Botnet attribute identification method, defense method and device
A botnet and attribute identification technology, which is applied in the field of botnet attribute identification methods, defense methods and devices, can solve problems such as network paralysis, personal and national security hazards, resource abuse, etc., and achieve the effect of rapid removal and improved defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
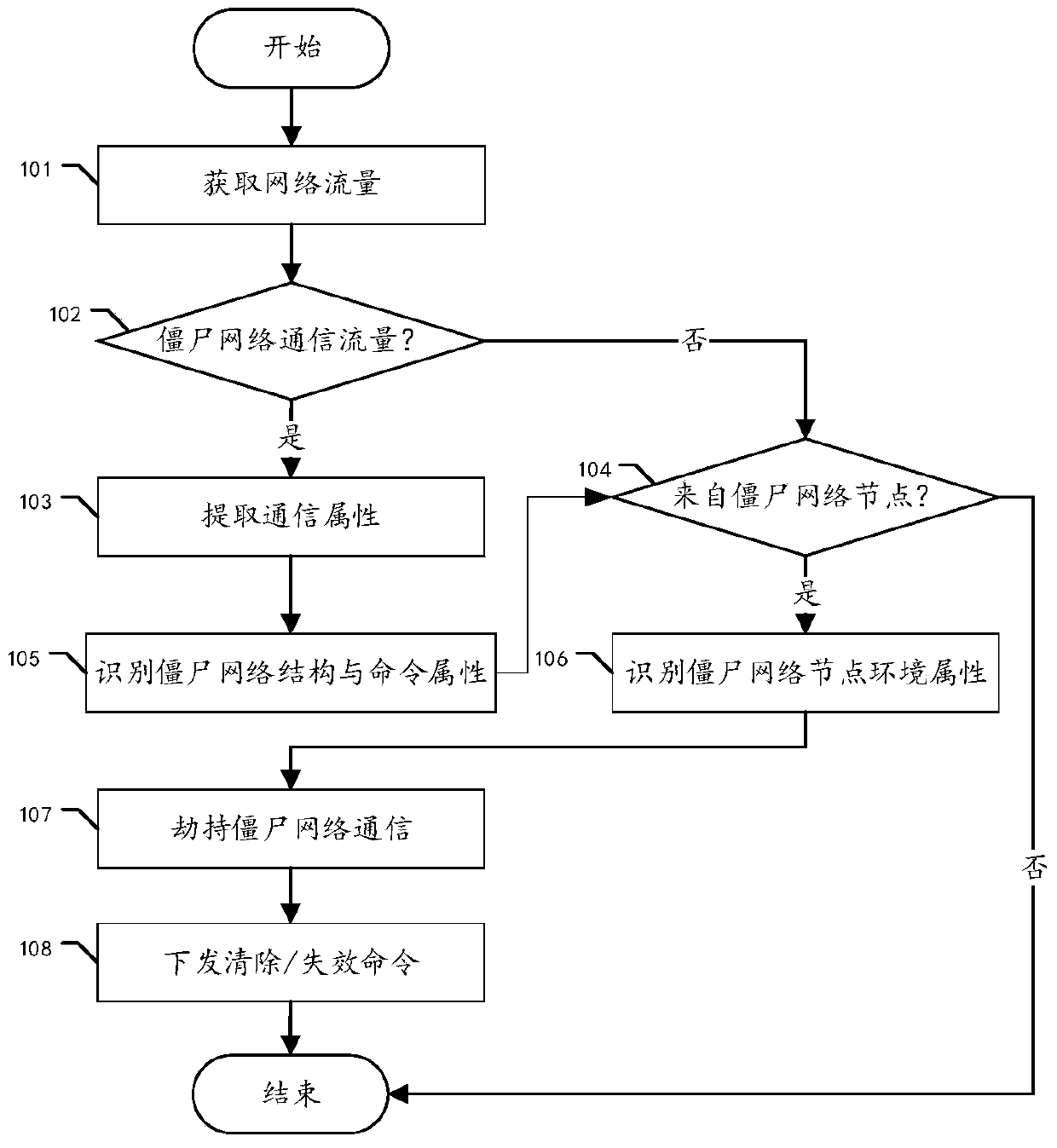
[0043] An embodiment of the present invention provides a method for identifying attributes of a botnet, including:
[0044] Identify botnet communication data traffic and normal network communication data traffic in network traffic;
[0045] Extracting basic communication attributes from the identified botnet communication data flow, identifying a botnet structure and a botnet command attribute from the extracted basic communication attributes; the botnet structure includes a master control terminal and a number of controlled terminals;
[0046] The environmental attributes of each node in the botnet structure are identified from normal network traffic.
[0047] The embodiment of the present invention can effectively identify the attributes of the botnet, and the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0048] like figure 1 As shown, the embodiment method of the present invention includes:
[004...
Embodiment 2
[0064] An embodiment of the present invention provides a botnet defense method, including:
[0065] Identification step: using the identification method described in Embodiment 1 botnet structure, botnet command attribute and each node environment attribute;
[0066] Defense step: Hijack the communication session in the botnet structure by man-in-the-middle, and clear the botnet program in the botnet structure based on the attributes of the botnet command.
