Identity verifying method and mobile terminal
A technology for identity verification and mobile terminals, applied in the field of identity verification and mobile terminals, can solve problems such as inability to balance security and user experience, and achieve the effect of overcoming the inability to balance security and user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
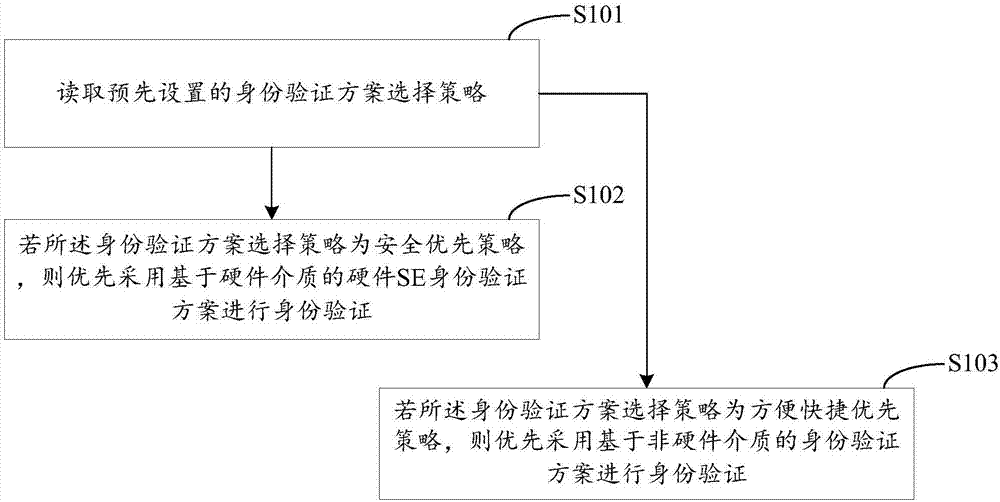
[0077] figure 1 It shows a schematic flow of the identity verification method provided by Embodiment 1 of the present invention, which is applied to a mobile terminal, and is described in detail as follows:
[0078] In step S101, a preset policy for selecting an identity verification scheme is read.
[0079] In the embodiment of the present invention, an identity authentication scheme selection strategy may be preset, and the identity authentication scheme selection strategy includes a security priority selection strategy and a convenience and quickness priority strategy. Before identity verification, the mobile terminal can read the identity verification scheme selection policy, and use different identity verification schemes for identity verification according to the identity verification scheme selection policy.
[0080] In step S102, if the authentication scheme selection strategy is a security priority strategy, the hardware medium-based hardware SE authentication scheme...
Embodiment 2
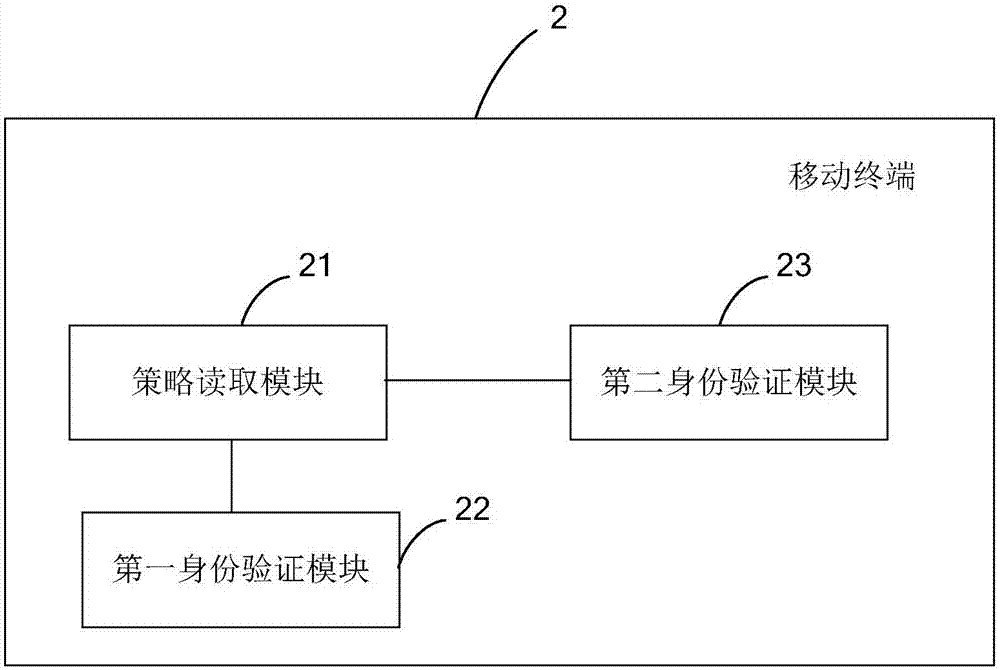
[0097] figure 2 A schematic block diagram of the mobile terminal 2 provided by Embodiment 2 of the present invention is shown, and for convenience of description, only parts related to the embodiment of the present invention are shown. The mobile terminal 2 includes: a policy reading module 21 , a first identity verification module 22 and a second identity verification module 23 .
[0098] Wherein, the strategy reading module 21 is used to read the preset identity verification scheme selection strategy;
[0099] The first identity verification module 22 is configured to preferentially adopt a hardware SE identity verification scheme based on a hardware medium for identity verification if the identity verification scheme selection strategy is a security priority strategy;
[0100] The second identity verification module 23 is configured to preferentially adopt an identity verification plan based on non-hardware media for identity verification if the identity verification sche...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com