A software authentication method and related equipment and system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
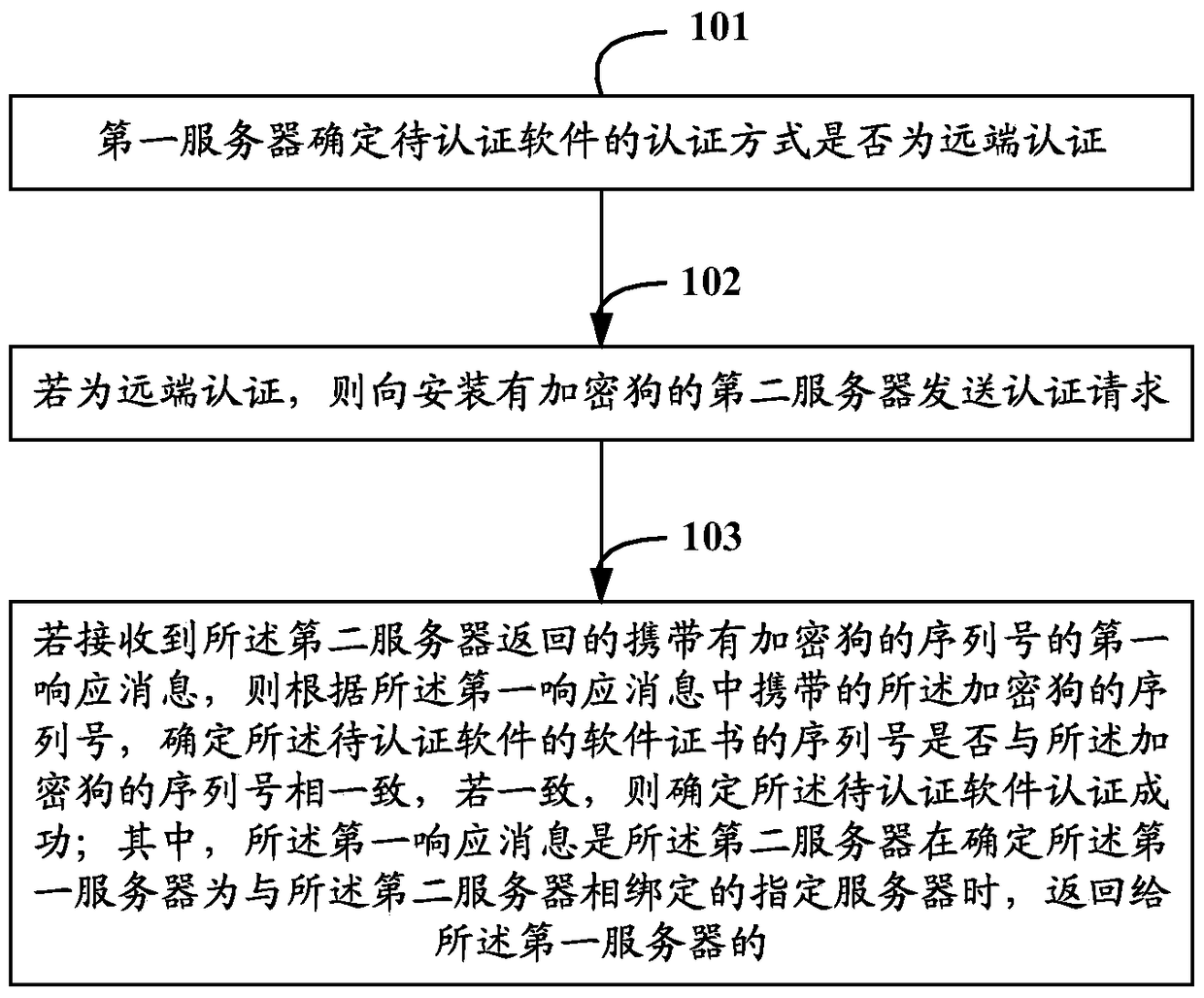
[0036] In order to solve the problems of low security and limited application scenarios in the existing software authentication methods, Embodiment 1 of the present invention provides a software authentication method, such as figure 1 As shown in , it is a schematic flow chart of the software authentication method described in Embodiment 1 of the present invention. figure 1 It can be seen that the software authentication method described in Embodiment 1 of the present invention may include the following steps:
[0037] Step 101: the first server determines whether the authentication mode of the software to be authenticated is remote authentication.
[0038] Wherein, the software to be authenticated may generally be software installed in the first server, such as installed BSA service software, etc., which will not be repeated here.
[0039] Optionally, before step 101 is performed, after the software is installed, remote authentication or local authentication can be selected ...
