Unlocking method and device and terminal
An unlocking and password technology, which is applied in the field of smart device security, can solve problems such as unfavorable device information security, device production cost and battery life impact, and easy to be copied, so as to save energy, improve battery life, and improve unlocking security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
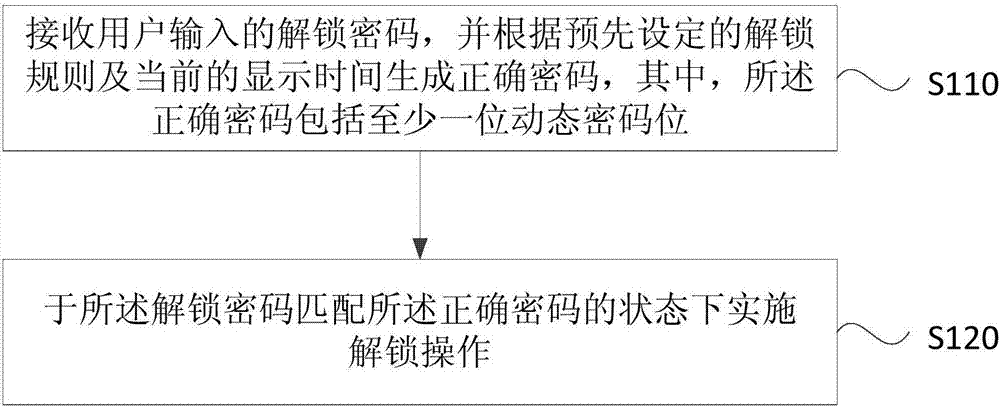
[0071] figure 1 It is a flow chart of the unlocking method provided in Embodiment 1 of the present invention. This embodiment is applicable to the password setting and password unlocking of the terminal. The method can be executed by the unlocking device provided in the embodiment of the present invention. The device can It is realized by means of software and / or hardware, and can be integrated into a terminal with locking and unlocking functions.
[0072] Such as figure 1 As shown, the unlocking method includes:
[0073] S110. Receive an unlocking password input by the user, and generate a correct password according to a preset unlocking rule and a current display time, wherein the correct password includes at least one dynamic password bit.
[0074] There are many ways for the user to input the unlocking password, which may be by pressing a physical button or a button on the touch screen, or speaking the unlocking password through a voice command.
[0075] The preset unlo...
Embodiment 2
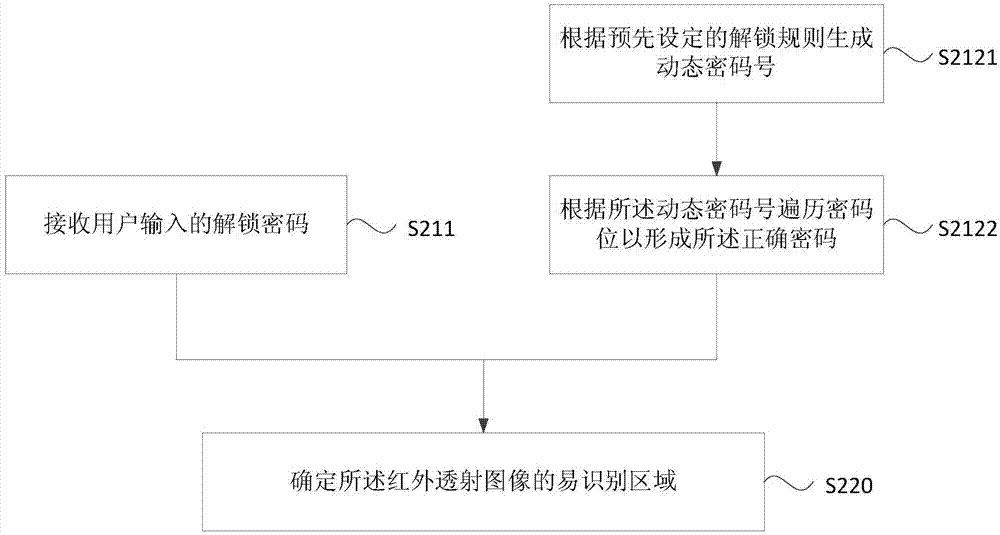
[0084] figure 2 It is a flow chart of the unlocking method provided by Embodiment 2 of the present invention. On the basis of the above-mentioned embodiments, this embodiment optimizes the generation of the correct password according to the preset unlocking rules and the current display time.
