Access group-based privacy protection-supporting access authorization method
A technology of privacy protection and access group, which is applied in the field of network privacy protection technology and access control, and can solve problems such as inflexible access policies and inability of visitors to join access groups independently
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings.
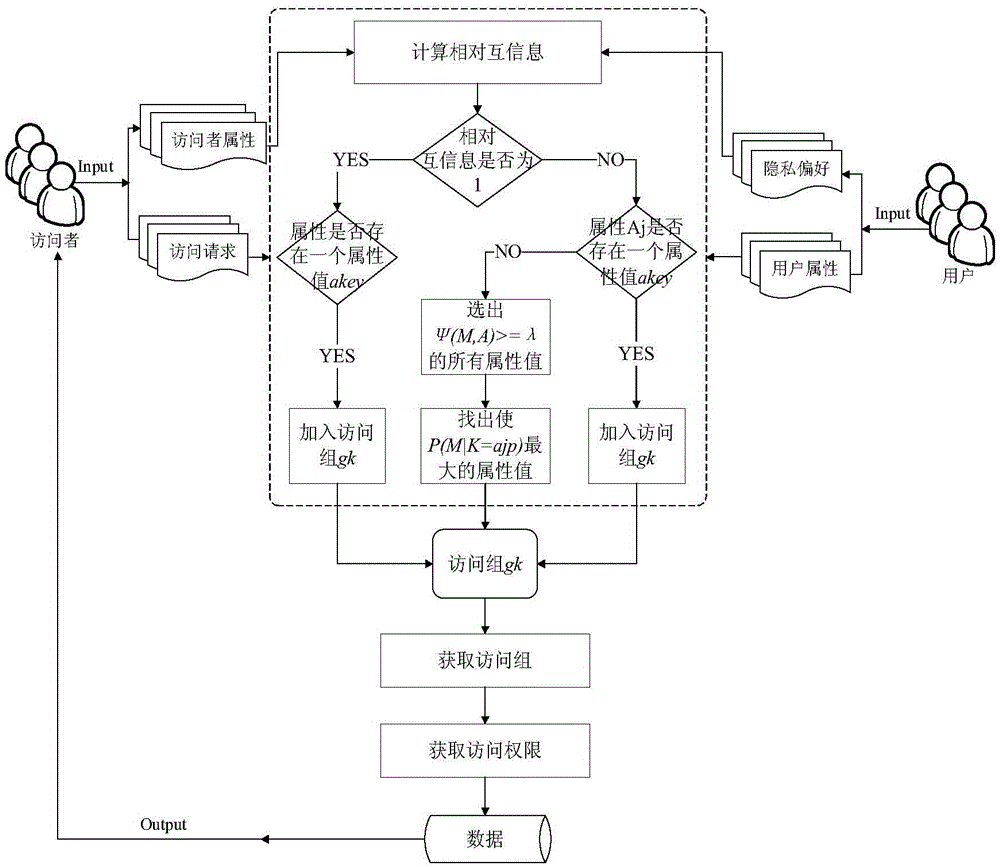
[0048] The relevant concepts and specific descriptions of an access authorization method based on access groups that support privacy protection are given below:
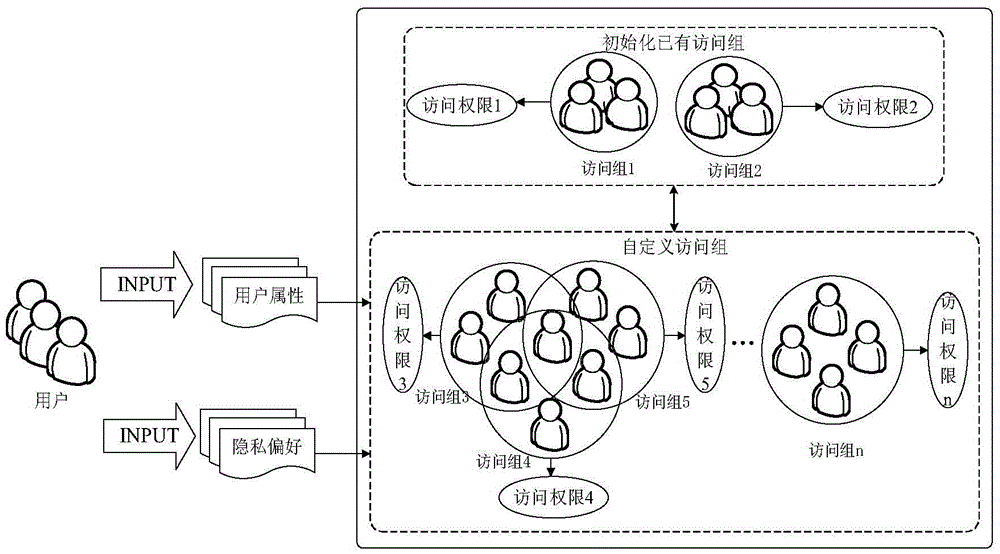
[0049] (1) User: refers to the person who creates, publishes and manages private data on the Internet. For example, the owner of personal data such as "small videos", "mobile phone photo albums" and "personal status" in WeChat Moments. During the privacy setting process, they have the right to create different access groups according to their own privacy preferences.
[0050] (2) Visitor: refers to a person who can access other user data on the Internet. If a user discloses his data on the Internet, anyone can become a visitor of his data; if a user only discloses part of his data, only visitors who meet the relevant access control permissions can access the data. Use V to repr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com