Information delivery system
A technology for information release and information generation, which is applied in the field of information release methods and programs, and can solve problems such as being unable to see confidential data content
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0048] In Embodiment 1, an information distribution system 500 (information distribution method) will be described as the most secure method: In addition to the fact that the server cannot obtain the user's private key, the server cannot impersonate the PKG and forge the master public key at will. Key and user secret key are sent to the user.
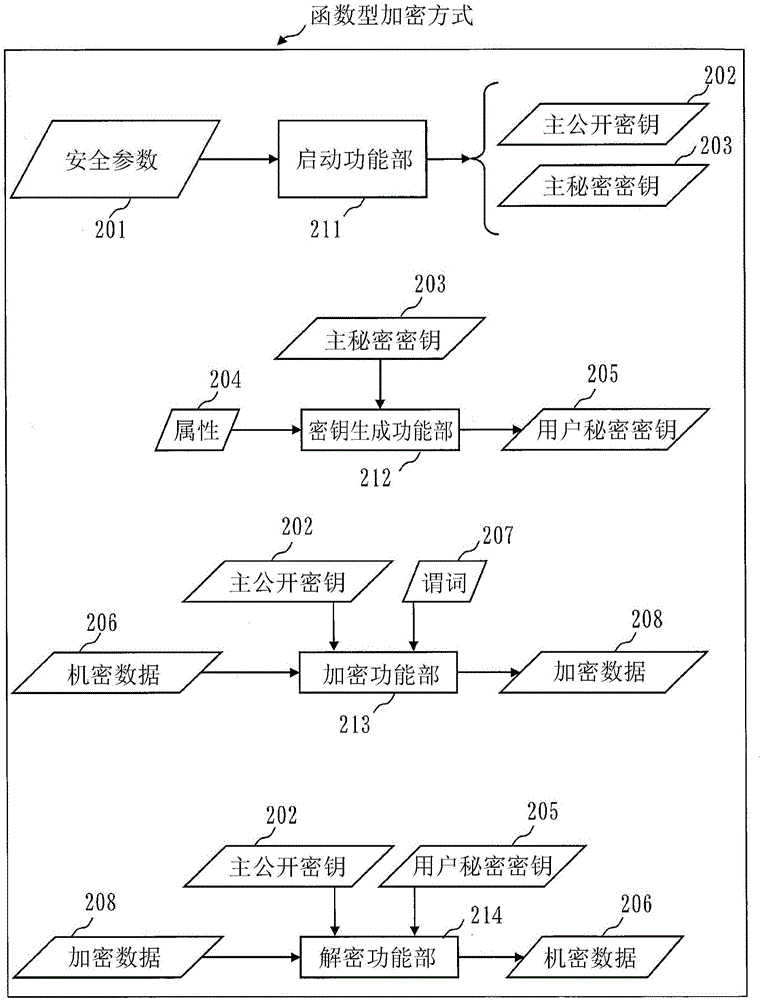
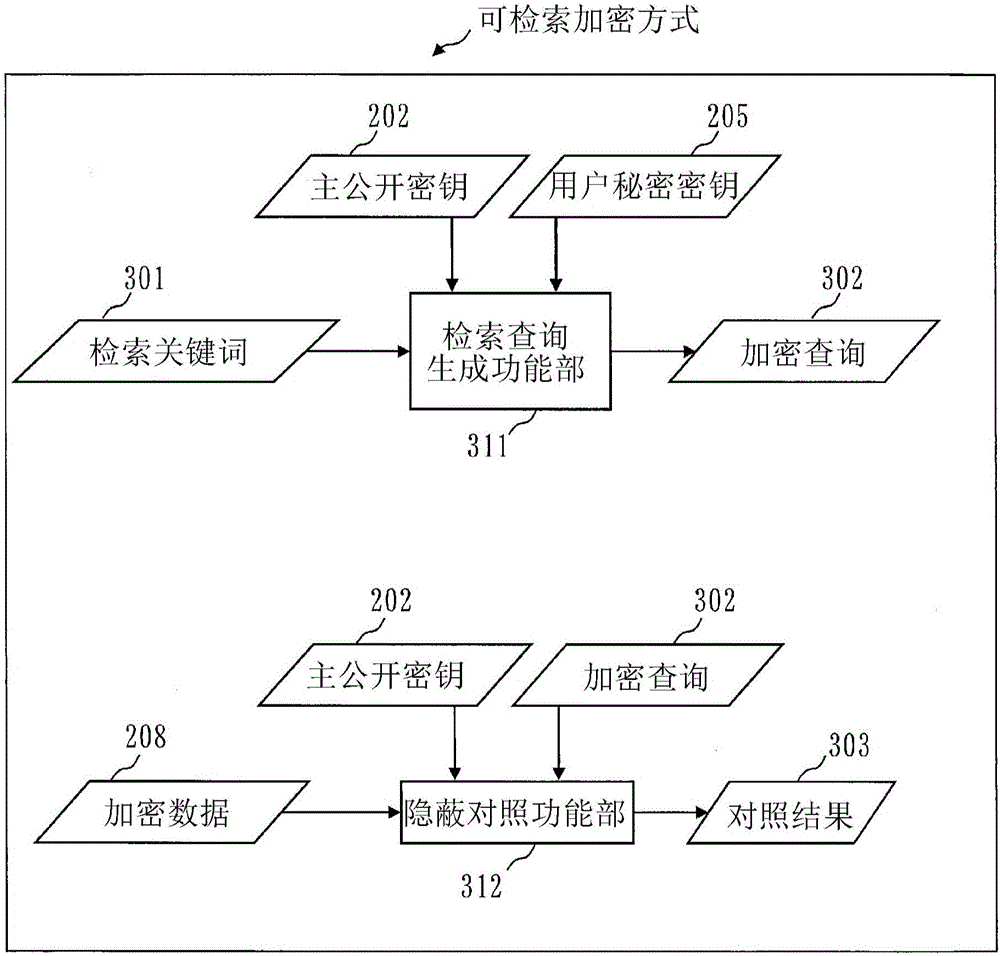
[0049] First, as a premise for describing the functional configuration of the information distribution system 500 of this embodiment, the configuration of the information distribution system 500, functional encryption, and searchable encryption will be described.