[0067] The embodiment of the present invention obtains more comprehensive botnet attributes from the communication attributes and all network traffic, and realizes the remote and large-scale rapid removal of botnets through the botnet's own functions and the middleman method, and solves the general network defense means In order to improve the defense effect of botnets, the zombie hosts are still harmed after changing the network environment.
[0068] Embodiments of the present invention will be described in detail below....
Embodiment 3
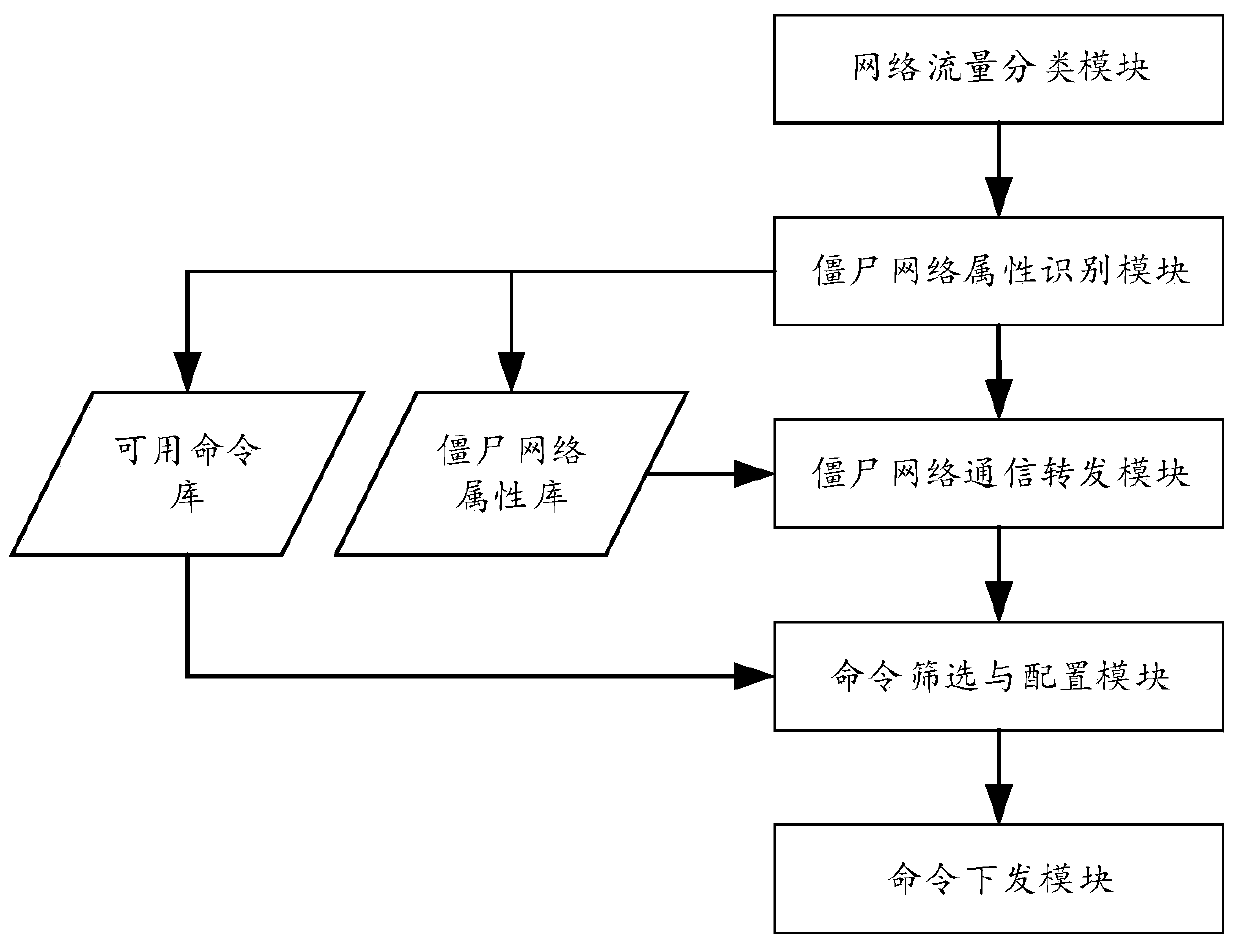
[0078] like figure 2 As shown, the embodiment of the present invention provides a botnet attribute identification device, which is a device embodiment corresponding to Embodiment 1, including:
[0079] A network traffic classification module, configured to obtain full network traffic, and identify botnet communication data traffic and normal network communication data traffic in the network traffic;
[0080] The botnet attribute identification module is used to identify the type, structure and command of the botnet according to the botnet traffic, and identify the node environment according to the normal network traffic;
[0081] Specifically, it is used to extract basic communication attributes from the identified botnet communication data flow, and identify the botnet structure and botnet command attributes from the extracted basic communication attributes; the botnet structure includes a master control terminal and several controlled end; and identify the environmental at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com