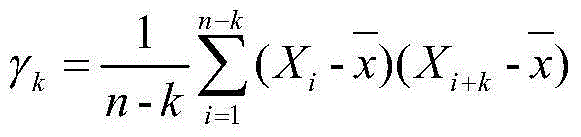Attack behavior detection method based on flow abnormity and feature analysis
A feature analysis and traffic anomaly technology, applied in the field of network security, can solve the problems of low interception attack efficiency, inability to prevent unknown vulnerability attacks, etc., and achieve the effect of avoiding volume increase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
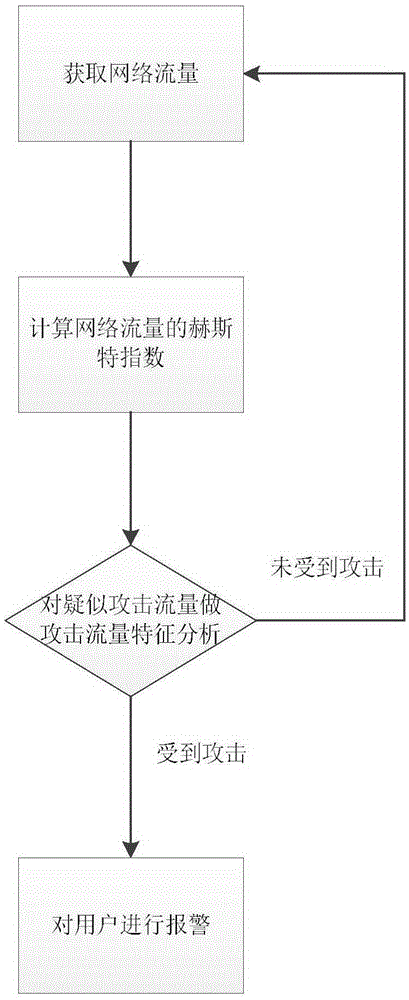
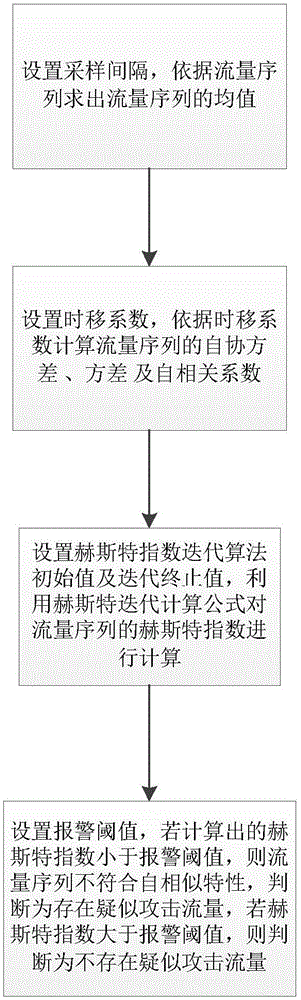
[0021] refer to figure 1 , the implementation steps of the present invention are as follows:
[0022] Step 1, get network traffic.
[0023] At present, there are many ways to obtain network traffic, such as firewall hooks, divertsocket and NPF-driven interception methods, etc. Among them, the firewall hook method and divertsocket method are both intercepting data packets at the IP layer of the TCP / IP protocol stack and performing Traffic statistics, because these data packets pass through part of the protocol stack, their data integrity cannot be guaranteed, and the interception method based on the NPF driver can directly intercept the data packets on the physical link and perform traffic statistics, so this example uses Based on the NPF-driven Windows network underlying access tool winpcap to perform network traffic statistics, the implementation steps are as follows:
[0024] 1a) Use winpcap to open the network adapter A that needs to be detected, set the statistical mode ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com