A privacy information protection method, mobile terminal and wearable device
A privacy information and mobile terminal technology, applied in transmission systems, electrical components, etc., can solve security threats and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
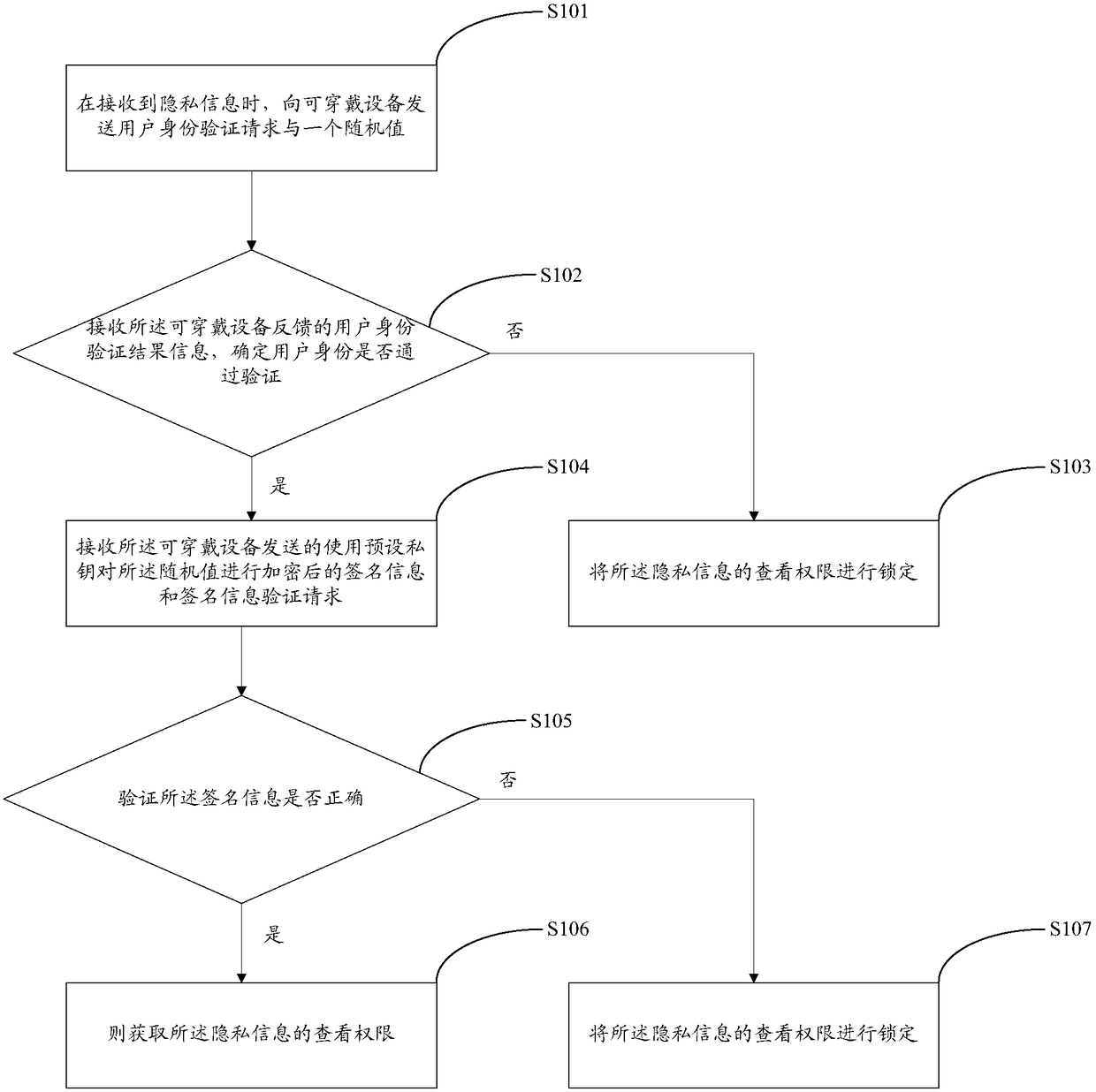
[0044] The invention provides a privacy information protection method, figure 1 It shows a flow chart of Embodiment 1 of the privacy information protection method of the present invention, including:
[0045] Step S101: When receiving the private information, send a user identity verification request and a random value to the wearable device;
[0046] When the mobile terminal receives the private information, it sends a user authentication request and a generated random value to the matching wearable device.
