Access control monitoring method and system thereof
An access control and user technology, applied to instruments, single input/output registers, time registers, etc., can solve problems such as easy loss of card devices, potential safety hazards, and limited face recognition technology, and achieve The authentication method is convenient and the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
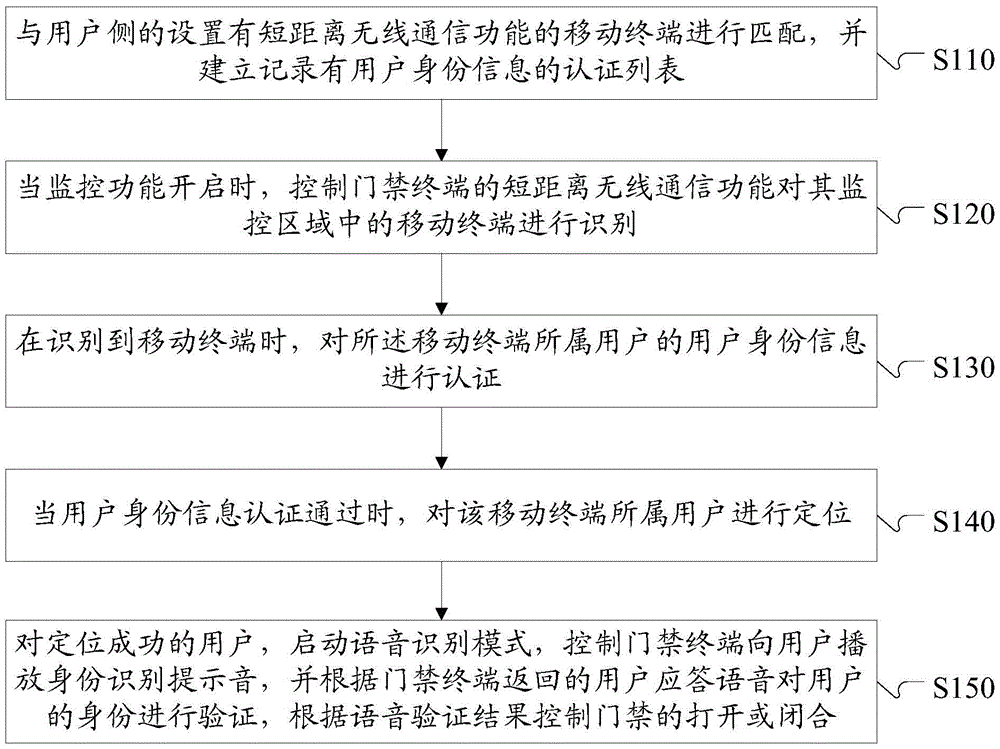
[0057]This embodiment provides an access control monitoring method suitable for a controlled area with multiple rooms, where each room in the controlled area is provided with an access control terminal.
[0058] figure 1 The flow chart of the access control monitoring method provided by this embodiment, such as figure 1 as shown, figure 1 The methods in include:
[0059] S110, matching with a mobile terminal equipped with a short-distance wireless communication function on the user side, and establishing an authentication list in which user identity information is recorded.
[0060] Short-range wireless communication technologies mainly include Bluetooth Low Energy (BLE), ZigBee, Near Field Communication (NFC) and Wireless Local Area Networks (WLAN). Due to the extensive application of BLE technology, such as mobile phones The BLE function on mobile devices such as mobile devices and wristbands, this embodiment preferably uses the BLE function of the mobile device to authen...
