HTTP protocol data leak prevention method and system based on deep content analysis
A HTTP protocol and data technology, applied in transmission systems, electrical components, etc., can solve problems such as difficult user configuration, opaque network, easy loss of network control, etc., to achieve good user experience and protect internal data of the enterprise
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described below are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
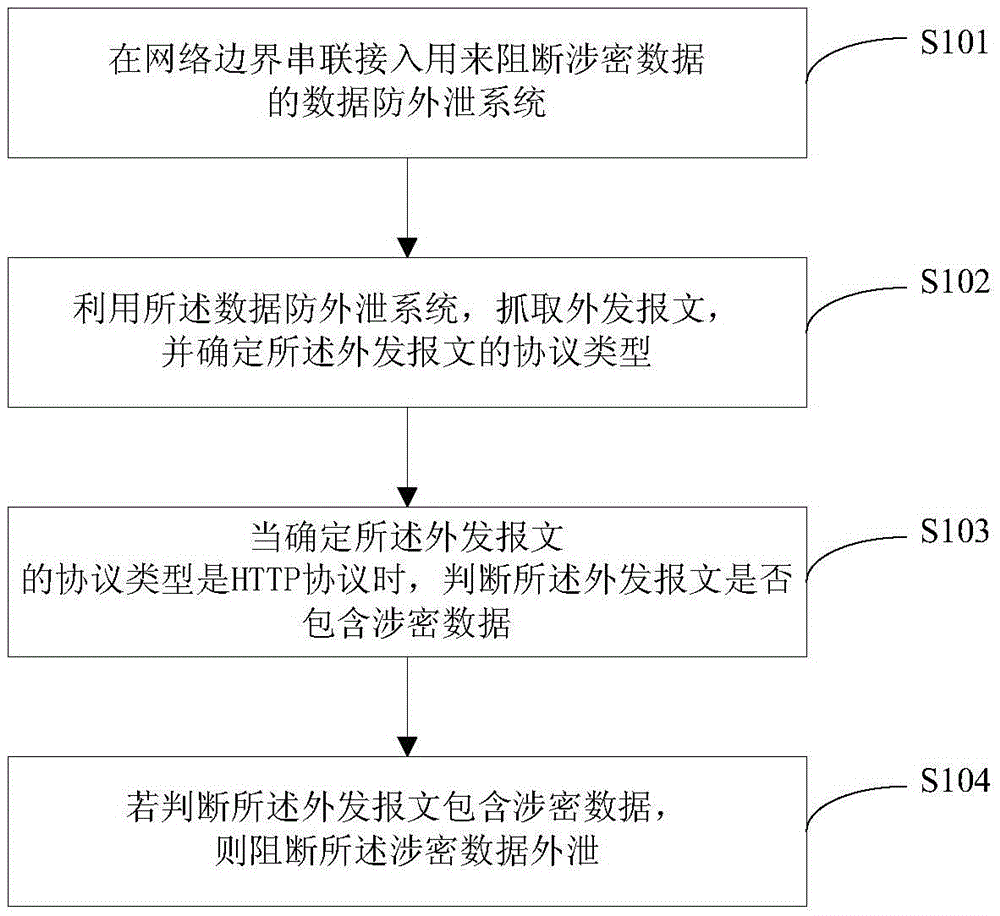
[0042] figure 1 It is a flow chart of the HTTP protocol data leakage prevention method based on deep content analysis provided by the present invention, such as figure 1 As shown, the steps include:
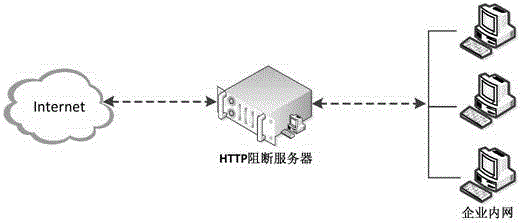
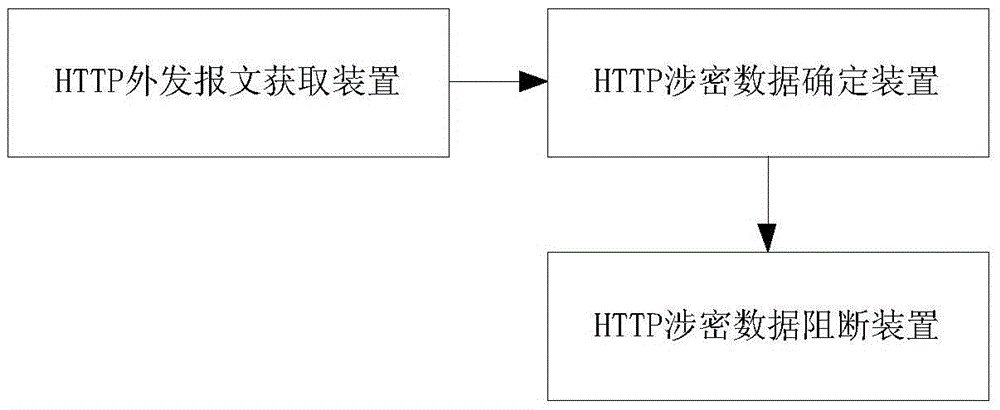
[0043] Step S101: A data leakage prevention system for blocking confidential data is connected in series at the network border.
[0044] Step S102: Use the data leakage prevention system to capture the outgoing message and determine the protocol type of the outgoing message.
[0045] Specifically, use the data leakage prevention system to obtain the port characteristics (such as the port number) of the outgoing message, and determine whether the protocol t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com