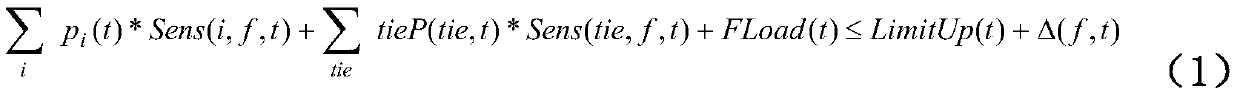A mid-to-long-term relaxed network security constraint modeling method based on the combination of near and far
A technology of network security and modeling method, which is applied in the field of medium and long-term relaxed network security constraint modeling, which can solve problems such as long solution time, failure to meet production needs, and long optimization cycle, so as to reduce the calculation dimension and shorten the optimization solution time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
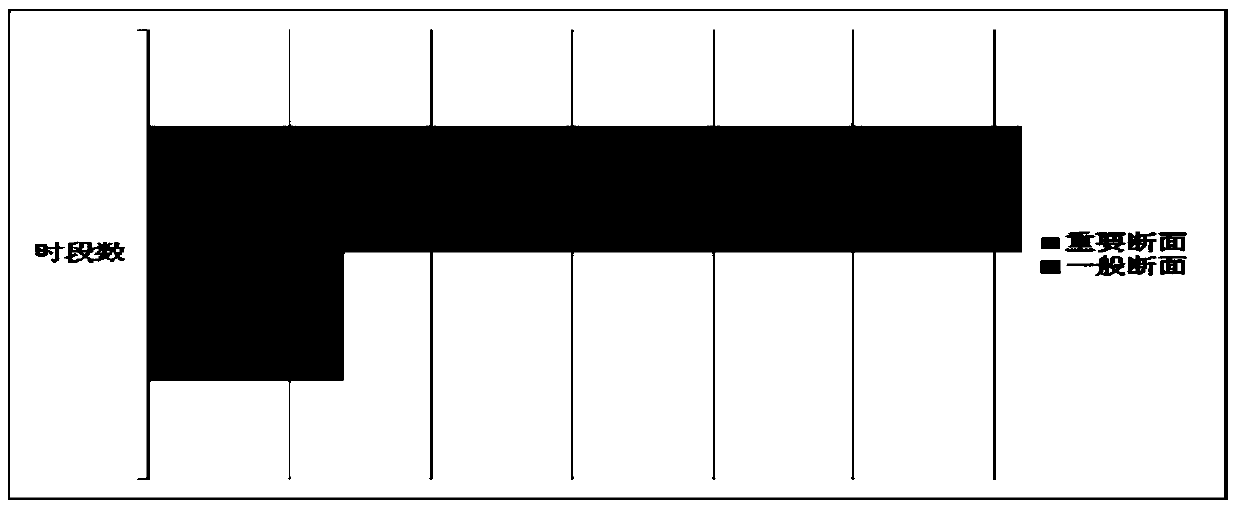
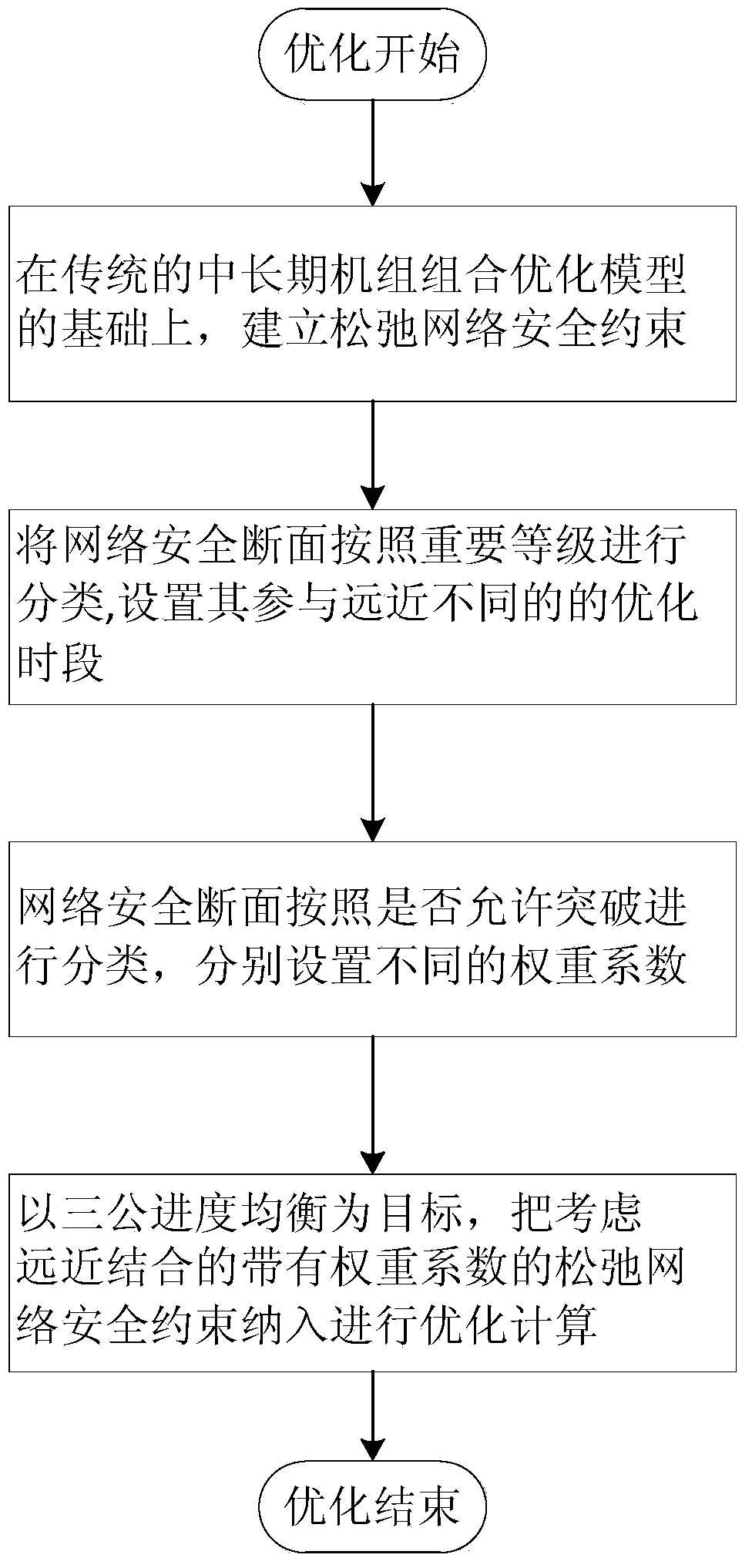
[0036] Such as Figure 1-2 As shown, the invention of this example provides an optimization modeling method combining far and near relaxed network security constraints. According to the importance level of the network security section participating in the optimization, different optimization time periods are set respectively, and different time intervals are set according to whether breakthroughs are allowed. The weight coefficient of , avoiding the situation that the optimization time is too long or the optimization has no solution. The method comprises the steps of:
[0037] 1. Establish loose network security constraints
[0038]
[0039]
[0040] where: p i (t) represents the physical output of unit i in time period t;
[0041] tieP(tie,t) represents the transmission power of the tie line tie in the time period t;
[0042] Sens(i,f,t) represents the correlation sensitivity coefficient between the physical output of unit i and the transmission flow of safety secti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com