Low voltage network electricity theft detection method based on AMI data
A technology of a low-voltage distribution network and a detection method, which is applied in the field of electricity stealing detection, can solve the problem that an electronic electric energy meter cannot effectively solve the problem of bypassing electricity stealing of a low-voltage distribution network and the like.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
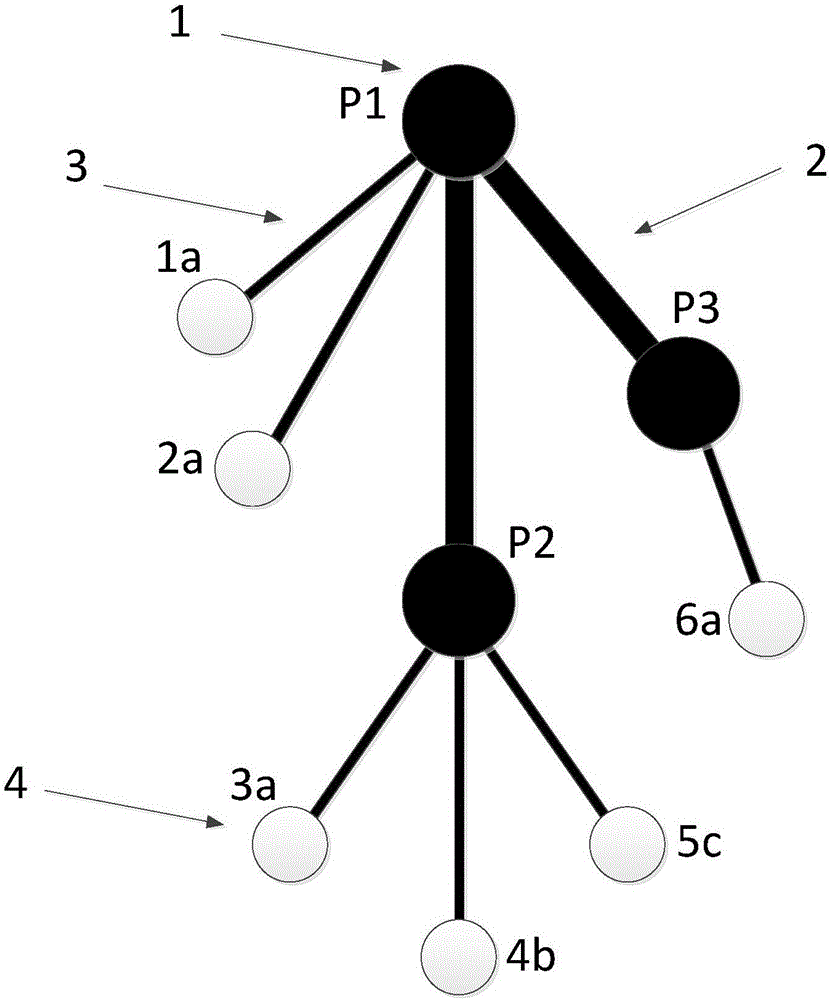
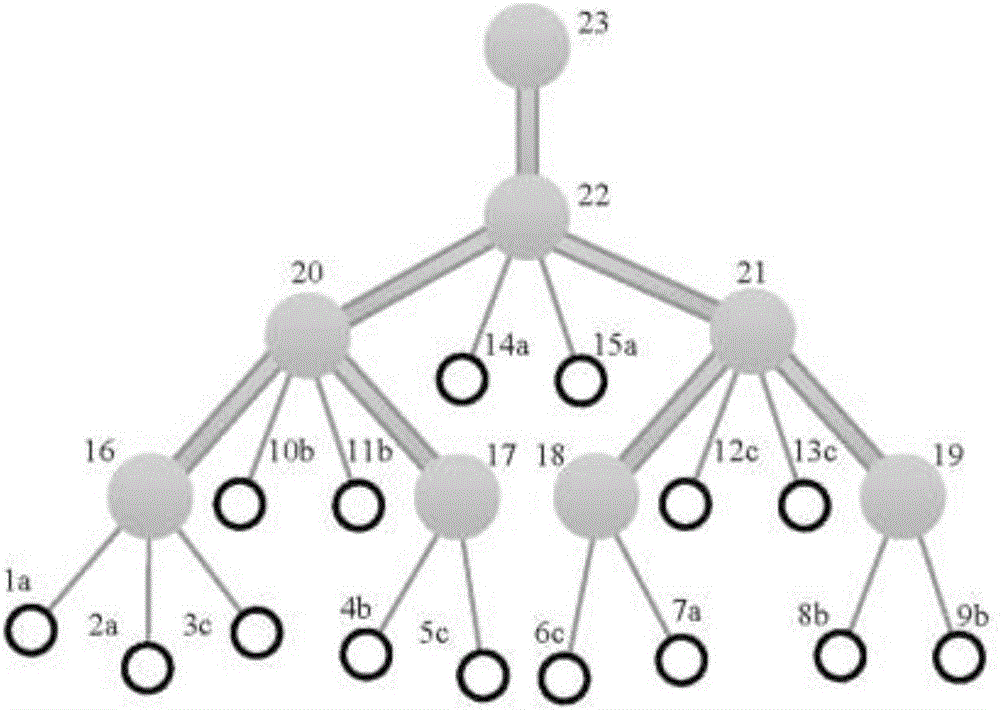
[0048] Let N be the number of nodes in the low-voltage distribution network under study. arr is an array of node numbers sorted by network topology from bottom to top, user nodes first and then non-user nodes. up is an array of upper-level node numbers. The basic process of using the voltage difference method to detect power theft in low-voltage distribution networks is as follows:
[0049] (1) Processing of user nodes;
[0050] 1) Each time a user node is selected in order from the arr array, and its number is set to k; the upper node number m of node k is obtained through the up array.
[0051] 2) Obtain the phase W (W ∈ {A, B, C}) of user node k.
[0052] 3) Calculate the W-phase voltage U of node m through node k pc .
[0053] 4) Put U PC Stored in the W-phase voltage storage matrix of node m.
[0054] 5) Add the current at node k to the W-phase current at node m.
[0055] attached figure 1It is a local topological diagram of a typical low-voltage distribution net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com