File security protection method and apparatus
A security protection and file technology, applied in the protection of internal/peripheral computer components, digital data protection, etc., can solve the problems of high programming language requirements, inconvenience, and inability to effectively protect files, and achieve the effect of flexible and simple debugging
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0046] see figure 1 , the first embodiment of the present invention provides a file security protection method, the method comprising:
[0047] Step S101, initialize the kernel controller in the Linux kernel, load the first virtual operating system and the second virtual operating system;
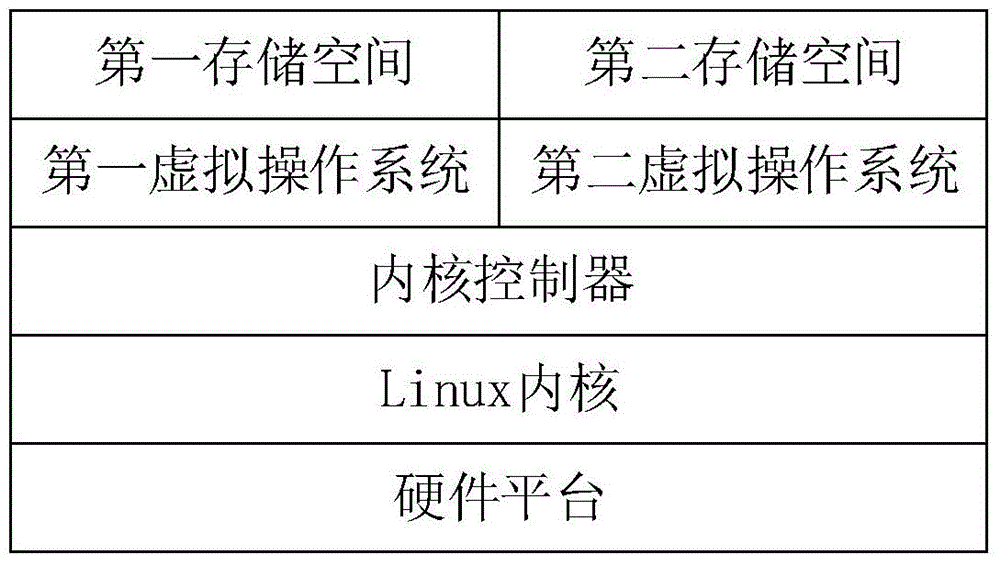
[0048] After the mobile terminal starts, first load the Linux kernel (Kernel), then initialize the kernel controller (namespace monitor) in the Linux kernel, then load the first virtual operating system and the second virtual operating system one by one on the Linux kernel, and make the first virtual operating system A virtual operating system is in an active state, and a second virtual operating system is in a suspended state. The above-mentioned first virtual operating system and the second virtual operating system are installed in independent storages, such as the internal memory of the mobile terminal. In addition, the first virtual operating system and the second virtual operating sy...
no. 2 example
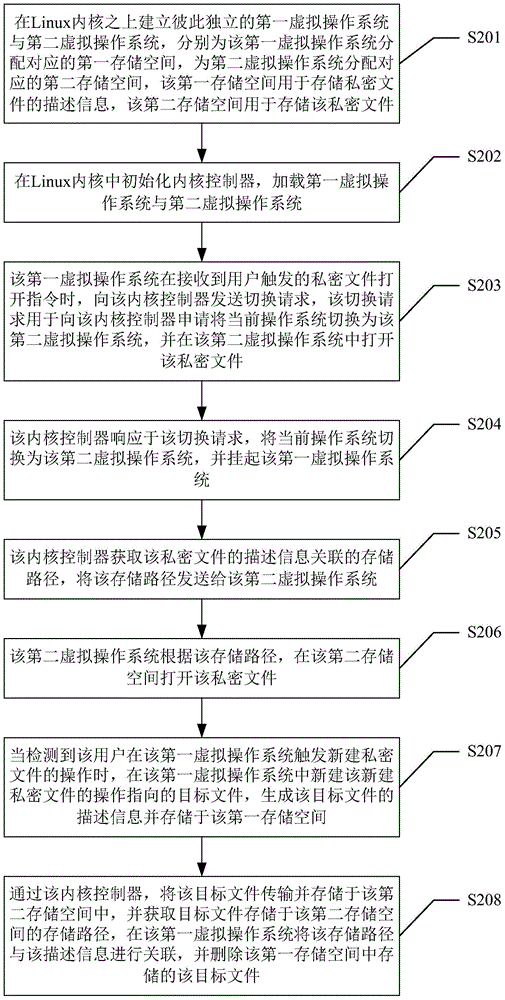
[0062] see image 3 , the second embodiment of the present invention provides a file security protection method, the method comprising:
[0063] Step S201, establish a first virtual operating system and a second virtual operating system independent of each other on the Linux kernel, allocate corresponding first storage space for the first virtual operating system, and allocate corresponding storage space for the second virtual operating system. a second storage space, the first storage space is used to store the description information of the private file, and the second storage space is used to store the private file;
[0064] Based on the Namespace (namespace) technology of the Linux kernel, two virtual operating systems with different namespaces independent of each other are established on the Linux kernel. The first virtual operating system and the second virtual operating system are installed in independent memories, such as mobile in the terminal's memory. The above tw...
no. 3 example
[0089] see Figure 4 , the third embodiment of the present invention provides a file security protection device, which can be applied to a mobile terminal. As the execution subject of the file security protection method provided in the above embodiment, it may be a mobile terminal or a module in the mobile terminal. Such as Figure 4 As shown, the device mainly includes: an initialization module 301, a system switching module 302 and an opening module 303, and the functions realized by each module are as follows:
[0090] The initialization module 301 is used to initialize the kernel controller in the Linux kernel, and load the first virtual operating system and the second virtual operating system one by one;
[0091] The system switching module 302 is configured to switch the current operating system to the second virtual operating system through the kernel controller and suspend the first virtual operating system when the first virtual operating system receives an instructi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com