[0047] Step S102: Receive user identity verification result information fed back by the wearable device, determine whether the user identity has passed the verification, if yes, go to step S104, otherwise go to step S103;
[0048] Step S103: Lock the viewing authority of the private information;
[0049] When the user identity is not verified, the current user identity of the wearable device is not trusted, and the permission to view private information is locked to pr...
Embodiment 2
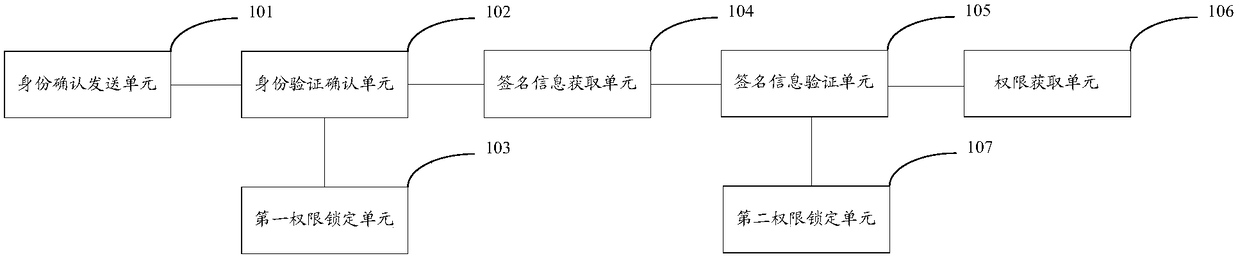
[0060] The present invention also provides a mobile terminal, figure 2 A schematic structural diagram of a mobile terminal according to Embodiment 2 of the present invention is shown, including:
[0061] An identity confirmation sending unit 101, configured to send a user identity verification request and a random value to the wearable device when receiving private information;
[0062] An identity verification confirmation unit 102, configured to receive user identity verification result information fed back by the wearable device, and determine whether the user identity has passed the verification;
[0063] The first authority locking unit 103 is configured to lock the viewing authority of the private information when it is determined that the user identity has not passed the verification;
[0064] The signature information acquisition unit 104 is configured to receive the signature information and the signature information verification request sent by the wearable device ...
Embodiment 3
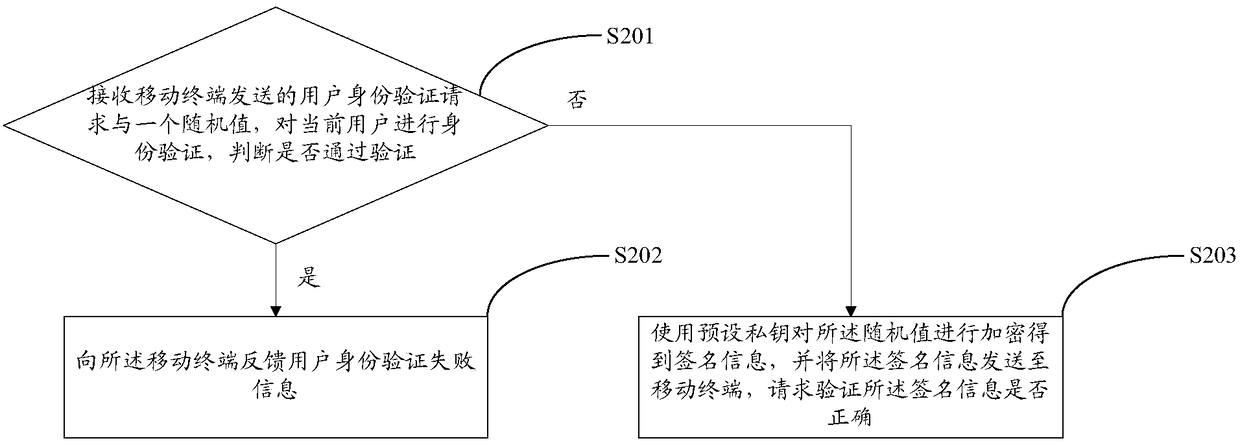
[0074] The invention also provides a privacy information protection method, image 3 It shows a flow chart of the privacy information protection method in Embodiment 3 of the present invention, including:
[0075] Step S201: Receive the user identity verification request and a random value sent by the mobile terminal, perform identity verification on the current user, and judge whether the verification is passed, if yes, go to step S203, otherwise go to step S202;
[0076] The wearable device receives the user identity verification request and random value of the mobile terminal, and the identity verification of the current user can be performed by obtaining the current user's biological information, such as fingerprints, etc., and judging whether the biological information matches the pre-stored biological information. , it is determined that the user identity has passed the authentication, otherwise it is determined that the user identity has not passed the authentication. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com