Embodiment 2
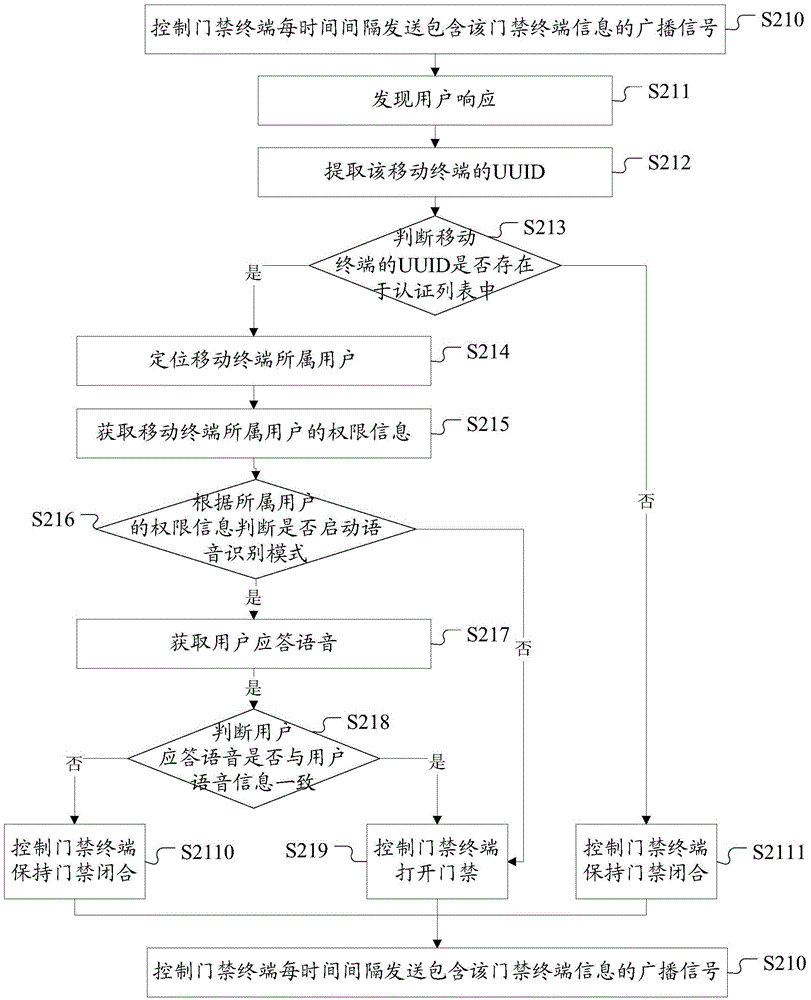
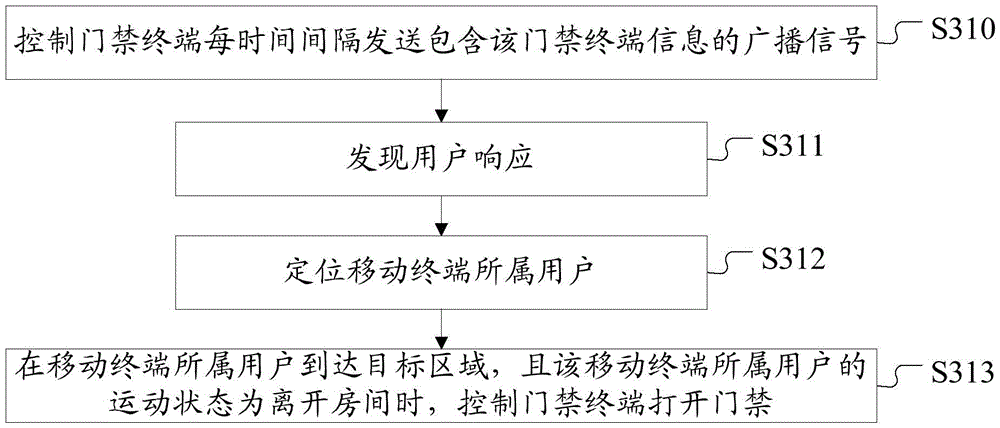
[0101] This embodiment adopts the access control monitoring method in the first embodiment to control the access control of the access control terminal.
[0102] In this embodiment, when controlling the opening and closing of the access control of the access control terminal, the entry of the user identity is completed first. That is, by matching with a mobile terminal equipped with a short-distance wireless communication function on the user side, an authentication list recording user identity information is established to realize user identity entry.
[0103] It should be noted that the user identity information in this embodiment includes an identification code uniquely identifying the mobile terminal, user voice information, and user authority information, wherein the identification code of the mobile terminal is the UUID of the mobile terminal.
[0104] The monitoring method of the access control monitoring system of the present embodiment to the access control terminal is ...
Embodiment 3
[0130] Based on the same technical idea as that of Embodiment 1 or Embodiment 2, this embodiment provides an access control monitoring system, which is suitable for a controlled area with multiple rooms.
[0131] Figure 4 A schematic diagram of the composition and structure of the access control monitoring system provided in this embodiment, such as Figure 4 As shown, the access control monitoring system in the present embodiment includes an access control terminal 40 and an access control monitoring server 41 arranged in each room;
[0132] The access control monitoring server 41 is used to complete the entry of user identity, interact with the data of each access control terminal and control each access control terminal;
[0133] The access control terminal 40 is used to play broadcast information to the environment, play prompts to the user under the control of the access control monitoring server 41, and perform data interaction with the access control monitoring server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com