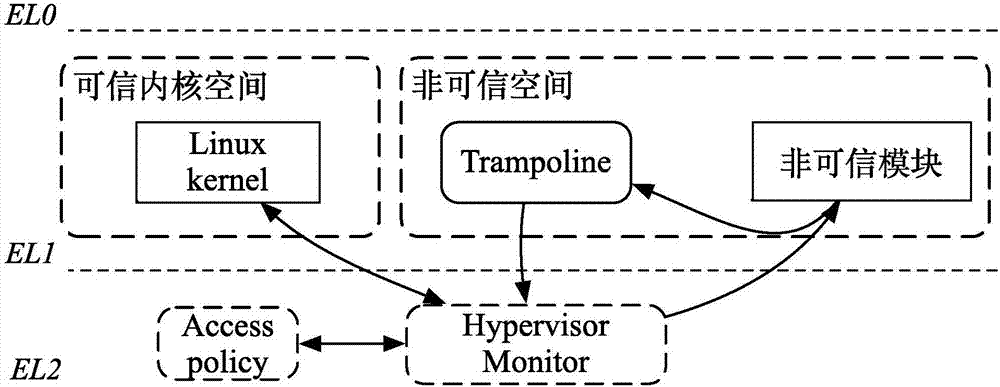
[0028] The present invention provides a module safety isolation method on an ARM platform, the steps of which are:
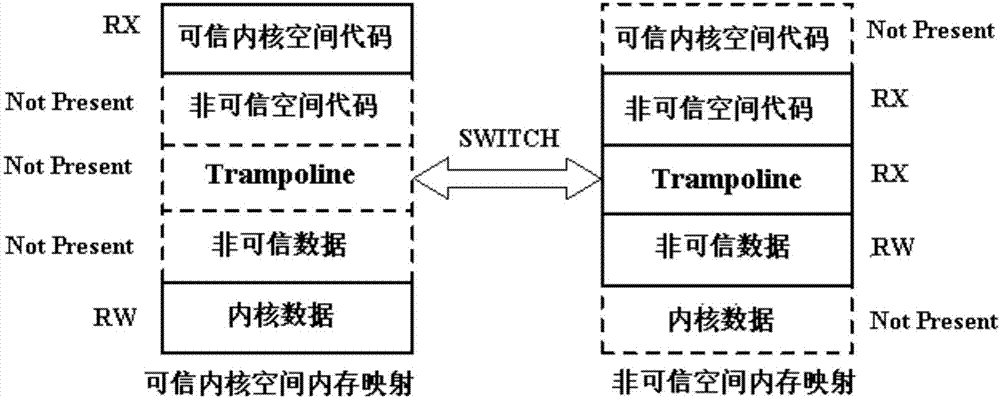
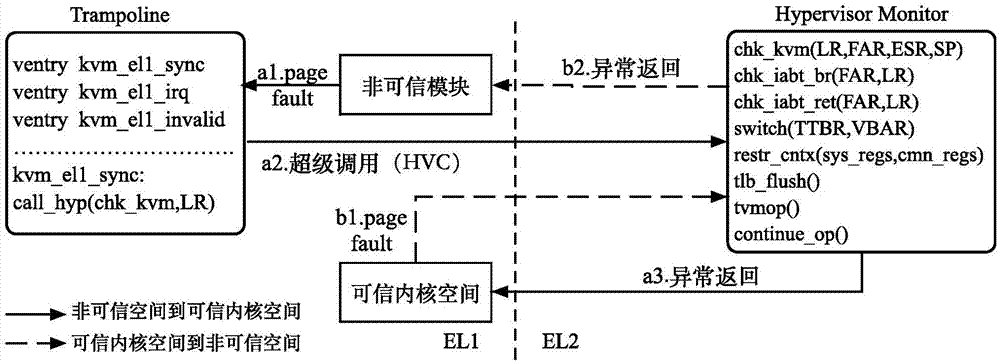
[0029] 1) According to the virtual memory layout, the Linux kernel space is divided to isolate the virtual address space, and the L...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com