[0085] Such as figure 2 As shown, the unlocking method includes:
[0086] S211. Receive an unlock password input by the user.
[0087] S2121. Generate a dynamic password number according to a preset unlocking rule.
[0088] Wherein, the preset unlocking rule can use time as the data reference value, and the time mentioned here includes date and time, for example, at 19:30 on August 8, 2008, in addition, it can also use the week as the reference value. Reference value, select different reference values, and then use different unlocking rules to obtain a dynamically changing password number.
[0089] S2122. Traverse the password bits according to the dynamic password number to form...
Embodiment 3
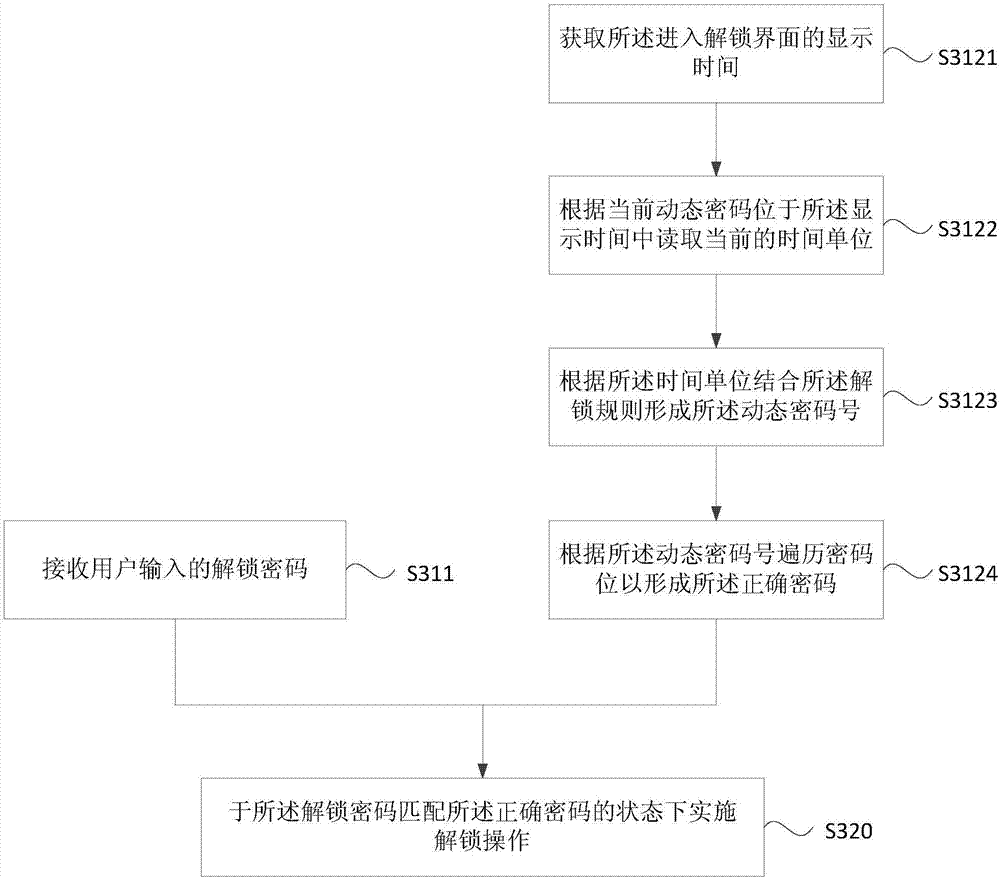
[0095] image 3 It is a flow chart of the unlocking method provided by Embodiment 3 of the present invention. In this embodiment, on the basis of the above embodiments, the dynamic code number is optimized according to the preset unlocking rules.
[0096] Such as image 3 As shown, the unlocking method includes:
[0097] S311. Receive an unlock password input by the user.
[0098] S3121. Obtain the display time of entering the unlocking interface.
[0099] Different terminals have different ways to enter the unlock interface, for example, it may be a way of clicking an unlock button, or a way of sliding the screen to enter the unlock interface. Obtaining the time displayed on the terminal when entering the unlocking interface can avoid the phenomenon that the user cannot unlock normally because the time changes during the unlocking process.
[0100] S3122. Read the current time unit according to the current dynamic password located in the display time.
[0101] When the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com