Method and device for detecting errors in speech encryption
A detection method and detection device technology, applied in speech analysis, wireless communication, instruments, etc., can solve problems such as loss of function, and achieve the effect of improving the method system and expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
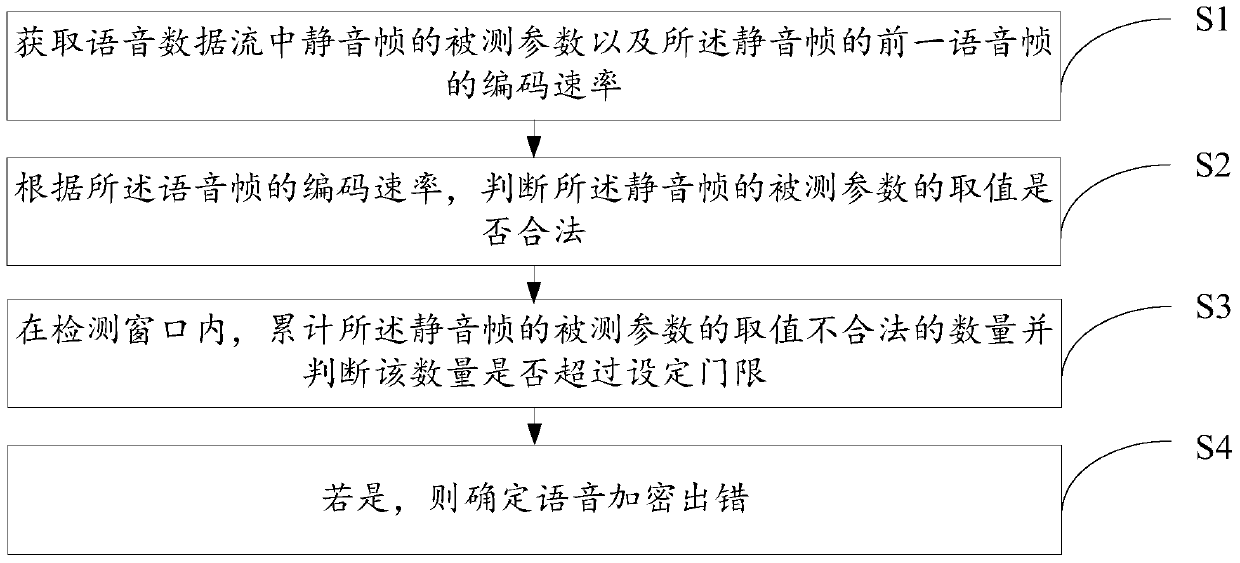
[0050] For the specific implementation of step S1:
[0051] The voice frame data received by the radio network controller RNC can judge the coding rate of the voice frame through its corresponding TFCI (Transport Format Combination Indicator) and the initial parameters of the voice service establishment, and then can determine the voice frame correspondingly. Encoding rate number.
[0052] The value of the measured parameter of the silent frame can be obtained by obtaining the coded data of the silent frame from the voice data stream. The coded data of the mute frame includes multiple fields, such as MI (Mode Indication) field, MR (Mode Request) field, FT (Frame Type) field and so on. Each field corresponds to a 3-bit or 4-bit bitcode, and different bitcodes correspond to different field values. Therefore, the above field can be used as the measured parameter of the silence frame, and the MI field is specifically used as the measured parameter of the silence frame below.
...
Embodiment 2
[0067] For the specific implementation of step S1:
[0068] The voice frame data received by the radio network controller RNC can judge the coding rate of the voice frame through its corresponding TFCI (Transport Format Combination Indicator) and the initial parameters of the voice service establishment, and then can determine the voice frame correspondingly. Encoding rate number.
[0069] The value of the measured parameter of the silent frame can be obtained by obtaining the coded data of the silent frame from the voice data stream. The coded data of the mute frame includes multiple fields, such as MI (Mode Indication) field, MR (Mode Request) field, FT (Frame Type) field and so on. Each field corresponds to a 3-bit or 4-bit bitcode, and different bitcodes correspond to different field values. Therefore, the above field can be used as the measured parameter of the silence frame, and the MI field is specifically used as the measured parameter of the silence frame below.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com