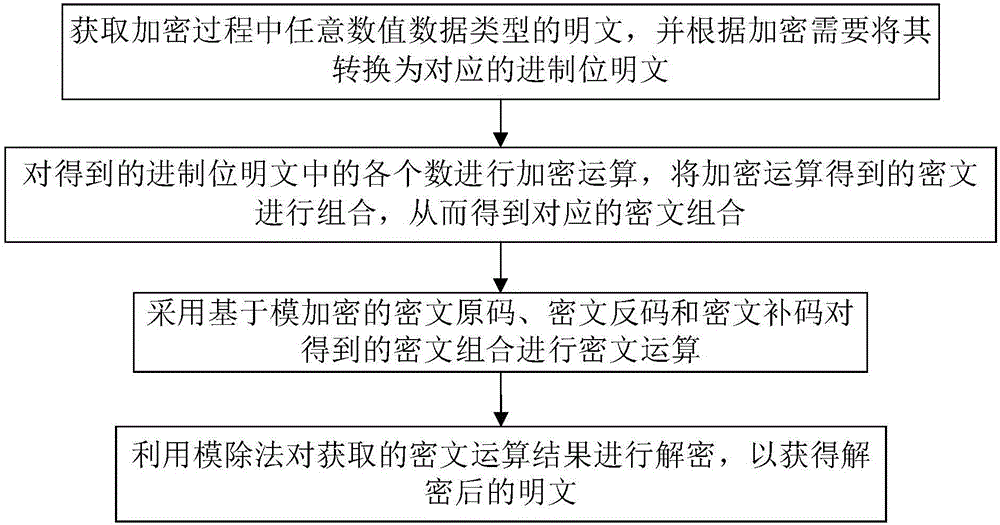
A Fully Homomorphic Encryption Processing Method Based on Modular Operation
A technology of fully homomorphic encryption and processing method, applied in the field of information security, can solve the problems that the encryption result cannot be decrypted correctly, and the noise of ciphertext multiplication is difficult to control, so as to improve data security, solve noise problems, and expand application scenarios. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0113] Example 1: c 1 +c 2 =(114,113,114)+(113,114,114);
example 2
[0114] Example 2: c 1 +c 2 =(114,114,114)+(113,114,114);
example 3
[0115] Example 3: c 1 +c 2 =(114,114,114)+(113,114,113);
[0116] In the ciphertext addition operation, it is first necessary to obtain the corresponding plaintext for each bit of the ciphertext according to the decryption formula (ciphertext mod p) mod s, and sum the obtained plaintext bit by bit, and then determine the Whether the value obtained after summing the ones is equal to the base system, if it is equal, it means that a carry has occurred, and the carry value (ie 1) is returned at this time, and the result of the sum of the ciphertext bits is returned (that is, the result of the ciphertext summation is realized Refresh), and add 1 during the summation of the last bit of the ciphertext bit; if not equal, it means that there is no carry, and return the carry value (ie 0) and the result of the summation of the ciphertext bit at this time, and Add 0 during the summation process of the upper bit of the ciphertext bit.
[0117] In the following ciphertext subtraction, m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com