Efficient SYN Flood attack identification and disposal method
A technology of attack identification and disposal method, applied in the field of efficient SYNFlood attack identification and disposal, which can solve the problems of exhaustion of server-side resources, failure to receive client ACK packets for SYN+ACK packets, and inability to respond to requests, etc. Achieving the effect of low attack impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
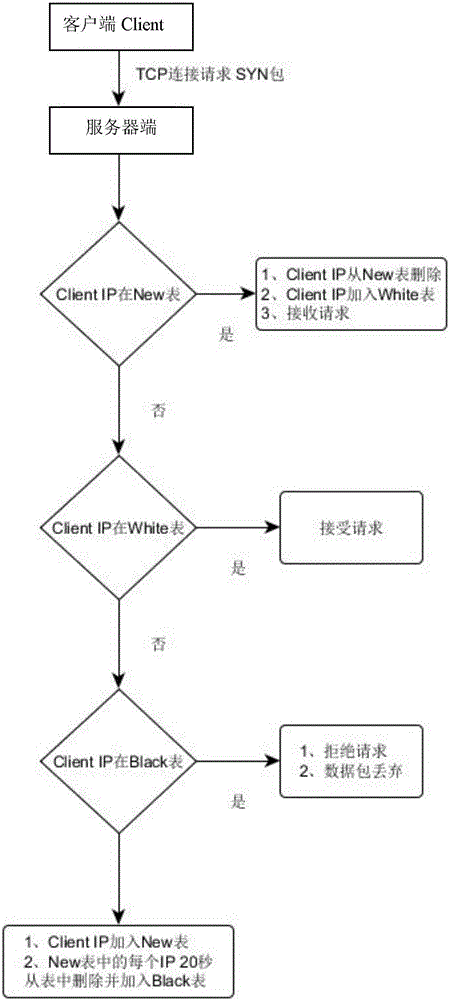
[0033] 1. The client initiates a TCP connection establishment request to the server.
[0034] 2. The server discards the first SYN packet of the connection request and records the client IP in the SYN packet to the New table.
[0035] 3. After the timeout retransmission time is reached, the client does not receive a response from the server, and will send the connection request again.
[0036] 4. The server finds that the client IP of the connection request is in the New table, the request is passed, and at the same time, the client IP is moved from the New table to the White table.
Embodiment 2
[0038] 1. The malicious client initiates a TCP connection establishment request to the server through a forged random source IP.
[0039] 2. The server discards the first SYN packet of the connection request and records the client IP of the SYN packet into the New table.
[0040] 3. After 20 seconds, if the server finds that there is no reconnection request with the same IP, the server will move the fake source IP from the New list to the Black list.
[0041] 4. If a malicious client forges a random source IP and repeats it after a timeout of 20 seconds, the request will be directly discarded by the server.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com