Software architecture security evaluation method based on theory of evidence combination
A technology of software architecture and architecture, applied to systems based on fuzzy logic, based on specific mathematical models, electrical components, etc., can solve problems such as difficult software dynamic security assessment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
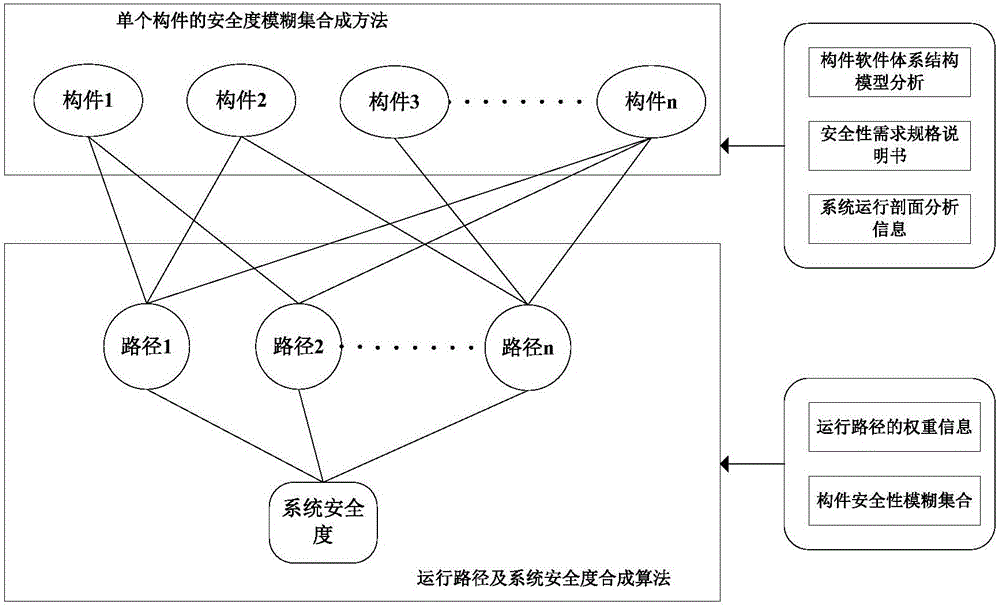
[0178] Taking a flight control system as an example, the architecture model is as follows: Figure 5 As shown, among them, "flight control console" Operating) is the man-machine interface of the flight control system, which has the function of setting the working state of the system by the driver and indicating the working state of the system. The system is composed of stability augmentation / control stability augmentation subsystems (pcs, lcs), automatic flight subsystem (ap_manage) and automatic trim subsystem (pap), and the stability augmentation / control stability augmentation subsystem is a three-redundant configuration (rm); At the same time, the system also has a line control subsystem, mainly the flight status selector (CDS); and several main modules of the system bit.
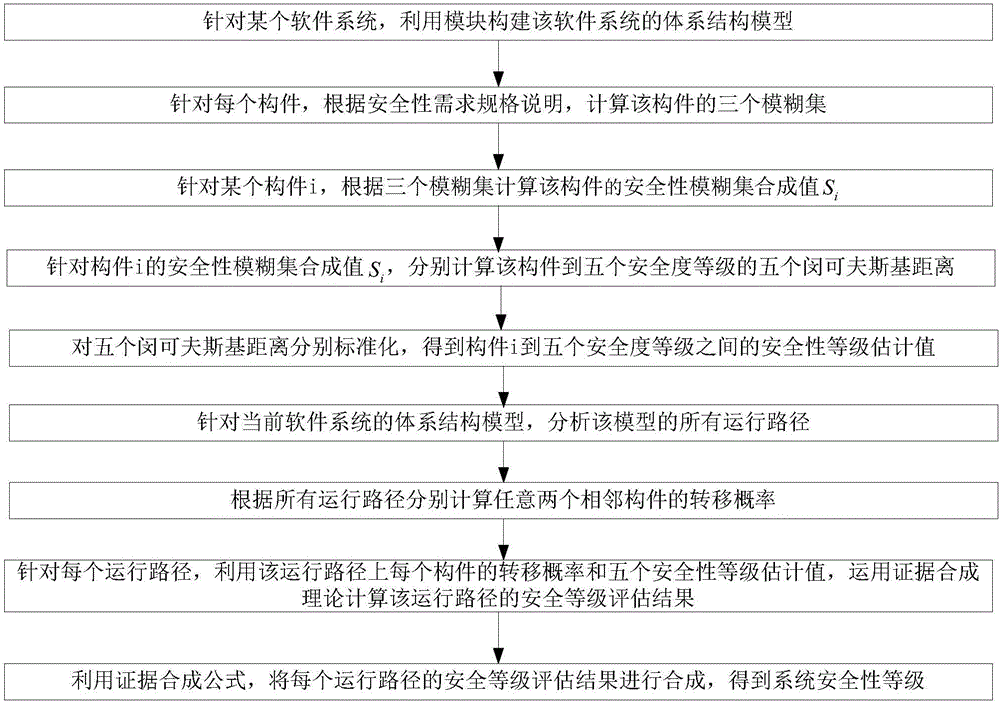
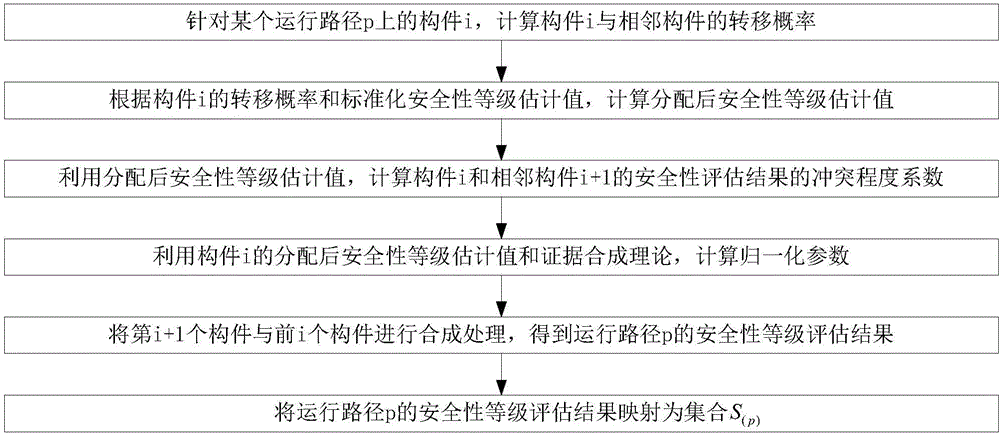
[0179] Step 1. For a certain software system, use modules to construct the architecture model of the software system;
[0180] In the present invention, the above several modules are regarded as the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com