Operation method and system for ciphertext numbers
An operation method and encryption algorithm technology, which is applied in the field of information security, can solve the problems of limited and complex homomorphic encryption operations, and achieve the effect of low possibility of cooperative cheating and avoiding cooperative cheating
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0023] Example 1: Multiplying a ciphertext number by a plaintext number
[0024] The specific implementation is as follows:
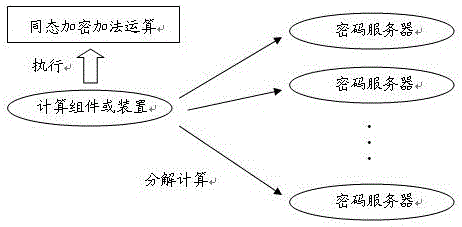
[0025] When a calculation component or device multiplies a ciphertext number and a plaintext number, the calculation component or device first decomposes the ciphertext number into the homomorphic encryption addition sum of n ciphertext numbers, and then uses the decomposed n Each ciphertext number in the ciphertext number and the plaintext number to be multiplied form a group to form n groups of numbers, and then submit the n groups of numbers to n cryptographic servers to request multiplication operations;
[0026] After n cryptographic servers receive each set of numbers, they decrypt the ciphertext numbers respectively, and then multiply the plaintext numbers obtained after decrypting the ciphertext numbers with the received plaintext numbers, and use additive homomorphic encryption for the calculation results The algorithm is encrypted and returne...
Embodiment 2
[0028] Example 2: Divide a ciphertext number by a plaintext number
[0029] The specific implementation is as follows:
[0030] When a calculation component or device divides a ciphertext number by a plaintext number, the calculation component or device first decomposes the ciphertext number into the homomorphic encryption addition sum of n ciphertext numbers, and then uses the decomposed n Each ciphertext number in the ciphertext numbers and the plaintext number as the divisor form n groups of numbers, and then submit the n groups of numbers to n password servers to request division operations;
[0031] After receiving each group of numbers, n cryptographic servers decrypt the ciphertext numbers respectively, divide the plaintext numbers obtained after decrypting the ciphertext numbers by the plaintext numbers as the divisor, and encrypt the calculation results with the additive homomorphic encryption algorithm and then returned to the computing component or device;
[0032...
Embodiment 3
[0033] Embodiment 3: Divide a plaintext number by a ciphertext number
[0034] The specific implementation is as follows:
[0035] When a computing component or device divides a plaintext number by a ciphertext number, the computing component or device first multiplies a random plaintext number by the dividend plaintext number (as the dividend plaintext number) to form a new dividend plaintext number, Calculate the divisor ciphertext number (as the ciphertext number of the divisor) by the same random plaintext number with the calculation method for the ciphertext number, as in Example 1, form a new divisor ciphertext number, and then divide the new dividend The plaintext number is decomposed into the sum of n plaintext numbers, and the decomposed n plaintext numbers are called the components of the new dividend plaintext number, and then each component of the decomposed n new dividend plaintext number components is combined with the new The divisor ciphertext number is a grou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com