File encryption system based on shadow file
A shadow file and file encryption technology, applied in the field of information security, can solve the problems of low memory utilization and file access efficiency, improve memory utilization and file access efficiency, and avoid frequently emptying the cache
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
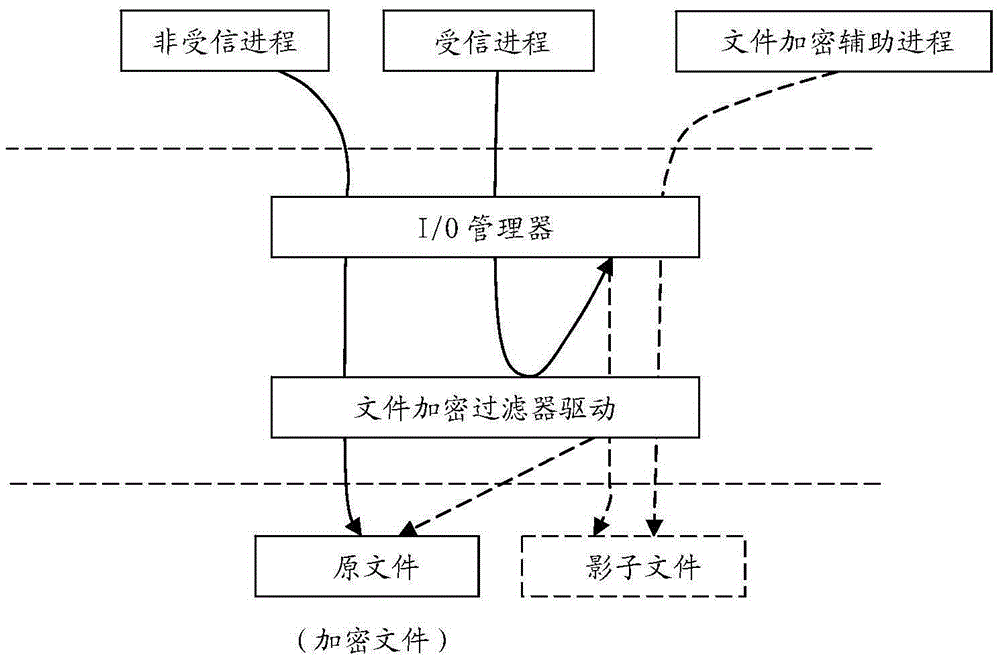
[0032] The specific implementation of the present invention will be described below. figure 1 It is a system structure diagram of the present invention.
[0033] The file encryption filter driver can be developed by using Windows file filter driver (filterdriver) or micro-filter driver (mini-filterdriver) technology.
[0034] It is a mature technology to judge trusted process and untrusted process by using Windows file filter driver or minifilter driver, so it will not be described here.
[0035] For file redirection, you can use the reparsepoint function of Windows file I / O (see the simrep.c code in the WDK).
[0036] A technical scheme that can be adopted for the file path of the shadow real image file is: temporary file directory name\file path of the original file. Here, the file path of the original file is the complete path of the original file to be opened or created by the program process, including the file where the file is located. Disk (Here, the file disk indica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com