Identity verification method and device
An identity verification method and identity verification technology, applied in the field of identity verification methods and devices, capable of solving problems such as large security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
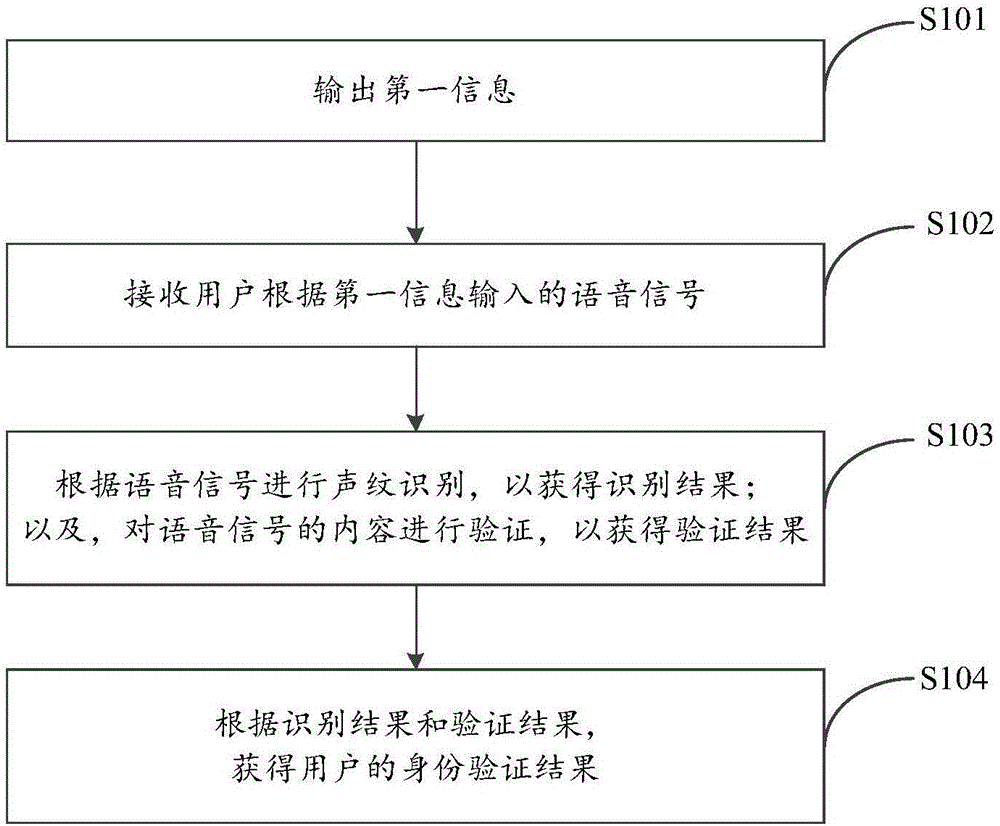
[0057] In order to solve the above-mentioned problems existing in the prior art, the embodiment of the present invention provides an identity verification method, please refer to figure 1 , which is a schematic flow chart of the first identity verification method provided by the embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
[0058] S101. Output first information.
[0059] It should be noted that, in the embodiment of the present invention, the first information may include several characters, may be only numbers, or may only be text, or may also include data and text.
[0060] In an optional implementation process, before outputting the first information, the method may further include: dynamically generating the first information.
[0061] In the embodiment of the present invention, there are many specific ways to realize the dynamic generation of the first information. For example, a piece of text can be randomly ...
Embodiment 2
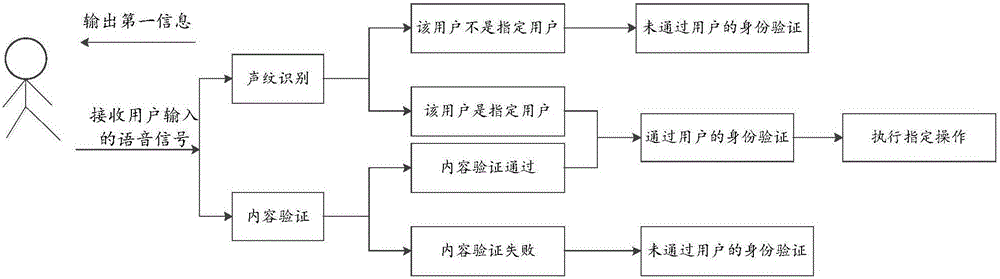
[0093] The following is an example of the identity verification method provided by the embodiment of the present invention in a specific implementation manner. This example is not intended to limit the application scenarios of the identity verification method provided by the embodiment of the present invention. In the authentication scenario, the method of this solution can be used to authenticate the user.
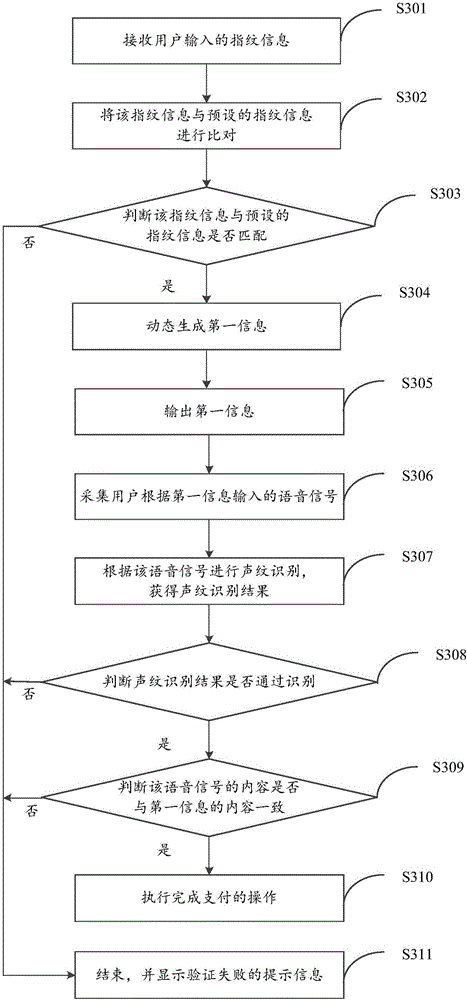
[0094] This embodiment provides an identity verification method applied in a payment scenario. Please refer to image 3 , which is a schematic flow chart when the identity verification method provided by the embodiment of the present invention is applied to a payment scenario, as shown in image 3 As shown, the method may specifically include:
[0095] S301. Receive fingerprint information input by a user.
[0096] S302. Compare the fingerprint information with preset fingerprint information.
[0097] S303, judging whether the fingerprint information matches the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com