Embodiment 2
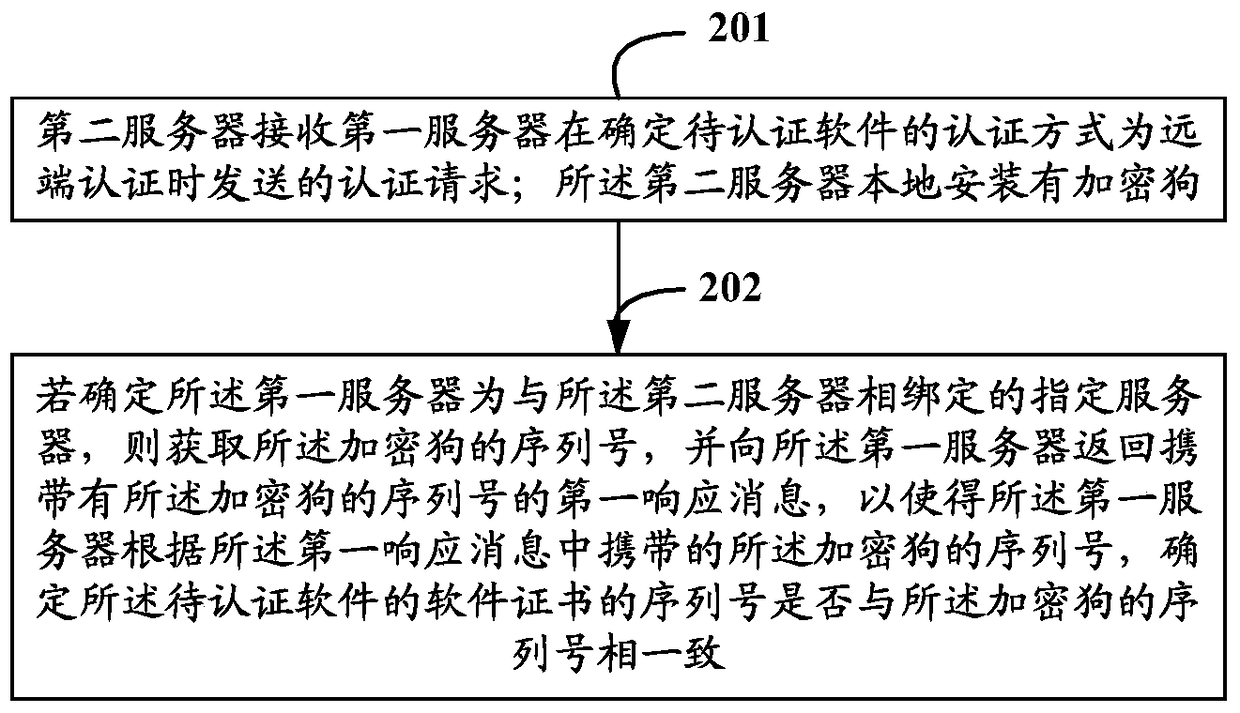
[0084] Based on the same inventive concept as that of Embodiment 1 of the present invention, Embodiment 2 of the present invention provides another software authentication method, such as figure 2 As shown in , it is a schematic flow chart of the software authentication method described in Embodiment 2 of the present invention. figure 2 It can be seen that the software authentication method described in Embodiment 2 of the present invention may include the following steps:
[0085] Step 201: the second server receives the authentication request sent by the first server when the authentication mode of the software to be authenticated is determined to be remote authentication; the second server is locally installed with a dongle;
[0086] Wherein, the software to be authenticated may generally be software installed in the first server, such as installed BSA service software, etc., which will not be repeated here.
[0087] It should be noted that the second server can be any d...
Embodiment 3
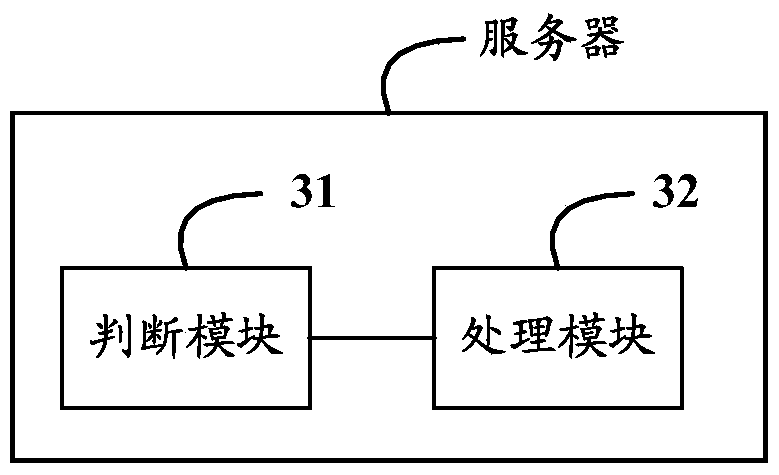
[0103] Based on the same inventive concept as that of Embodiment 1 of the present invention, Embodiment 3 of the present invention provides a server, such as image 3 As shown in , it is a schematic structural diagram of the server described in Embodiment 3 of the present invention, which is represented by image 3 It can be seen that the server described in Embodiment 3 of the present invention may include:
[0104] A judging module 31, configured to determine whether the authentication mode of the software to be authenticated in the server is remote authentication;
[0105] The processing module 32 is used to send an authentication request to a remote server equipped with a dongle if it is determined that the authentication method of the software to be authenticated is remote authentication according to the judgment result of the judgment module 31; The first response message carrying the serial number of the dongle returned by the remote server, then determine the serial n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com