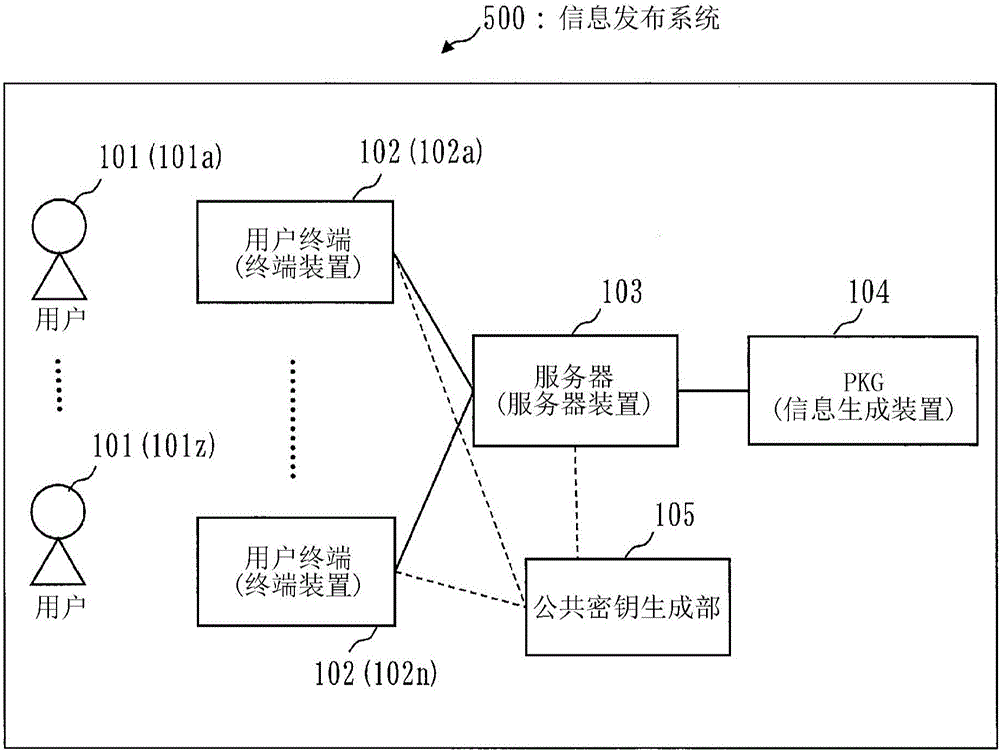
[0050] figure 1 It is a figure which shows an example of the structure of the information delivery system 500 of this Embodiment 1.
[0051] like figure 1 As shown, the information distribution system 500 has: a PKG104 (information generation device) that generates information such as a public key, a secret key, a master public key, a master secret key, and a user secret ke...
Embodiment approach 2
[0215] In this embodiment, differences from Embodiment 1 will be mainly described.
[0216]In this embodiment, an information distribution system 500a that is partially different from the information distribution system 500 described in Embodiment 1 will be described.
[0217] Portions having the same functions and operations as those described in Embodiment 1 may be denoted by the same reference numerals, and description thereof will be omitted.
[0218] In this embodiment, a method is disclosed in which the server 103 restricts illegal activities such as key forgery and storage data theft by the server administrator's agreement, capabilities, or intentions in some form. , compared with Embodiment 1, the server 103 is prevented from obtaining the user's private key more efficiently in terms of the number of steps or the number of data.
[0219] Figure 13 It is a flowchart showing the procedure of the system startup process in the information distribution system 500a of thi...
Embodiment approach 3
[0269] In this embodiment, differences from Embodiments 1 and 2 will be mainly described.
[0270] In this embodiment, an information distribution system 500b that is partially different from the information distribution systems 500 and 500a described in Embodiments 1 and 2 will be described.
[0271] Parts having the same functions and operations as those of the constituent parts described in Embodiments 1 and 2 are sometimes assigned the same reference numerals, and their descriptions are omitted.
[0272] In this embodiment, a method is disclosed in which the server 103 cannot obtain the user's private key more efficiently by using the user's password.
[0273] In addition, as a premise of this embodiment, in a general system, it is necessary to understand the fact that, when authentication of a password is performed, authentication is performed by comparing the hash value of the password, not the password itself. That is, the hash value of the password is stored on the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com