Terrorist organization network mining algorithm
A technology of mining algorithms and organizing networks, which is applied in the field of computer networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in further detail below.
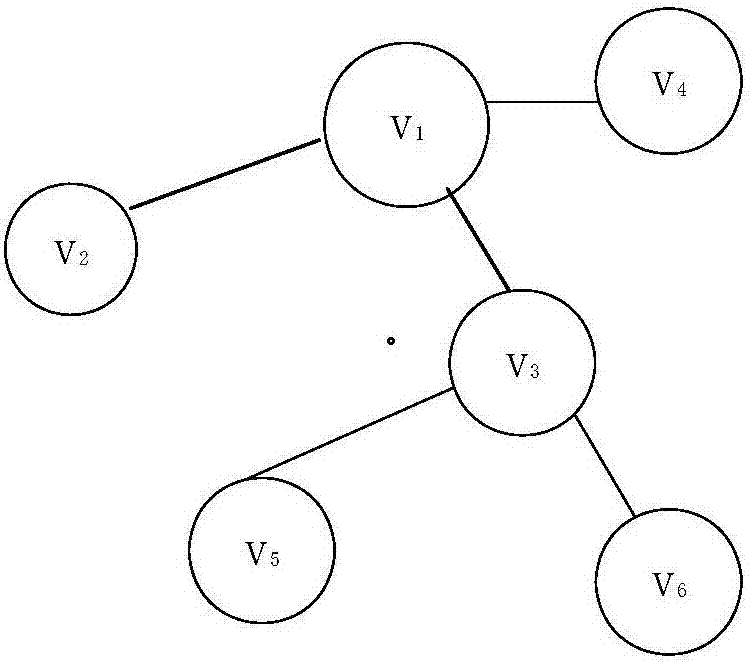
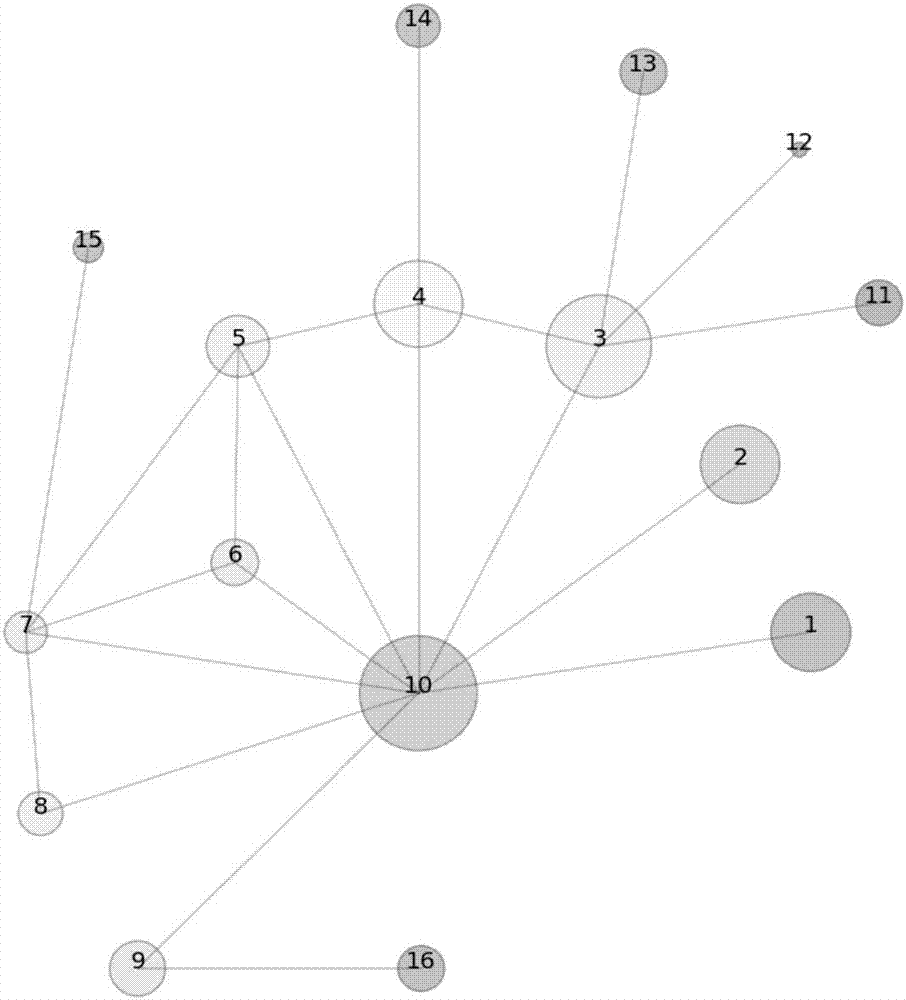
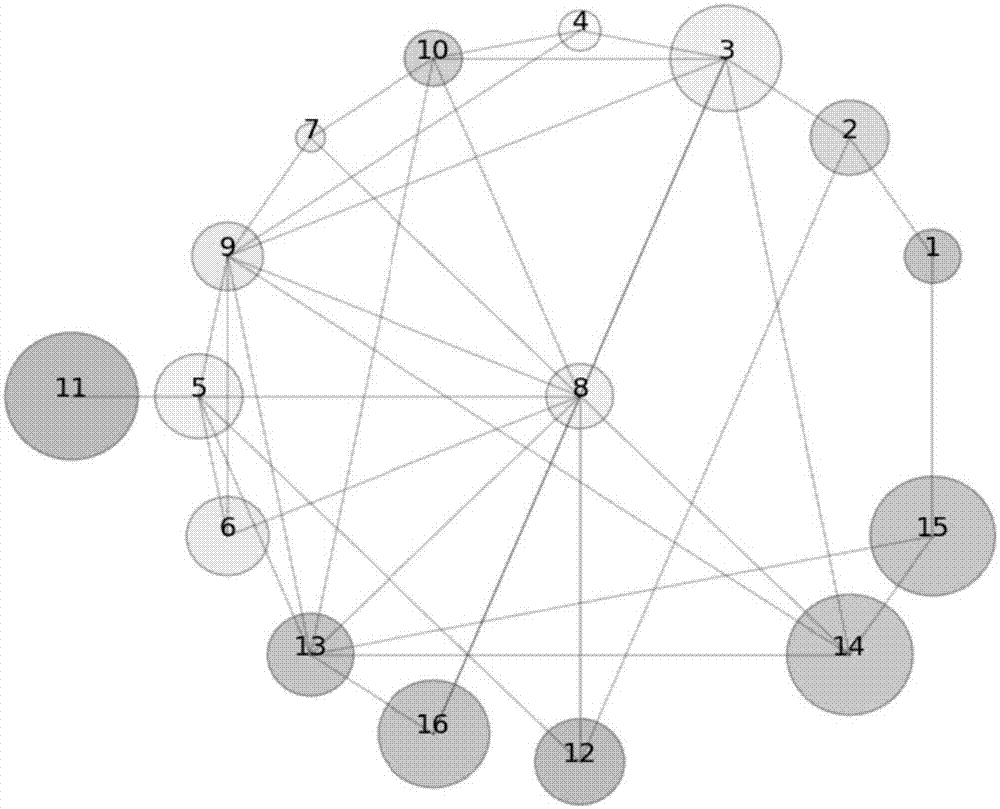
[0039] Random set evidence reasoning has a strong ability to deal with dynamic uncertain information. The biggest feature of its method of dealing with problems is that it retains all known information and directly participates in quantitative calculations, which can minimize accumulated errors. Furthermore, no artificial assumptions have been made other than the raw data, in order to be as faithful as possible to the information presented. Therefore, it has become a powerful tool for analyzing the random dynamic information of the terrorist organization network. The concept of topological potential is proposed based on data field theory in cognitive physics. The size of the topological potential describes the potential value of a node in the network topology under the joint influence of itself and neighboring nodes, and can describe its ability to influence other nodes. As a powerful tool for network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com