Block chain real-time polling cloud side system
A block chain, cloud technology, applied in the field of anti-counterfeiting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
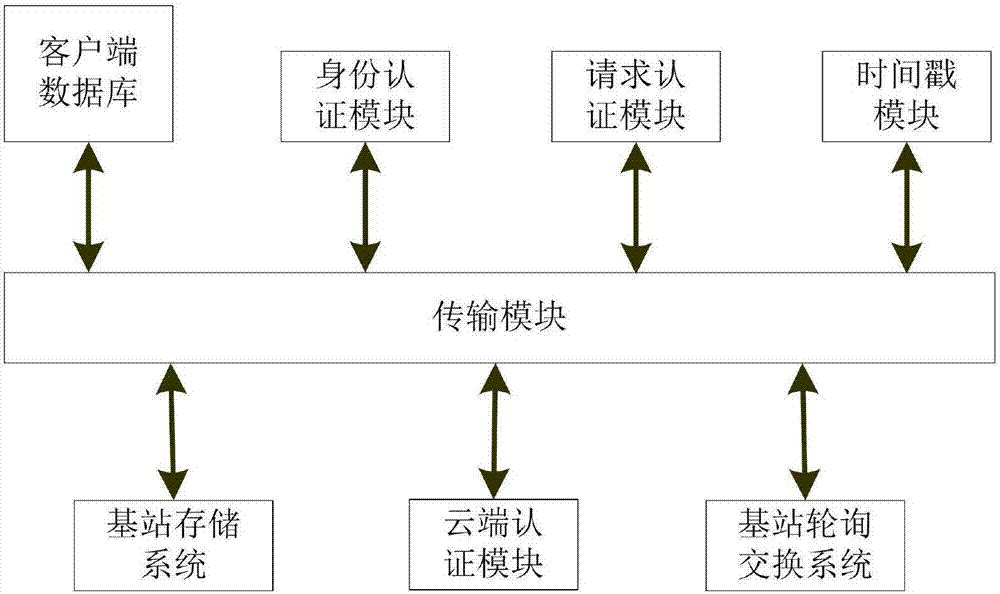
[0023] Embodiment one: if figure 1 Shown: In practice, the base station polling exchange system receives the location area and identity information of the blockchain user; according to the blockchain user ID carried in the location area and identity information, it is authenticated from the blockchain user cloud stored in the base station storage system In the information, to query the blockchain user ID corresponding to the cloud authentication information of the blockchain user;
[0024] The cloud authentication module collects the cloud authentication information of all blockchain users in each region; generates cloud authentication information of blockchain users based on the cloud authentication information of all blockchain users in each region, so as to reduce the calculation amount of concurrent authentication , and store the blockchain user cloud authentication information to the cloud authentication module; send the queried location area blockchain user cloud authentic...
Embodiment 2
[0030] Embodiment two, such as figure 1 Shown: In practice, from the analysis and calculation of the credibility of identity authentication based on the dynamic password and public key cryptosystem and the analysis and calculation of the credibility of the identity authentication based on the cloud of the present invention, the calculation results of the two are compared, and the analysis of the present invention in advantage in credibility. The steps are: set the authentication mechanism, the authentication certificate is composed of the public key, the encrypted identity and the block chain user password; the dynamic password is randomly generated; by comparing the stored block chain user password; the cloud authentication module: assign block chain The user identifies the access entity; identity authentication module: uses the public key and private key distributed by the elliptic curve system to perform key verification, and then verifies the legitimacy of the access entit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com