Decentralized user identification method and system in smart home
A user identification and decentralization technology, applied in transmission systems, home automation networks, data exchange through path configuration, etc., can solve problems such as low security and easy information leakage, and achieve flexibility and security. high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
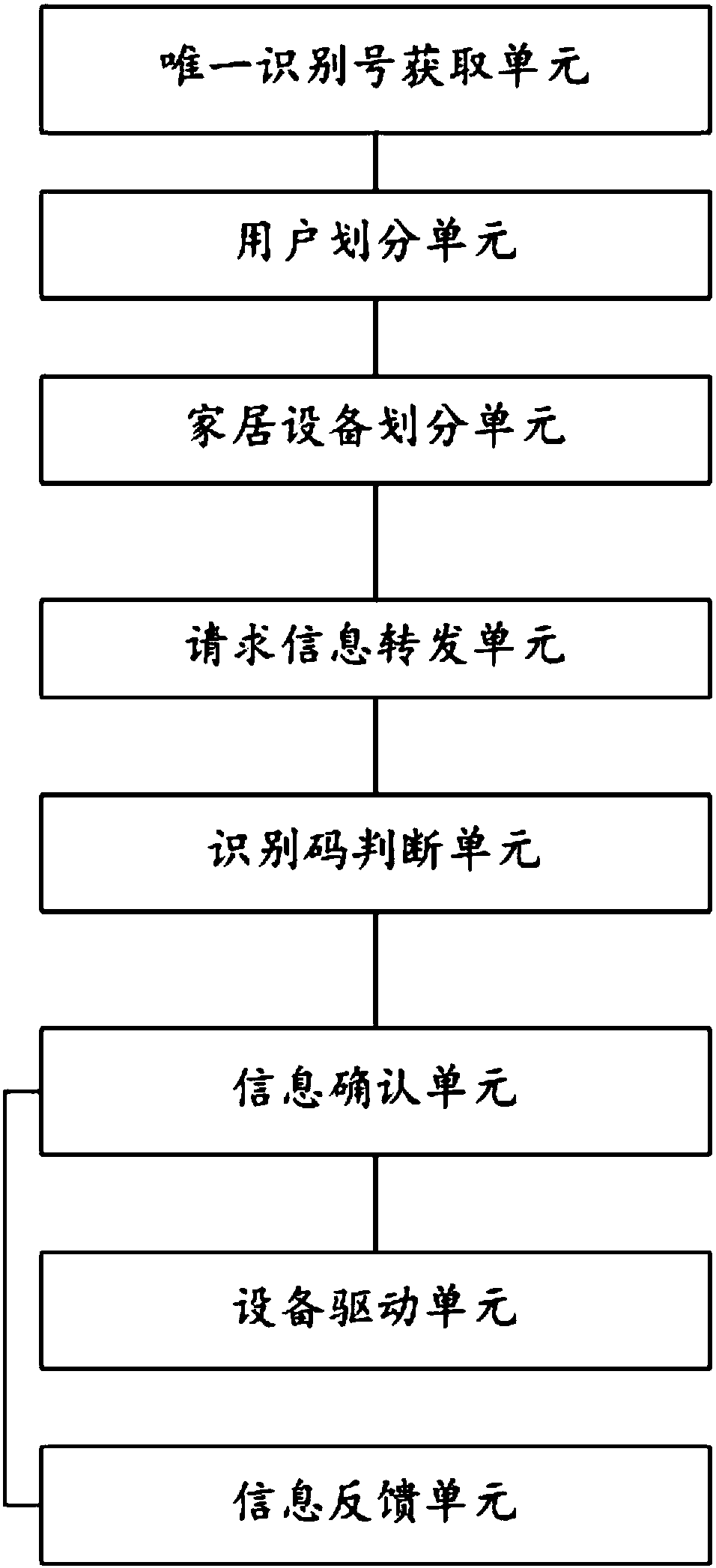
[0036] In an embodiment of the present invention, a decentralized user identification method in a smart home includes the following steps:
[0037] S1. Obtain in advance the unique identification numbers of each smart terminal corresponding to each home user; generate a list of the unique identification numbers of all smart terminals and distribute them to each smart terminal after encryption;
[0038] S2. Classify users according to their status in the family; the grades are divided into four levels: high, medium, low, and temporary; each user corresponds to a corresponding smart terminal;
[0039] S3. Classify the importance of the smart home equipment, and divide the importance into four levels: high level, medium level, low level, and public equipment.
[0040] For example, the importance level of safes and specific information storage devices can be set to a high level, and equipment with high risk factors such as water heaters and gas can be divided into high levels, whi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com