User identifier recognition method and apparatus
A technology of user identification and identification method, which is applied in the field of user identification identification method and a user identification device, and can solve the problems of high time cost of manual labeling, difficulty in obtaining training data, and low applicability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
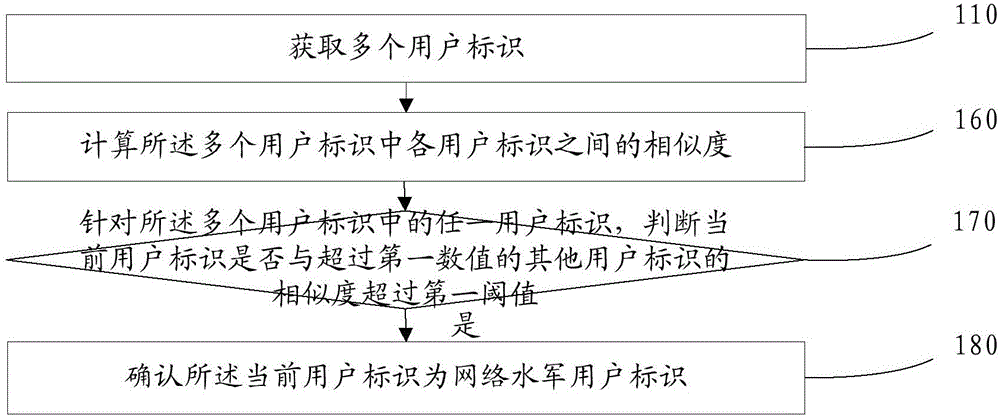
[0114] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a method for identifying a user ID according to an embodiment of the present invention, which may specifically include the following steps:
[0115] Step 110, acquiring multiple user IDs.
[0116] In this embodiment of the present invention, the user ID may refer to a name that identifies the user identity in the IIP, for example, user nickname, user name, user account, etc. all belong to the user ID. In practical applications, the user ID is composed of a series of characters recognizable by the IIP system, such as letters, Chinese characters, Arabic numerals, special symbols, and so on. Such as Figure 1A Examples for some user IDs. It can be seen that the 1st to 4th user IDs are composed of Chinese characters, underscores and letters, while the subsequent 5th to 8th and 12th to 16th are composed of Chinese characters and letters, and the other 9th to 11th are completely composed of Chine...
Embodiment 2
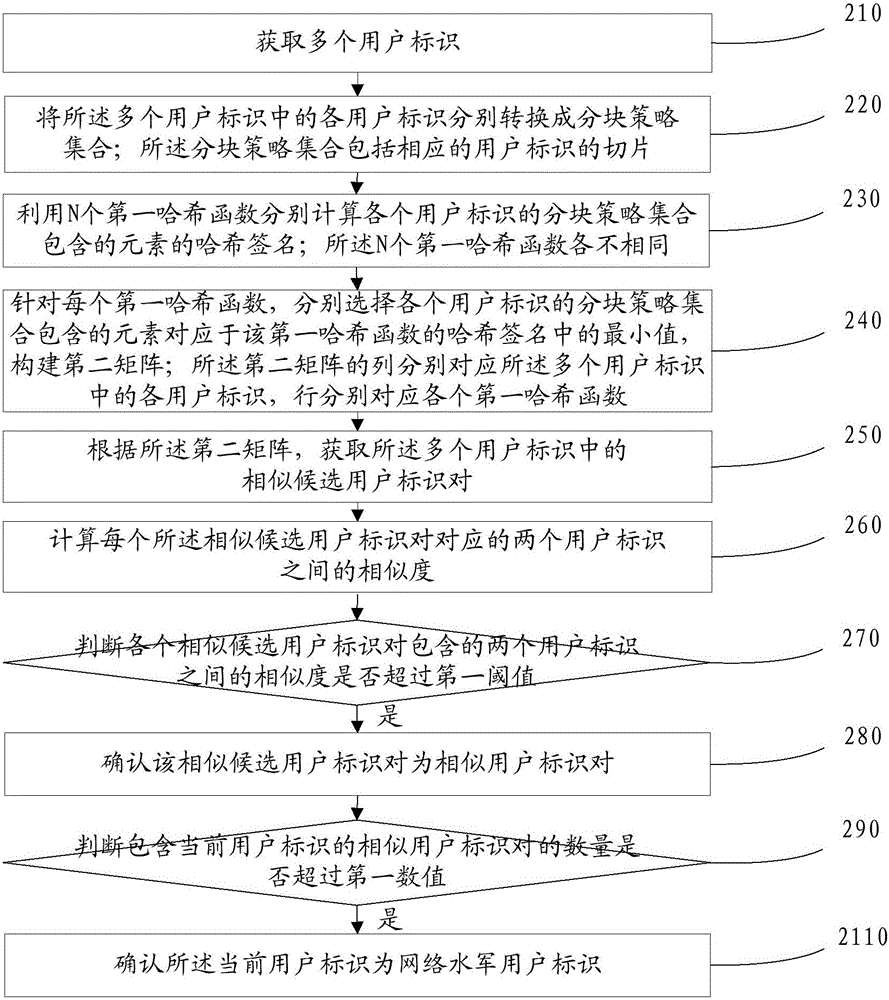
[0193] refer to figure 2 , which shows a flow chart of the steps of an embodiment of a method for identifying a user ID according to an embodiment of the present invention, which may specifically include the following steps:
[0194] Step 210, acquiring multiple user IDs.
[0195] Step 220, converting each user ID among the plurality of user IDs into a block policy set; the block policy set includes slices of corresponding user IDs.
[0196] Step 230, using N first hash functions to calculate the hash signatures of the elements included in the block policy set of each user ID; the N first hash functions are different.
[0197] In practical applications, if according to the method of Embodiment 1, the similarity between each user's nickname is directly compared in turn, the time complexity is O(n 2 ), where O(f(n)) is a time complexity function, which can quantitatively describe the running time of the algorithm f(n), n is the number of user IDs that need to be identified, u...
Embodiment 3
[0279] refer to image 3 , which shows a flow chart of the steps of an embodiment of a method for identifying a user ID according to an embodiment of the present invention, which may specifically include the following steps:
[0280] Step 310, acquiring multiple user identifiers.
[0281] Step 320: Transform each user ID among the plurality of user IDs into a block policy set; the block policy set includes slices of corresponding user IDs.
[0282] Step 330: Construct a first matrix according to the relationship between each user ID among the plurality of user IDs and each element in the block strategy set of each user ID; wherein, the columns of the first matrix correspond to each user ID ID; the row of the first matrix corresponds to each element in the block policy set of each user ID; if the user ID contains any element in the element, then the corresponding value in the first matrix is The second value; if the element is not included in the user identifier, then the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com